Users Online
· Members Online: 0
· Total Members: 188
· Newest Member: meenachowdary055
Forum Threads
Latest Articles
Articles Hierarchy
#CompTIA Security+ 501 exam Chapter09 Implementing Public Key Infrastructure Part 2
Chapter09 Implementing Public Key Infrastructure Part 2
XOR encryption
The binary operation exclusive OR (XOR) is a binary operand from Boole algebra. This operand will compare two bits and will produce one bit in return:
-
Two bits that are equal: 0
-
Two bits that are different: 1
This is the opposite to binary. For example, we are going to use the word tread in ASCII format and then we are going to insert a key using the word hello so that we can complete an XOR operation. See the following diagram:

Figure 10: XOR
XOR encryption is commonly used with AES, several symmetric ciphers, and a one-time pad.
Key stretching algorithms
The concept of key stretching is to insert a random set of characters to increase the size of the password hash, making it harder for a brute force attack:
-
BCRYPT: Bcrypt is a password hashing algorithm based on the Blowfish cipher. It is used to salt the passwords; a random string is inserted to increase the password length to help protect against rainbow table attacks. It also has an adaptive function where the iteration count can be increased to make it slower, so it remains resistant to attacks even with increasing computation power.
-
PBKDF2: PBKDF2 stores password with a random salt and with the password hash using HMAC; it then iterates, which forces the regeneration of every password and prevents any rainbow table attack.
Cipher modes
There are different cipher modes; most symmetric keys use a block cipher and can encrypt a large amount of data quicker than asymmetric encryption. Let us look at these in turn:
-
Stream cipher: A stream cipher (https://searchsecurity.techtarget.com/definition/cipher) is a method of encrypting text (to produce ciphertext (https://whatis.techtarget.com/definition/ciphertext)) in which a cryptographic key and algorithm (https://whatis.techtarget.com/definition/algorithm) are applied to each binary digit (https://whatis.techtarget.com/definition/bit-binary-digit) in a data stream, one bit at a time. In this mode, only one key is used. It uses symmetric encryption but is not commonly used today as it is easy to crack.
-
Block cipher: A block cipher is where a block of data is taken and then encrypted, for example 128 bits of data are encrypted at a time. This is the method used today as it is much faster than a stream cipher.
Stream versus block cipher analogy
We have two teams of four people who have been tasked with unloading one five-ton lorry full of skittles and placing them in a room on the bottom floor of a building.
There are skittles in boxes and there are skittles which have been placed loose. One of the teams has loose skittles that need to be bagged and the other lorry has boxes of skittles. It is obvious that the team with boxes of skittles will win:
-
Initialization Vector (IV): This is an arbitrary number that can be used along with a secret key for data encryption. This number, also called a nonce, is employed only one time in any session. The IV length is usually comparable to the length of the encryption key or the block of the cipher in use. Sometimes, this is also known as a starter variable.
-
Cipher Block Chaining (CBC): CBC adds XOR to each plaintext block from the ciphertext block that was previously produced. The first plaintext block has an initialization vector (IV) that you XOR; you then encrypt that block of plaintext. See the following diagram:
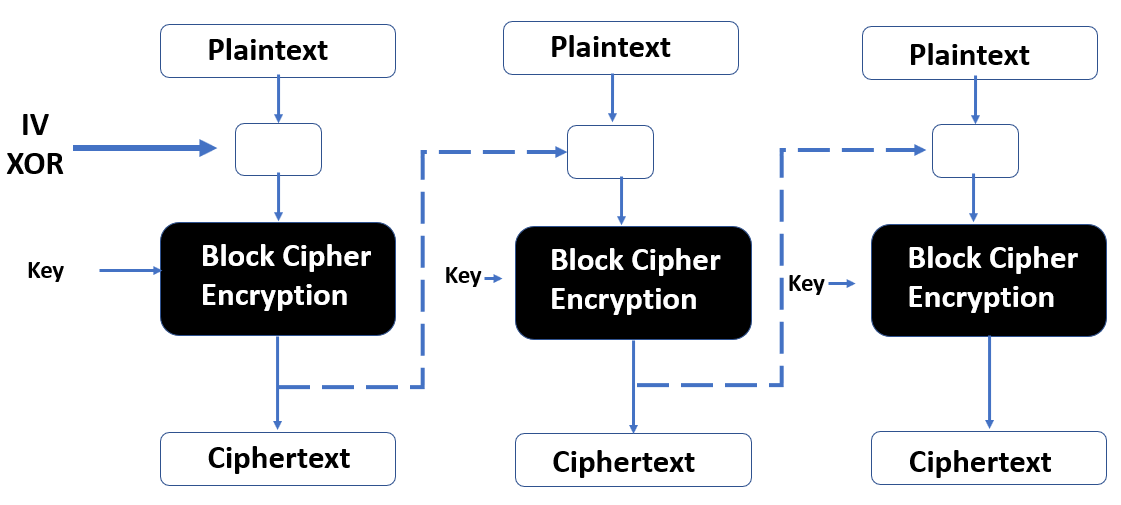
Figure 11: Cipher Block Chaining (CBC)
The next block of plaintext is XOR'd against the last encrypted block before you encrypt this block. When decrypting a ciphertext block, you need the XOR from the previous ciphertext block. If you are missing any blocks, then decryption cannot be done.
-
Electronic Code Book (ECB): ECB replaces each block of the clear text by the block of ciphertext. The same plaintext will result in the same ciphertext. The blocks are independent from the other blocks. CBC is much more secure.
-
Galois/Counter Mode (GCM): This is a block cipher mode of operation that uses universal hashing over a binary Galois field to provide authenticated encryption. It can be implemented in hardware and software to achieve high speeds with low cost and low latency.
-
Counter Mode (CTR): Counter mode turns a block cipher into a stream cipher. It generates the next key stream block by encrypting successive values of a counter rather than an IV.
Hashing and data integrity
Hashing is where the data inside a document is hashed using an algorithm such as a Secure Hash Algorithm version 1 (SHA1) and MD5. This turns the data inside the file into a long text string known as a hash value; this is also known as a message digest.
While you are hashing the same data, if you copy a file and therefore have two files containing the same data, if you hash them with the same hashing algorithm, it will always produce the same hash value. Please look at the following example:
-
Verifying Integrity: During forensic analysis, the scientist takes a copy of the data prior to investigation. To ensure that he has not tampered with it during investigation, he will hash the data before starting and then compare the hash to the data when he has finished. If the hash matches, then we know that the integrity of the data is intact.
-
One-way Function: For the purpose of the exam, hashing is a one-way function and cannot be reversed.
-
HMAC Authentication: In cryptography, a HMAC (sometimes known as either keyed-hash message authentication code or hash-based message authentication code) is a specific type of message authentication code (MAC) involving a cryptographic hash function and a secret cryptographic key. We can have HMAC-MD5 or HMAC-SHA1; the exam provides both data integrity and data authentication.
-
Digital Signature: Digital signatures are used to verify the integrity of an email so that you know it has not been tampered with in transit. The private certificate used to sign the email creates a one-way hash function, and when it arrives at its destination, the recipient has already been given a public key to verify that it has not been tampered with in transit. This will be covered more in-depth later in this book.
Can you read data that has been hashed? Hashing does not hide the data, as a digitally signed email could still be read; it only verifies integrity. If you wish to stop someone reading the email in transit, you need to encrypt it.
-
RIPEMD: This is a 128-bit hashing function. RIPEMD has been replaced by RIPEMD-160, RIPEMD-256, and RIPEMD-320. For the purpose of the exam, you need to know that it can be used to hash data.
Comparing and contrasting basic concepts of cryptography
The most common asymmetric algorithms include the Diffie Hellman, which creates a secure session so that symmetric data can flow securely. An example of this would be the L2TP/IPsec VPN. RSA is the commonly used asymmetric algorithm that was the very first of its kind, creating public and private key pairs. Elliptic Curve Cryptography is an asymmetric algorithm used for the encryption of small mobile devices.
Asymmetric – PKI
Asymmetric keys are obtained from a CA. If you are selling products or services with external entities, then you need to obtain your X509s from a public CA, otherwise your internal certificates will not be accepted.
Asymmetric – weak/depreciated algorithms
A SSL should now be depreciated as it is weak; an example of an exploit is the POODLE attack, which is a man-in-the-middle attack that exploits the vulnerabilities of SSL 3.0 and SSL 3.0 (CBC). Asymmetric algorithms should not be using a key whose strength is 2046 or lower. However, a SSL VPN is the only VPN that uses a SSL certificate and works with legacy clients.
Asymmetric – ephemeral keys
Ephemeral keys are short-lived keys that are used for a one-time only session. There are two types of Diffie Hellman: Ephemeral (DHE) and Elliptic Curve Diffie Hellman Ephemeral (ECDHE). The other keys, used for other asymmetric and symmetric encryption, are known as static keys, as they have about a two-year lifespan.
Symmetric algorithm – modes of operation
Symmetric encryption is a stream cipher that encrypts data one bit at a time; this is easy to crack and is much slower than a block cipher. Block cipher mode takes blocks of data depending on the key and encrypts that data in blocks—this makes the encryption of a large amount of data much faster.
In a L2TP/IPSec VPN tunnel, we have a choice of three different versions of symmetric encryption; the weakest is DES, which has 56-bit key, followed by Triple Des (3DES), which has a 168-bit key. The most secure is AES as it can go from 128 bits up to 256 bits. Remember, symmetric encryption has only one key. It is much faster for encrypting a larger amount of data, but it needs Diffie Hellman, an asymmetric technique, to create a secure tunnel before it is used.
Symmetric encryption – stream versus block cipher
Symmetric encryption uses a block cipher, where blocks of data are encrypted. The key size determines how large the block of data is; for example, if I use DES, then I can only encrypt blocks of 56 bits, whereas AES can encrypt blocks of data of up to 256 bits.
Asymmetric encryption encrypts one bit at a time, therefore it is slower but more secure than symmetric encryption as it uses a larger key size and uses two keys: public and private.
Symmetric encryption – confusion
Confusion massively changes the input to the output by putting it through a non-linear table created by the key.
Symmetric encryption – secret algorithm
A secret key is the piece of information that is used to encrypt and decrypt messages in symmetric encryption.
Symmetric – session keys
A session key is an encryption and decryption key that is randomly generated to ensure the security of a communications session between a user and another computer or between two computers. A RADIUS server could create a session key for a user being authenticated.
Hashing algorithms
A hashing algorithm takes the data from a document and generates a hexadecimal value from that input. If you take the same data and hash it with the same algorithm it will generate the same hash. In the Security + exam, the hashing algorithms are SHA-1, which is 160 bits, and MD5, which is 128 bits. Hashing is a one-way function to ensure that the integrity of the data is intact.
Crypto service provider
A crypto service provider is a software library. For example, Microsoft uses the CryptoAPI and has providers such as:
-
Microsoft AES cryptographic provider: This service provider provides support for the AES algorithm.
-
Microsoft DDS and Diffie-Hellman/channel cryptographic provider: This supports hashing and data signing with DSS and key exchanging for Diffie-Hellman.
Crypto module
A Crypto module is a combination of hardware or software that implements crypto functions such as digital signatures, encryption, random number generation, or decryption.
Protecting data
One of the key functions of a security team is to protect a company's data as it is difficult to put a cost value on lost data. Let us look at three types of data—when it is at rest, in use, and in transit:
-
Data-at-rest: Data-at-rest is when data is not being used and is stored either on a hard drive or external storage; let us look at the different devices:
-
Desktops and laptops: We could use, for example, Bitlocker, which is known in the Security + exam as Full Disk Encryption. However, the desktop or laptop would need a TPM chip built into the motherboard. We could also use Data Loss Prevention (DLP) to prevent someone stealing the data with a USB drive.
-
Tablets/phones: Tablets and phones will need Full Device Encryption (FDE) to encrypt the device so that data cannot be stolen.
-
USB or removable drive: For removable devices, we should use Full Disk Encryption so that if the drive is lost or stolen, the data will not be readable.
-
Data-in-transit: When we are using the internet to purchase items, we use https to encrypt the session before we enter the credit card details. If we are outside of the company, we would use a VPN session to tunnel into the workplace to access data. TLS will be used to encrypt emails as they travel between mail servers.
-
Data-in-use: When we use memory on a device, it is in the Random Access Memory or a faster block of memory called the CPU cache. We can protect this data by using Full Memory Encryption.
-
Basic cryptographic terminology
The Security+ exam is full of cryptographic terminology, and in this section, we are going to look at these, starting with obfuscation, which makes the code obscure. Try asking your family and friends to say the word obfuscation and watch them struggle. It is aptly named as the word itself is very obscure! You must know the terminology thoroughly.
Obfuscation
Obfuscation is the process where you take source code and make it look obscure so that if it was stolen it would not be understood.
Pseudo random number generator
Pseudo Random Number Generator (PRNG) refers to an algorithm that uses mathematical formulas to produce sequences of random numbers. Random numbers can be used when generating data encryption keys.
Nonce
A nonce is an arbitrary number that can be used just once; it is often a random (https://en.wikipedia.org/wiki/Randomness) or pseudo-random (https://en.wikipedia.org/wiki/Pseudorandomness) number issued in an authentication protocol (https://en.wikipedia.org/wiki/Authentication_protocol) to ensure that old communications cannot be reused in replay attacks (https://en.wikipedia.org/wiki/Replay_attack).
Perfect forward secrecy
When a VPN makes a secure connection, a key exchange is made for each secure session, but it links to the server's private key. With perfect forward secrecy, there is no link between the session key and the server's private key, therefore even if the VPN server has been compromised, the attacker cannot use the server's private key to decrypt the session.
Security through obscurity
The concept of security through obscurity is to prevent anyone from outside the organization from knowing the architecture or design of the system or any of its components. The internal people are aware of the weaknesses of the system, but you want to prevent an outside person from knowing anything about the system. Obfuscation is a technique that makes the storing of source code unreadable.
Collision
If you hash the same data or password with MD5 or with SHA-1, then it will always create the same hash. Hashes are used to store passwords or digitally sign documents. A collision attack is where the attacker tries to match the hash; if the hash is matched, it is known as a collision, and this could compromise systems.
Steganography
Steganography is where a document, an image, an audio file, or a video file can be hidden inside another document, an image, an audio file, or a video file.
Diffusion
Diffusion is a technique where if you change one character of the input, it will change multiple bits of the output.
Implementation versus algorithm
In today's world, the security administrators need to look at how the company operates to ensure it is more secure. Do they want to implement smart cards for multifactor authentication or implement a VPN so that remote users can connect to the company securely? Do they need to implement a Data Loss Prevention (DLP) template to ensure that sensitive data cannot be emailed from the company?
Once the company vision has been decided, the security team then needs to look at the algorithms that they need. Normally, this would be the strongest possible, however, we need to ensure that the server has enough processing power to deal with any increase in key length. We should not be using a key of less that 2,046 bits as it would be too insecure.
Common use cases for cryptography
The words use case in the Security+ exam just mean examples of when something is used. We are now going to look at examples of when different cryptography is used.
Supporting confidentiality
A company's data cannot be priced, and the disclosure of this data could cause grave danger to the company. If your competitors stole your secrets, they could beat you to the market and you would not get the rewards that you deserved. To prevent data from being accessed, we will encrypt the data to prevent it from being viewed and prevent any protocol analyzer from reading the packets. When people access the company's network from a remote location, they should use a L2TP/IPSec VPN tunnel, using AES, as the encryption to create a secure tunnel across the internet and to prevent man-in-the-middle attacks. Encryption could be coupled with mandatory access control to ensure that data is secure and kept confidential.
Supporting integrity
There are two main reasons for ensuring integrity. The first would be to hash data stored on a file server so that it can be proved whether or not that the data has been tampered with. This could also be the case for a forensic examination of a laptop seized by the police—the forensic scientist could hash the data before the examination and then re-hash it at the end to prove that he had not tampered with the data. The hash values should match.
Another method of proving integrity would be to digitally sign an email with your private key to prove to the recipient that it has not been tampered with in transit. Prior to this, you would have to send them your Public key to validate the email. This proves that the email has maintained its integrity and has not been tampered with in transit.
Supporting non-repudiation
When you digitally sign an email with your private key, you cannot deny that it was you as there is only one private key; this is known as non-repudiation. When two separate parties decide to do a business deal together, they may use a third party to create a digital contract, but parties would log in to where the contract was stored—once they digitally sign it, then it is legally binding.
Supporting obfuscation
When companies store their source code, they use obfuscation to make it obscure and so that it cannot be read by anyone who steals it. This is also known as security by obscurity, where you want to prevent third parties knowing about your IT systems and identifying any weaknesses in the system.
Low-power devices
Small IoT devices will need to use elliptic curve cryptography for encryption as it uses a small key—they do not have the power processing power for convention encryption.
Low latency
When using encryption, we should use symmetric ciphers such as 3DES or AES to encrypt large amounts of because they both use block cipher encryption with a small key length, compared to asymmetric keys, which have a minimum of 1,024 bits. The server will not have to use as much processing power, as the larger the key length, the more processing and possible latency that can occur. We should implement network accelerator cards where there is a lot of encryption and decryption.
High resiliency
We should be using the most secure encryption algorithm to prevent the encryption key from being cracked by attackers. The more secure the encryption key, the longer and more processing power it will take to gain the encryption key. In an RSA encryption environment, we should use a key with at least 3,072 bits or higher. We should also look at implementing accelerator cards to reduce the amount of latency on the encryption or decryption.
Supporting authentication
A corporate environment should not use a single-factor username and password as it is not as secure as a multifactor. We should adopt at least two-factor authentication and use a smart card and PIN to make authentication more secure. Installing a RADIUS server adds an additional layer to authentication to ensure that authentication from the endpoints is more secure.
Resource versus security constraints
The more secure the encryption used and the higher the key length, the more processing power and memory that the server will need. If there is not enough resources on the server, it could be vulnerable to a resource exhaustion attack, which causes the systems to hang or even crash—it is like a denial-of-service attack. We must strike a balance between the hardware resources that the server has and the amount of processing power.
Practical exercises
For these three practical exercises, you need a 2012/2016 server that is a domain controller. If you are a home user and have access to a desktop with Windows 7, Windows 8.1, or Windows 10 and do not have a server, you can still complete the second exercise.
Practical exercise 1 – building a certificate server
-
Log in to your 2012/2016 domain controller and Open Server Manager.
-
Select Manage, then Add Roles and Features; click next three times.
-
On the select Server Roles page, check the top box, active directory certificate server. Select the Add Features button. Click next three times. Check the CA, box, then next, and then install. This will take a few minutes; when it is finished, press close.
-
On the Server Manager toolbar, double-click on the yellow triangle; this is a notification. In the post-deployment configuration wizard, double-click on the blue hyperlink, and clock Configure active directory certificate service. Click next, then in the role services wizard, check the CA box. You need to wait a few seconds, then the next button comes alive. Press next twice. In the CA Type wizard, select Root CA and click Next three times. For the CA name under common name for this CA, enter the name MyCA, click next three times, then click Configure. After it is configured, press close.
-
On the server manager toolbar press Tools, then CA. Expand MyCA on the left-hand side, then expand issued certificates, and it should be blank, as no certificates have been issued. See the following screenshot:
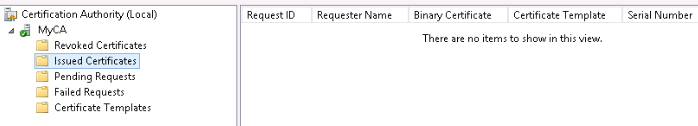
Figure 12: Certificate authority
Practical exercise 2—encrypting data with EFS and steal certificates
Follow these steps:
-
Go to the desktop; create a folder called test.
-
Inside the folder, create a text document called data.
-
Right-click the folder called data, then select Properties.
-
On the General tab, click Advanced, then check the box against encrypt content to secure data. The data folder should turn green; that means it is encrypted with EFS.
-
Go to the Start button, then type mmc and select the icon with the red suitcase.
-
Console 1 should open. Select File—Add remove snap in, then select certificates, select add, click next, and then finish.
-
Expand certificates—current user, expand personal. You should see an entry for an EFS certificate.
-
Right-click the Certificate. Select All tasks—export.
-
The certification export wizard appears. Press Next. On the Export Private Key, select Yes, export the private key, press Next. You will see it is the P12 format, Press Next, check the password box, enter the password 123 twice, and then press next. In the file to export, call it PrivKey and save it to the desktop. Press next and then finish.
-
The export was successful box should appear.
-
Repeat the exercise and export the public key as PubKey.
-
You should notice the two files on the desktop; the public key has a .cer extension and looks like a certificate. The private has a .pfx extension and looks like a letter being inserted into an envelope.
Practical exercise 3 – revoking the EFS certificate
-
Go to Server Manager—Tools and select Certificate Authority.
-
Expand issued certificates and then you should now see an EFS certificate.
-
Right-click the Certificate and select All Tasks.
-
Revoke the Certificate.
You will now notice it has moved from issued certificates to revoked certificates.
Review questions
-
What type of certificate does CA have?
-
If I am going to use a CA internally, what type of CA should I use?
-
If I want to carry out b2b activity with third-party companies or sell products on the web, what type of CA should I use?
-
Why would I make my CA offline when not in use?
-
Who builds the CA or intermediary authorities?
-
Who signs the X509 certificates?
-
What can I use to prevent my CA being compromised and fraudulent certificates being issued?
-
If two entities want to set up a cross certification, what must they set up first?
-
What type of trust model does PGP use?
-
How can I tell if my certificate is valid?
-
If the CRL is going slow, what should I implement?
-
Explain certificate stapling/OCSP stapling?
-
What is the process of obtaining a new certificate?
-
What is the purpose of the key escrow?
-
What is the purpose of the HSM?
-
What is the purpose of the DRA and what does it need to complete its role effectively?
-
How can I identify each certificate?
-
What type of file extension and format is a private certificate?
-
What type of file extension and format is a public certificate?
-
What format is a PEM certificate?
-
What type of certificate can be used on multiple servers in the same domain?
-
What type of certificate can be used on multiple domains?
-
What should I do with my software to verify that is it original and not a fake copy?
-
What is the purpose of extended validation of a X509?
-
What type of cipher is the Caesar cipher and how does it work if it uses ROT 4?
-
What is encryption and what are the inputs and outputs called?
-
What type of encryption will be used to encrypt large amounts of data?
-
What is the purpose of Diffie Hellman?
-
What is the first stage in any encryption, no matter if it is asymmetric or symmetric?
-
If Carol is encrypting data to send to Bob, what key will they each use?
-
If George encrypted data four years ago with an old CAC card, can he un-encrypt the data with his new CAC card?
-
If Janet is digitally signing an email to send to John to prove that it has not been tampered with in transit, what key will they each use?
-
What two things does digitally signing an email provide?
-
What asymmetric encryption algorithm should I use to encrypt data on a smartphone?
-
What shall I use to encrypt a military mobile telephone?
-
Name two key stretching algorithms.
-
What is the purpose of key stretching?
-
What is the difference between stream and block cipher modes, and which one will you use to encrypt large blocks of data?
-
What happens with cipher block chaining if I don't have all of the blocks?
-
If I want to ensure the integrity of data, what shall I use? Name two algorithms.
-
If I want to ensure the protection of data, what shall I use?
-
Is a hash a one-way or two-way function, is it reversible?
-
What type of man-in-the-middle attack is SSL 3.0 (CBC) vulnerable to?
-
Explain why we would use Diffie Hellman Ephemeral (DHE) and Elliptic Curve Diffie Hellman Ephemeral (ECDHE).
-
What are the strongest and weakest methods of encryption with a L2TP/IPSec VPN tunnel?
-
What is the name of the key used to ensure the security of communications between a computer and a server or a computer to another computer?
-
What should I do to protect data-at-rest on a laptop?
-
What should I do to protect data-at-rest on a tablet or smartphone?
-
What should I do to protect data-at-rest on a backend server?
-
What should I do to protect data-at-rest on a removable device such as a USB flash drive or an external hard drive?
-
What two protocols could we use to protect data-in-transit?
-
How can you protect data-in-use?
-
What is the purpose of obfuscation?
-
What is the purpose of perfect forward secrecy?
-
What type of attack tries to find two has values that match?
-
What is the purpose of rainbow tables?
-
Explain the concept of steganography.
-
What are the two purposes of data loss protection?
-
What is the purpose of salting a password?
Answers and explanations
-
A CA has a root certificate that he uses to sign keys.
-
I would use a private CA for internal use only; these certificates will not be accepted outside of your organization.
-
I would use a public CA for b2b activities.
-
If you were a military, security, or banking organization, you would keep the CA offline when it is not being used to prevent it being compromised.
-
An architect would build the CA or intermediary authorities.
-
The CA would sign the X509 certificates.
-
Certificate pinning can be used to prevent a CA being compromised and fraudulent certificates being issued.
-
If two separate PKI entities want to set up a cross certification, the Root CAs would set up a trust model between themselves, known as a bridge trust model.
-
PGP uses a trust model known as a Web of Trust.
-
A Certificate Revocation List (CRL) is used to determine if a certificate is valid.
-
If the CRL is going slow, an OCSP is used as it provides faster validation.
-
Certificate stapling/OCSP stapling is where a web server uses an OCSP to for faster certificate authentication, bypassing the CRL.
-
A Certificate Signing Request (CSR) generates two keys; the Public key is sent to the CA and then sends back the X509.
-
The key escrow stores and manages private keys for third parties.
-
A hardware security module is used by the key escrow as it securely stores and manages certificates.
-
When a user's private key goes corrupt, the data recovery agent recovers the data by obtaining a copy of the private key from the key escrow.
-
Each certificate can be identified by its OID, which is similar for each certificate.
-
A public certificate is in a P7B format with a .cer extension.
-
A private certificate is in a P12 format with a .pfx extension.
-
A PEM certificate is in a Base64 format.
-
A wildcard certificate can be used on multiple servers in the same domain.
-
A Subject Alternative Name (SAN) certificate can be used on multiple domains.
-
Code signing software is similar to hashing the software and ensuring the integrity of the software.
-
Extended validation is normally used by financial institutions as it provides a higher level of trust for the X509; when it is used the URL background turns green.
-
The Caesar cipher is a substitution cipher; an example would be ROT 4 where each letter would be substituted by a letter four characters further along in the alphabet.
-
Encryption is when plaintext is taken and turned into ciphertext.
-
Symmetric encryption is used to encrypt large amounts of data as it uses one key.
-
Diffie Hellman is an asymmetric technique that creates a secure tunnel; during a VPN connection, it is used during the IKE phase and uses UDP Port 500 to create the VPN tunnel.
-
The first stage in encryption is key exchange. During asymmetric encryption each entity will give the other entity their Public Key. The private key is secured and never given away.
-
Carol uses Bob's Public Key to encrypt the data and then Bob will use his private key to decrypt the data. Encryption and decryption are always done by the same key pair.
-
George must obtain the old private key to decrypt the data as the encryption was done with a different key pair.
-
Janet will digitally sign the email with her private key and John will check its validity with Janet's Public key, which he would have received in advance.
-
A digital signature provides both integrity and non-repudiation.
-
Elliptic Curve Cryptography will be used to encrypt data on a smartphone as it is small and fast and uses the Diffie Hellman handshake.
-
AES-256 will be used to encrypt a military mobile telephone.
-
Two key-stretching algorithms are Bcrypt and PBKDF2.
-
Key stretching salts the password being stored so that duplicates passwords are never stored and it increases the length of the keys to make it harder for a brute force attack.
-
Stream encrypts one bit at a time and block cipher takes blocks of data, for example 128-bit modes. A block cipher will be used for large amount of data.
-
Cipher Block Chaining needs all of the clocks of data to decrypt the data, otherwise it will not work.
-
Hashing ensures the integrity of data; two examples are SHA-1 (160 bit) and MD5 (128 bit).
-
Encryption is used to protect data so that it cannot be reviewed or accessed.
-
A hash is one-way and cannot be reversed.
-
POODLE is a man-in-the-middle attack on a downgraded SSL 3.0 (CBC).
-
DHE and ECDHE are both ephemeral keys that are short-lived, one-time keys.
-
The strongest encryption for a L2TP/IPSec VPN tunnel is AES and the weakest is DES.
-
A session key ensures the security of communications between a computer and a server or computer to another computer.
-
Data-at-rest on a laptop is protected by FDE.
-
Data-at-rest on a tablet or smartphone are both protected by Full Device Encryption.
-
Data-at-rest on a backend server is stored on a database, therefore it needs database encryption.
-
Data-at-rest on a USB flash drive or external hard drive is done via Full Disk Encryption.
-
Data-in-transit could be secured by using TLS, HTTPS, or a L2TP/IPsec tunnel.
-
Data-in-use could be protected by Full Memory Encryption.
-
Obfuscation is used to make source code look obscure so that if it is stolen it cannot be understood.
-
Perfect forward secrecy ensures that there is no link between the server's private key and the session key. If the VPN server's key was compromised, it could not decrypt the session.
-
A collision attack tries to match two hash values to obtain a password.
-
Rainbow tables are a list of precomputed words showing their hash value. You will get rainbow tables for MD5 and different rainbow tables for SHA-1.
-
Steganography is used to conceal data; you can hide a file—image, video, or audio—inside another image, video, or audio file.
-
DLP prevents sensitive or PII information being emailed out of a company or being stolen form a file server using a USB device.
-
Salting a password ensures that duplicate passwords are never stored and makes it more difficult for brute force attacks by increasing the key size (key stretching).

