Users Online
· Members Online: 0
· Total Members: 188
· Newest Member: meenachowdary055
Forum Threads
Latest Articles
Articles Hierarchy
#CompTIA Security+ 501 exam Chapter10 Responding to Security Incidents Part 1
Responding to Security Incidents
In this chapter, we will be looking at incident response, particularly with regard to the collection of volatile evidence for forensic analysis.
We will cover the following exam objectives in this chapter:
-
Given a scenario, use appropriate software tools to assess the security posture of an organization: Protocol analyzer, network scanners, rogue system detection, network mapping, wireless scanners/cracker, password cracker, vulnerability scanner, configuration compliance scanner, exploitation frameworks, data sanitization tools, steganography tools, honeypot, backup utilities, banner grabbing, command-line tools, ping, netstat, tracert, nslookup/dig, ARP, ipconfig/ip/ifconfig, tcpdump, Nmap, and netcat
-
Given a scenario, analyze and interpret the output from security technologies: HIDS/HIPS, antivirus, file integrity check, host-based firewall, application whitelisting, removable media control, advanced malware tools, patch management tools, UTM, DLP, data execution prevention, and web application firewalls
-
Given a scenario, follow incident response procedures: Response plan, documented incident types/category definitions, roles and responsibilities, reporting requirements/escalation, cyber incident response teams, exercise, incident response process, preparation, identification, containment, eradication, recovery, and lessons learned
-
Summarize basic concepts of forensics: Order of volatility, chain of custody, legal hold, data acquisition, capture system image, network traffic and logs, capture video, record time offset, take hashes, screenshots, witness interviews, preservation, recovery, strategic intelligence/counterintelligence gathering, active logging, and tracking man hours
-
Explain disaster recovery and continuity of operations concepts: Backup concepts, differential, incremental, snapshots, and full, incremental, incremental backups and snapshots.
Incident response procedures
There are many different incidents, and each of them requires a different incident response plan. For example, dealing with a flood or the failure of a server's hardware is totally different. The first stage of an incident response plan is to collect any volatile evidence so that the source of that incident can be identified, followed by containment of the incident itself, followed by the recovery procedures. Let's look in more detail at the components required to make incident response successful:
-
Documented incident types: We should already have documentation about each incident that shows the steps required for a positive response. These types of incidents are laid down under different category definitions.
-
Category definitions: Your company should have an outline plan for dealing with most incidents ranging from the following categories:
-
Unauthorized access
-
Loss of computers or data
-
Loss of availability
-
Malware attack
-
DDoS attack
-
Power failure
-
Natural disasters such as floods, tornados, hurricanes, and fires
-
Cyber security incidents
-
-
Roles and responsibilities: When an incident occurs, it is important to get an Incident Response Team together to deal with the incident, and these include the following roles:
-
Incident response manager: A top level manager takes charge
-
Security analyst: Technical support to the incident
-
IT auditor: Check that the company is compliant
-
Risk analyst: Evaluates all aspects of risk
-
HR: Sometime employees are involved in the incident
-
Legal: Gives advice and makes decisions on legal issues
-
Public relations: Deals with the press to reduce the impact
-
-
Reporting requirements/escalation: Depending on the incident itself, you may have to report it to the authorities and/or your customer base should their credit card details be stolen. Your Help Desk must identify the incident response plan that deals with each particular incident so that it can be escalated to the team that has the skill set to deal with it.
-
Cyber incident response teams: Cybercrime is very prominent in today's world. It ranges from a single criminal trying to steal some money to organized criminal gangs through to advanced persistent threats, sometimes from national states. The Cyber Incident Response Team must move rapidly and have up-to-date training for the variety of incidents that they may face, and may have to use third-party specialists in some aspect of cybercrime.
-
Incident response exercises: Companies will need to invoke each incident response plan periodically, very similar to fire drills that have been carried out for many years. This will allow your different incident response teams to gain the skill set to deal with future incidents.
Incident response process
While responding to an incident, the following processes are followed:
-
Preparation: The preparation phase is where the different incident response plans are already written and kept up to date.
-
Identification: Once an incident has occurred, it is important that the appropriate incident response plan is invoked and the personnel needed are notified.
-
Containment: When dealing with the incident, it is important that the volatile evidence is secured and then we prevent the incident from spreading any further.
-
Eradication: In the eradication phase, we want to destroy the source of the incident. For example, if it is a virus, we want it totally removed.
-
Recovery: In the recovery phase, we are getting the company back to an operational state, hopefully within the RPO. For example, imaging machines and restoring data within one day.
-
Lessons learned: Lessons learned is a detective phase where we pull together all of the facts and plan to prevent a re-occurrence in the future. Failure to carry this out will lead to a re-occurrence. The incident response process is shown here:
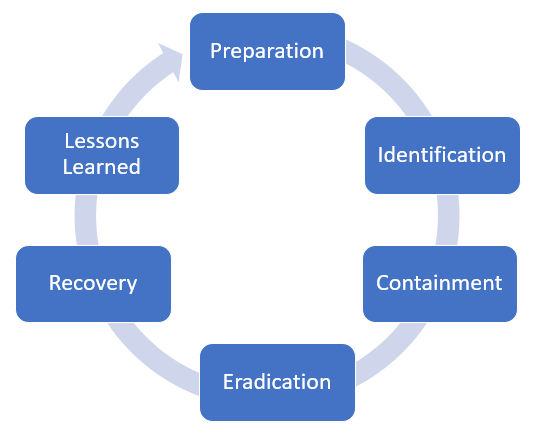
Figure 1: Incident response process
Exam tip:
Lessons learned is a detective control where the incident is reviewed and changes are made to prevent it happening again.
Understanding the basic concepts of forensics
Forensics is used by the police when they are investigating crimes and need to find as much evidence as they can to secure a conviction. We will be looking at computer and web-based attacks. There are many different components, therefore we will look at each of these in turn:
-
Order of volatility: You are a fireman and you arrive at a house and you can only save one person at a time and there are two items inside. The first is a snowman, and the second is a rib of beef; the fireman now has the dilemma, which one shall he choose? He saves the snowman first as it is melting and has decided to let the rib of beef cook some more so that the firemen can have a nice supper! So, when we look for order of volatility, we are looking to secure the most perishable evidence first. We do not try and stop the attack until we have secured the volatile evidence so that the source can be identified. This is known as order of volatility:
-
Example 1—web-based attack: An attacker is attacking the company website and the Security Team are trying to capture the network traffic to find the source of the attack. This is the most volatile evidence.
-
Example 2—attack inside a computer: When someone has attacked your computer, you need to capture the evidence in accordance with the order of volatility:
-
CPU cache: Fast block of volatile memory used by the CPU
-
Random Access Memory (RAM): Volatile memory used to run applications
-
Swap/page file: Used for running applications when there is no RAM left
-
Hard drive: Data at rest for storing data
-
-
Example 3—removable storage drive attached to a computer/server: Someone has left a USB flash drive plugged into your file server. When it is in use, the programs such as Word are launched in RAM, so we would capture the volatile memory first.
-
Example 4—command-line tools: You need to know which command-line tool provides information that could disappear if you reboot the computer, and that would be netstat. With netstat -an, it shows the listening and established ports. If you reboot the computer, all of the established connections will be lost.
-
Exam tip:
Order of volatility is collecting the most perishable evidence first.
Five minute practical
Open up the command prompt on your computer, and type netstat -an. You should now see the listening and established ports; count them, and write the numbers down. Run the command shutdown /r /t 0 to immediately reboot the machine. Log back in, go to the command prompt, and run netstat -an; what is the difference? You will see that you have lost information that could have been used as evidence:
|
Volatile evidence summary |
|||
|
Web-based attack |
Computer attack |
Removable drive |
Command line |
|
Capture network traffic |
CPU cache then RAM |
Volatile memory using RAM |
Netstat-an |
Exam tip:
Capturing the network traffic is the first step in remote or web-based attacks so that you can identify the course.
-
Chain of custody: The Chain of custody starts when the evidence has been collected, bagged, and tagged. It lists the evidence and who has handled it along the way. For example, Sgt Smith handed 15 kg of cocaine to Sgt Jones following a drugs raid. However, when it is handed into the Property Room, 1 kg is missing. In this event, we would need to investigate the chain of custody and in this scenario, Sgt Jones would be liable for the loss. The chain of custody is shown here:
|
Date |
From |
To |
Evidence |
|
1st August |
Sgt Smith |
Sgt Jones |
15 kg cocaine |
|
2nd August |
Sgt Jones |
Property room |
14 kg cocaine |
-
Example 1—missing entry on the chain of custody document: On Monday 15, laptops were collected by the System Administrator. The next day, the system administrator passes them on to the IT manager. On Wednesday, the IT Director presented the 15 laptops as evidence to the court. The judge looks at the chain of custody document and notices that there was no formal handover between the IT Manager and the IT Director. With the handover missing, the judge wants to investigate the chain of custody.
-
Example 2—evidence leaves the detective's possession: The FBI arrest a known criminal and collect 43 hard drives that they bag and tag, before placing them in two bags. They arrest the criminal and take him from Arizona to New York. One detective is handcuffed to the criminal while the other carries the two bags. When they arrived at check-in, the airline clerk tells them that the carry-on bags are more than the 8 kgs allowance, and therefore they are too heavy and need to go in the hold. The detective does this, but locks the suitcases to prevent theft. Because the evidence is not physically in their possession at all times, the chain of custody is broken as there is a chance for someone working for the airline to swap out any of the evidence. Therefore, they cannot prove to the court that the evidence has been intact at all times.
Exam tip:
Chain of custody must show who has handled the evidence until it is presented to the courts. The evidence must not leave the possession of the person who has signed for it, otherwise it needs to be investigated.
-
Legal hold: Legal hold is the process of protecting any documents that can be used in evidence from being altered or destroyed. Sometimes, this is also known as litigation hold.
Example: Dr. Death has been prescribing new drugs to patients in a large hospital who have been dying. An auditor has been sent to investigate the possibility of foul play, and then following the audit, the FBI are notified. The doctor has been emailing a pharmaceutical company that has been supplying the drugs for a trial. The FBI does not want the doctor to be alerted, so they have the hospital's IT Team put his mailbox on legal hold. When the mailbox is on legal hold, the mailbox limit is lifted; the doctor can still send and receive email, but cannot delete anything. This way, he is not alerted to the fact that he is under investigation.
-
Data acquisition: This is the process of collecting all of the evidence from devices such as removable media, such as USB flash drives, cameras, and computers, as well as data in paper format such as letters or bank statements. The first step in data acquisition is to collect the volatile evidence so that it is secured. The data must be bagged and tagged, and included in the evidence log.
Exam tip:
Recording the time offset is used for time normalization across multiple time zones.
-
Record time offset: When we collect evidence from computers, we should record the time offset. This is the regional time so that in a multinational investigation we can put them into a time sequence—this is known as time normalization.
Example: The police in three separate countries are trying to identify where the data started from in a chain, then who handled the data along the line. They have the following information of when it was first created:
New York: Created 3 a.m
-
-
London: Created 4 a.m
-
Berlin: Created 4.30 a.m
-
Without recording the time offset, it looks as if it started off in New York, but if we apply regional times, when it is 4 a.m. in London, the time in New York is 11 p.m. the day before, so it cannot be New York. When it is 4.30 a.m. in Berlin, it is only 3.30 a.m. in London, therefore, it originated in Berlin. However, with the record time offset, it looked the least unlikely before the time offset was applied.
-
Forensic copy: If we are going to analyze removable data that we have acquired, we would first of all take a forensic copy and keep the original data intact. We would then use the copy to analyze the data so that we keep the original data unaltered, as it needs to be used in its original state and presented as evidence to the courts.
-
Capture system image: When the police are taking evidence from laptops and desktops, they take a complete system image. The original image is kept intact and the system is analyzed to find evidence of any criminal activity.
Exam tip:
Taking a system image or a forensic copy of a hard drive is the first stage in forensic investigation.
-
Screenshots: You may also take screenshots of applications or viruses on the desktops and keep them as evidence. A better way of doing this would be to use a modern smartphone that would geotag the evidence.
-
Taking hashes: When either the forensic copy or the system image is being analyzed, the data and applications are hashed at the beginning of the investigation. At the end, it is re-hashed and should match the original hash value to prove data integrity. If, during the investigation, the officer believes that he has made a mistake, he re-hashes the data, and if it has been altered, he should note it down and then carry out the investigation as best as he can.
Exam tip:
Hashing data before and after investigation can prove data integrity.
-
Network traffic and logs: When investigating a web-based or remote attack, we should first capture the volatile network traffic before stopping the attack. This will help us identify the source of the attack. In addition to this, we should look at different log files from the firewall, NIPS, NIDS, and any server involved. If we use a SIEM system, this can help collate these entries and give a good picture of any attack.
Example: Your company uses an account lockout of three attempts. If an attacker tries to log in once to three separate computers, each computer would not identify it as an attack, as it is a single attempt on each computer, but a SIEM system would pick up these attempts as three failed login attempts and alert the administrators in real time.
-
Capture video: A good source of evidence can be CCTV traffic to help identify the attackers and the time the attack was launched. This can be vital in apprehending the suspects.
-
Witness statements: The police may also take witness statements to try and get a picture of who was involved and maybe then use photofits so that they can be apprehended.
-
Preservation: Data needs to be preserved in its original state so that it can be produced as evidence in court. This is why we take copies and analyze the copies so that the original data is not altered and is pristine. Putting a copy of the most vital evidence in a WORM drive (write once, read many) will prevent any tampering with the evidence, as you cannot delete it from a WORM drive.
-
Recovery: When the incident has been eradicated, we may have to recover the data from a backup, or a faster method would be a hot site that is already up and running with data less than one hour old. We may also have to purchase additional hardware, if the original hardware was damaged during the incident.
Exam tip:
Re-imaging computers and restoring data is part of the recovery phase.
-
Strategic intelligence/counterintelligence gathering: This is where different governments exchange data about cyber criminals so that they can work together to reduce the threat. It is also possible for companies who have suffered an attack to log as much information as they can and have a third party who specializes in incident response to help them find a way to prevent reoccurrence.
-
Active logging: To track incidents, we need to be actively monitoring and actively logging changes to patterns in our log files, or traffic patterns in our network. Installing a SIEM system can help collate all entries in the log files, ensuring that duplicate data is not used so that a true picture can be taken. Alerts based on certain triggers can be set up on our SIEM system so that we are notified as soon as the event happens.
-
Track man hours: Companies should track man hours to realize the costs incurred during incidents. This may make them realize that they may have to spend more money on resources to protect against incidents.
Software tools to assess the security posture of an organization
Security teams are constantly under attack from cyber criminals and threat actors, and therefore they need to be able to use a mixture of different security tools so that they can identify attacks before they have a chance to cause grave damage to the business. We will now look at each of these tools to see the benefits of each:
-
Protocol analyzer: A protocol analyzer, such as Wireshark, can capture the traffic flowing through the network, including passwords in clear text and any commands being sent to network-based applications. A protocol analyzer can identify the three-way handshake between two hosts and the verbs being used with applications, such as the HTML GET verb for fetching a web page. But if we see the PUT or HEAD verb, we could recognize this as an attack.
Example: Someone within the company is not working as they should be but has been surfing the web, and the manager has called you in as the security administrator to gather evidence. You decide that a protocol analyzer or packet sniffer is the best tool to track the information. You run a Wireshark session and capture the visits to the NFL website. When you analyze the trace, you notice that the request is using the HTTP GET verb. This is the request for a page on www.nfl.com. When we drill down further into the analysis of the request, we are looking at a page with an article, Josh Hobbs and Mike Glennon drawing trade interest, as shown here:
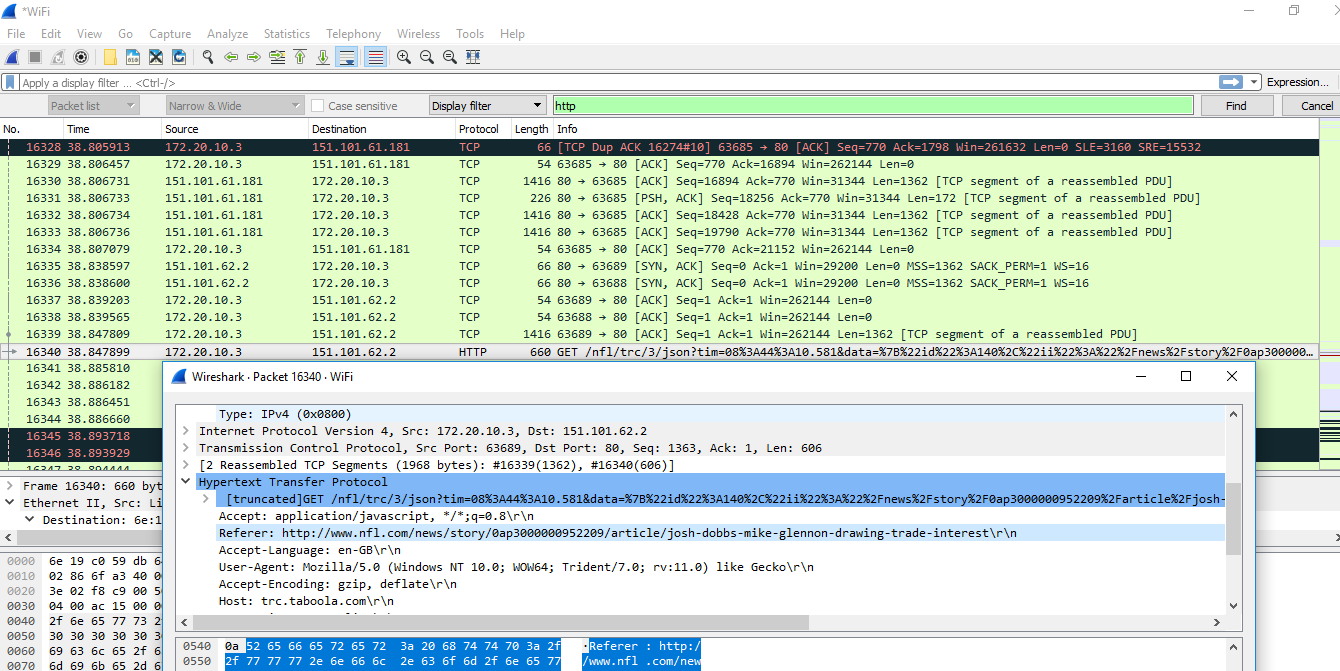
Figure 2: Protocol analyzer
Exam tip: A protocol analyzer can detect the operating system of a host and commands being sent across the network to any applications.
-
Network scanners: A network scanner can be used to map out your network for you so that you can see the network devices and can also show performance data and packet loss—see the following screenshot:
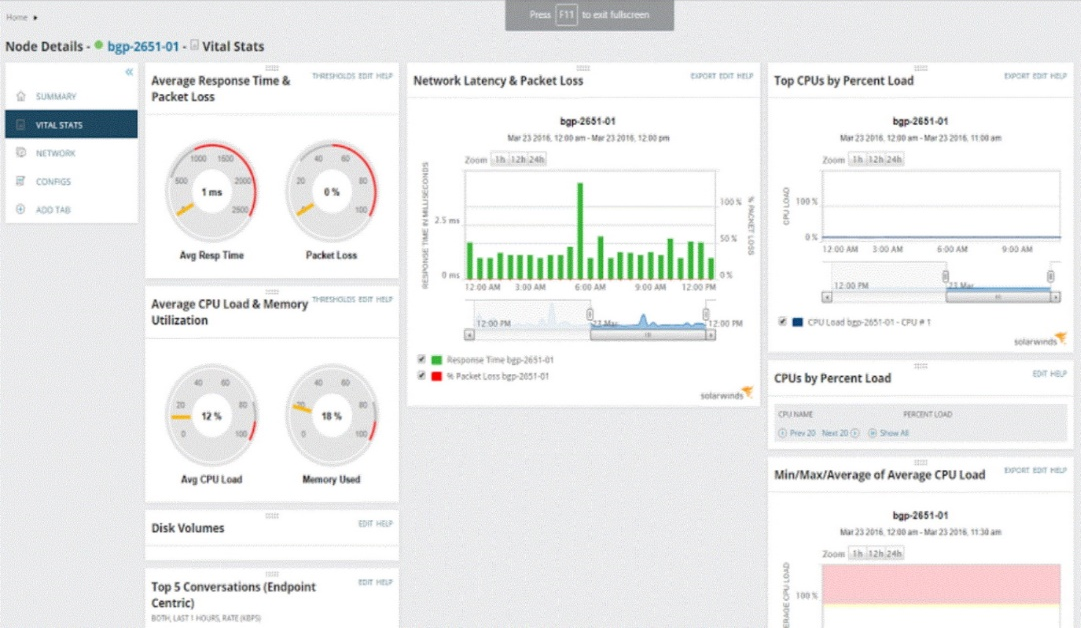
Figure 3: Network scanner
-
Rogue system detection: Rogue system protection tools, such as those made by McAfee, can detect rogue and unmanaged devices on your network and help you protect your network. If we also adopt 802.1x managed switches, we can prevent these devices from connecting to your network.
-
Network mapping: A network mapper can show all the devices on your network along with their operating systems and the services running on them. These tools will be banned from use on a corporate network because of the vast amount of information that can be gathered.
-
Wireless scanners: A wireless scanner is like a protocol analyzer for wireless networks. They can capture packets going to the wireless router. Embedded in the wireless packets is the name of the wireless network SSID. This means that even if you disable SSID broadcasting, the SSID can still be discovered. You could also use a SSID de-cloak device to find the SSID.
Exam tip:A network mapper can identify the operating systems and services running on a computer.
-
Wireless crackers: Tools, such as Fern Wi-Fi Cracker, are written using the Python programming language and can be used to crack and recover the WEP/WPA and WPS keys.
-
Password cracker: Password crackers are tools that can perform the most common Dictionary, Brute-Force, and Rainbow table attacks. They can also use guessing, where they are using words such as qwerty, password, or 12345, or Spidering, where information about the company is used in passwords. This information can be found on the company's social media websites, for example, Facebook or Twitter. This information can then be turned into words for password cracking.
-
Vulnerability scanner: There are two types of vulnerability scanner:
-
Credentialed: This is basically running as an administrator and can find vulnerabilities and can even audit files and permissions
-
Non-credentialed: This is the most basic, running with limited permissions where it is scanning the hosts to find missing patches
-
The vulnerability scanner is passive and does not cause damage to the systems. An example is Microsoft Baseline Analyzer—see the following screenshot. Although the computer was fully patched, as it was a credentialed scan, it gave me some information:
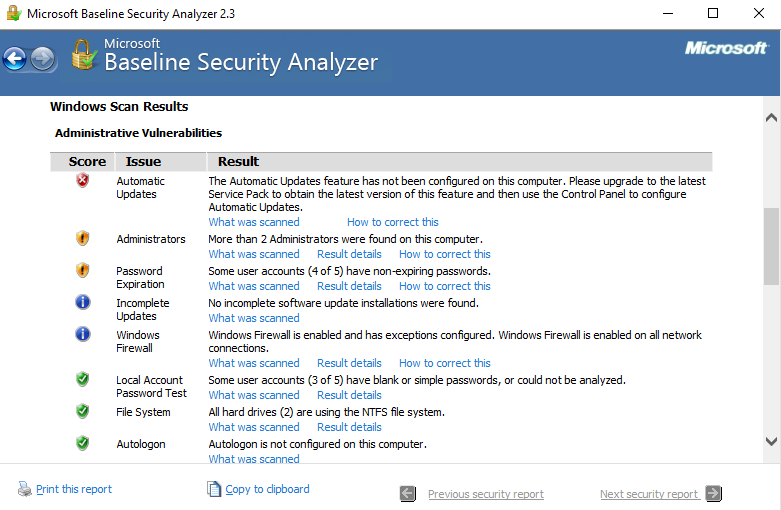
Figure 4: Credentialed vulnerability scan
Exam tip:A credentialed vulnerability scanner can audit files and examine permissions.
-
Configuration compliance scanner: Compliance scanning focuses on the configuration settings (or security hardening) being applied to a system in accordance with a compliance framework. This means we are ensuring all of the settings of a system are configured properly.
-
Exploitation frameworks: Exploitation framework tools such as the open source Metasploit Framework can develop and execute exploit code against a remote target computer. This can be used to harden your IT systems before they are attacked.
-
Data sanitization tools: When you delete data and then use the format command to reformat your hard drive, professional packages exist to recover the data depending on how old it is, as it deteriorates over time. Using professional data sanitization tools ensures that this data will never ever be recovered.
-
Steganography tools: Steganography tools can be used for encoding and decoding images, for example, JPEGs, sound files such a WAV files such as an audio files. You can hide data inside a file, an audio, video, or image file.
Exam tip:A compliance scanner can ensure that all of the settings on computers are compliant and as they should be.
-
Honeypot: A honeypot is a website made to look like a legitimate website with lower security to distract attackers away from the legitimate website. Additionally, the Security Team can monitor the method that the attackers are using so that they can prevent these attacks in the futures.
Backup utilities
Backing up data is very important so that if the systems fail, then a copy of the data can be obtained from a previous backup. A company cannot put a cost on its most critical data, and if it was to lose it, this would cause grave damage to the company, especially if the data was the Financial, or Research and Development Department, which make new prototypes of products.
There are various ways that we can back up the data—we can take snapshots of virtual machines, back up to a network, back up to tape, or a removable device. Let's look at these in turn.
Exam tip:A honeypot can be used to track the attack methods being used against websites.
-
Creating a snapshot: When using virtualization, a snapshot can be created so that the virtual machine can be rolled back to a previous state. This is the fastest backup to recover from as it can be done in a matter of seconds.
-
Network location: A backup can be performed to a file share on a server in the network. The server would have some sort of RAID redundancy or the storage would be part of a SAN.
-
Backing up to tape: A backup can be backed up to magnetic tape, and this would be the slowest form of restore. Additionally, a copy of the backup tape can be stored offsite in case the company has a fire and burns down.
Backup types
There are various types of backups and these are full, incremental, and differential. Let's look at these in turn:
-
Full backup: A full backup is a backup of all of your data. However, some companies might only be able to back up all of their data over the weekend, so they will use either an incremental or differential midweek.
-
Incremental: An incremental backup backs up the data since the last full backup or the last incremental. An incremental backup will need the full backup from the start and then all of the incremental backups.
-
Differential: A differential backup will back up the data since the last full backup. The problem with this if we have a full backup at the start of the week and then a differential backup daily each day, they will be progressively larger each day. A differential backup will always be two tapes, the full backup from the start and the latest differential.
Example: We will compare the different types of backup. We will start the backup each day, but will suffer data loss on the Friday, and we will see how many tapes we need to recover our data. Our full backup will be 50 GB of data and each day we will produce 5 GB of data. You can see this from the following chart, how many tapes are needed for each type of backups to recover your data:
Full: The latest full backup is 65 GB; each day we back up more and more
-
-
Incremental: Starts off with the full backup but needs all of the incremental backup
-
Differential: Starts off with the full backup but needs the latest differential backup:
-
|
Backup |
Mon |
Tues |
Wed |
Thurs |
Fri |
Tapes to recover |
|
Full (F) |
F 50 GB |
F 55 GB |
F 60 GB |
F 65 GB |
X |
F 65 GB thurs |
|
Incremental (I) |
F 50 GB |
I 5 GB |
I 5 GB |
I 5 GB |
X |
F 50 GB Mon 3 X I—tues, wed, thurs |
|
Differential (D) |
F 50 GB |
D 5 GB |
D 10 GB |
D 15 GB |
X |
F 50 GB mon D 15 GB thurs |
Exam tip:Symptoms of steganography is that an image is lighter or a file is larger than it should be.
-
Banner grabbing: Banner grabbing is a technique used to gain information about a remote server and is often used as part of a fingerprinting attack. This could be where you are looking for details on remote systems such as a web server. If you are looking for the patch level of a web server, we would use banner grabbing to collect this information.

