Users Online
· Members Online: 0
· Total Members: 188
· Newest Member: meenachowdary055
Forum Threads
Latest Articles
Articles Hierarchy
Skill 4.1: Design Azure App Service Web Apps Part 2
Skill 4.1: Design Azure App Service Web Apps Part 2
Configure Web App settings
Azure Web Apps provide a comprehensive collection of settings that you can adjust to establish the environment in which your web application runs, as well as tools to define and manage the values of settings used by your web application code. You can configure the following groups of settings for your applications:
![]() Application type and library versions
Application type and library versions
![]() Load balancing
Load balancing
![]() Slot management
Slot management
![]() Debugging
Debugging
![]() App settings and connection strings
App settings and connection strings
![]() IIS related settings
IIS related settings
To manage Web App settings follow these steps:
-
Navigate to the blade of your web app in the portal accessed via https://portal.azure.com.
-
Select the Application settings tab from the left navigation pane. The setting blade appears to the right.
-
Choose from the general settings required for the application:
-
Choose the required language support from .NET Framework, PHP, Java, or Python, and their associated versions.
-
Choose between 32bit and 64bit runtime execution.
-
Choose web sockets if you are building a web application that leverages this feature from the browser.
-
Choose Always On if you do not want the web application to be unloaded when idle. This reduces the load time required for the next request and is a required setting for web jobs to run effectively.
-
Choose the type of managed pipeline for IIS. Integrated is the more modern pipeline and Classic would only be used for legacy applications (Figure 4-9).
-
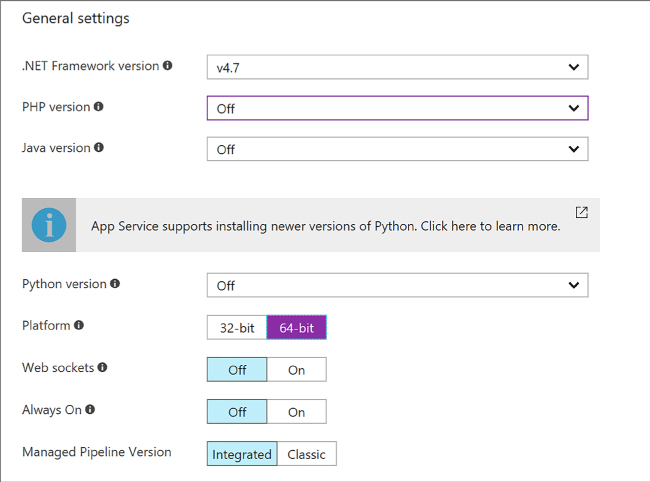
FIGURE 4-9 General settings section for application settings
-
Choose your setting for ARR affinity (Figure 4-10). If you choose to enable ARR affinity your users will be tied to a particular host machine (creating a sticky session) for the duration of their session. If you disable this, your application will not create a sticky session and your application is expected to support load balancing between machines within a session.

FIGURE 4-10 ARR affinity settings
-
When you first create your web app, the auto swap settings are not available to configure. You must first create a new slot, and from the slot you may configure auto swap to another slot (Figure 4-11).

FIGURE 4-11 Auto Swap settings
-
Enable remote debugging (Figure 4-12) if you run into situations where deployed applications are not functioning as expected. You can enable remote debugging for Visual Studio versions 2012, 2013, 2015, and 2017.
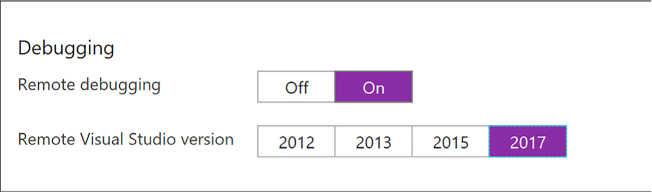
FIGURE 4-12 Remote debugging settings for the web app
-
Configure the app settings required for your application. These app settings (Figure 4-13) override any settings matching the same name from your application.
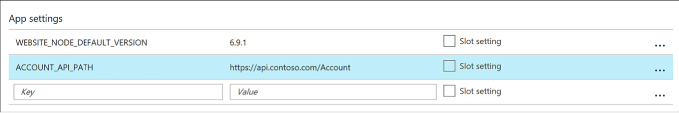
FIGURE 4-13 Application settings
-
Configure any connection strings for your application (Figure 4-14). These connection string settings override any settings matching the same key name from your application configuration. For connection strings, once you create the settings, save, and later return to the application settings blade; those settings are hidden unless you select it to show the value again.
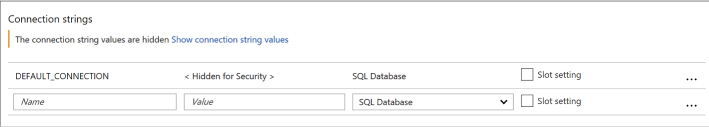
FIGURE 4-14 Connection string settings
-
Configure IIS settings related to default documents, handlers, and virtual applications and directories required for your application (Figure 4-15). This allows you to control these IIS features related to your application.
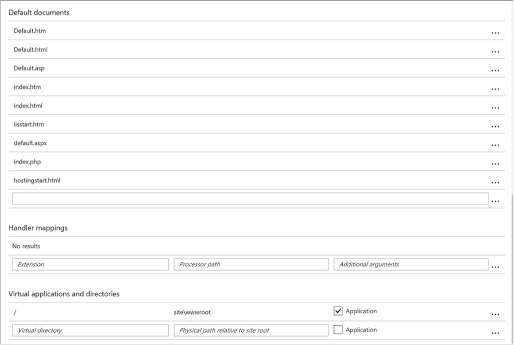
FIGURE 4-15 IIS settings
Note: Access to App Settings
App settings are represented as name-value pairs made available to your web application when it starts. The mechanism you use to access these values depends on the web platform in which your web application is programmed. If your application is built using ASP.NET 4.6, you access the values of app settings just as you would access the AppSettings values stored in web.config. If your web application is built using ASP.NET Core, you access the values as you would in your appsettings.json file. If your web application is built using another supported web platform, such as Node.js, PHP, Python, or Java, the app settings are presented to your application as environment variables.
Note: Accessing Connection Strings
Like app settings, connection strings represent name-value pairs, but they are used specifically for settings that define the connection string to a linked resource (typically a database) such as a SQL database, a SQL server, MySQL, or some other custom resource. Connection strings are given special treatment within the portal, beyond that offered to app settings, in that you can specify a type for the connection string to identify it as a SQL server, MySQL, a SQL database, or a custom connection string. Additionally, the values for connection strings are not displayed by default, requiring an additional effort to display the values so that their sensitive data is not displayed or editable until specifically requested by the portal user.
Configure Web App certificates and custom domains
When you first create your web app, it is accessible through the subdomain you specified in the web app creation process, where it takes the form <yourwebappname>.azurewebsites.net. To map to a more user-friendly domain name (such ascontoso.com), you must set up a custom domain name.
If your website will use HTTPS to secure communication between it and the browser using Transport Layer Security (TLS), more commonly (but less accurately) referred to in the industry as Secure Socket Layer (SSL), you need to utilize an SSL certificate. With Azure Web Apps, you can use an SSL certificate with your web app in one of two ways:
![]() You can use the “built-in” wildcard SSL certificate that is associated with the *.azurewebsites.net domain.
You can use the “built-in” wildcard SSL certificate that is associated with the *.azurewebsites.net domain.
![]() More commonly you use a certificate you purchase for your custom domain from a third-party certificate authority.
More commonly you use a certificate you purchase for your custom domain from a third-party certificate authority.
Note
There are multiple types of SSL certificates, but the one you choose primarily depends on the number of different custom domains (or subdomains) that the certificate secures. Some certificates apply to only a single fully qualified domain name (sometimes referred to as basic certs), some certificates apply to a list of fully qualified domain names (also called subjectAltName or UC certs), and other certificates apply across an unlimited number of subdomains for a given domain name (usually referred to as wildcard certs).

