Users Online
· Members Online: 0
· Total Members: 188
· Newest Member: meenachowdary055
Forum Threads
Latest Articles
Articles Hierarchy
#CompTIA Security+ 501 exam Chapter05 Understanding Network Components Part 1
Understanding Network Components
In this chapter we are going to look at networking components and how they could affect the Security of your network, we will look at firewalls, switches and routers. We will start by look at the OSI Reference model that was created to improve communications between devices.
We will cover the following exam objectives in this chapter:
-
Install and configure network components, both hardware—and software-based, to support organizational security: Firewall—ACL—application-based versus network-based—stateful versus stateless—implicit deny. VPN concentrator—remote access versus site-to-site—IPSec—tunnel mode—transport mode—AH—ESP—split tunnel versus full tunnel—TLS—always-on VPN. NIPS/NIDS—signature-based—heuristic/behavioral—anomaly—inline versus passive—in-band vs. out-of-band—rules—analytics—false positive—false negative. Router—ACLs—antispoofing. switch—port security—layer 2 versus layer 3—loop prevention—flood guard. Proxy—forward and reverse proxy—transparent—application/multipurpose. Load balancer—scheduling—affinity—round-robin—active-passive—active-active—virtual IPs. Access point—SSID—MAC filtering—signal strength—band selection/width—antenna types and placement—fat versus thin—controller-based versus standalone. SIEM—aggregation—correlation—automated alerting and triggers—time synchronization—event deduplication—logs/WORM. DLP—USB blocking—cloud-based—e-mail. NAC—Dissolvable versus permanent—host health checks—agent versus agentless. Mail gateway—spam filter—DLP—encryption. Bridge, SSL/TLS accelerators, SSL decryptors, media gateway. Hardware security module
-
Given a scenario, implement secure protocols: Protocols—DNSSEC—SSH—S/MIME—SRTP—LDAPS—FTPS—SFTP—SNMPv3—SSL/TLS—HTTPS—secure POP/IMAP. Use cases—voice and video—time synchronization—e-mail and web—file transfer—directory services—remote access—domain name resolution—routing and switching—network address allocation—subscription services
-
Given a scenario, implement secure network architecture concepts: Zones/topologies—DMZ—extranet—intranet—wireless—guest—honeynets—NAT—Ad hoc. Segregation/segmentation/isolation—physical—logical (VLAN)—virtualization—air gaps. Tunnelling/VPN—Site-to-site—Remote access. Security device/technology placement—Sensors—collectors—correlation engines—filters—proxies—firewalls—VPN concentrators—SSL accelerators—load balancers—DDoS mitigator—aggregation switches—taps and port mirror. SDN
-
Given a scenario, install and configure wireless security settings: Cryptographic protocols—WPA—WPA2—CCMP – TKIP. Authentication protocols—EAP—PEAP—EAP-FAST—EAP-TLS—EAP-TTLS—IEEE 802.1x—RADIUS federation. methods—PSK versus enterprise versus open—WPS—captive portals
OSI – reference model
The Open Systems Interconnection (OSI) reference model was created by the Internet Standards Organization (ISO) and it is a reference model used for communication. Each of the seven different layers has different protocols and responsibilities. The Security+ exam focuses mainly on layers 2, 3, and 7:
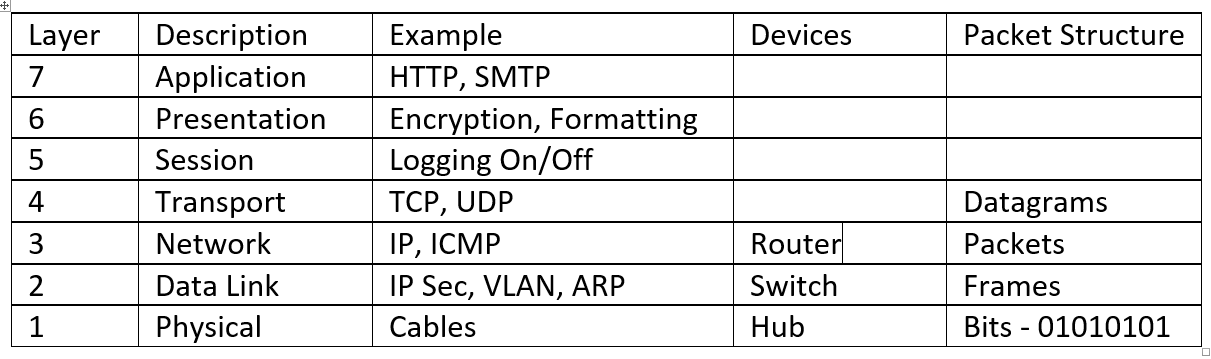
Figure 1: OSI reference model
Here is a brief summary of each layer:
-
Application layer: Applications, such as HTTP for accessing the web or SMTP for accessing email, are launched here. The Web Application Firewall (WAF), whose job it is to protect web-based applications, operates at this layer.
-
Presentation layer: The presentation layer formats data into the character code, such as Unicode or ASCII. Encryption also works at this layer.
-
Session layer: This is where you would create a session, such as logging in and logging out.
-
Transport layer: Ports are either TCP or UDP. TCP is connection-orientated as it uses a three-way handshake and acknowledges the receipt of each packet, whereas UDP is connectionless and the application is responsible for checking the data has arrived. Most ports are TCP-based, but streaming video will use UDP as it is much faster than TCP.
-
Network layer: The network layer is responsible for Internet Protocol (IP) addressing and routing. A router whose function is to route packets works at this layer, and a Layer 3 switch that is a multifunction switch also operates at this layer. The format of data is called packets, hence we hear of IP packets. The Internet Control Message Protocol (ICMP) operates at this layer, when troubleshooting tools such as ping, tracert, or pathing are used, ICMP produces the replies.
-
Data-link layer: The three main functions of the data-link layer are to deal with transmission errors, regulate the flow of data, and provide a well-defined interface to the network layer. MAC addresses operate at this layer. This is the lowest layer that a switch operates at. When the exam talks about a switch, this is the Layer 2 switch. The Address Resolution Protocol that translates an IP to a MAC address, IPSec, an encryption-tunneling protocol, switches, and virtual local area network (VLAN), where you can segment traffic on a switch, all work at that layer.
-
Physical layer: Cables operate at the physical layer, such as Ethernet, coaxial, and wireless communication.
When protocols, such as the TCP IP protocol suite, are created, it is based on some or all layers of this model.
Exam tip: When a switch is mentioned, it is a Layer 2 switch that can create VLANs. ARP operates at Layer 2 and an ARP attack must be done locally on the host.
Installing and configuring network components
There are many network components and topologies (layouts) that we need to know about to maintain a secure environment. We are going to look at each of these in turn. We need to know how each device is configured and which device is the most appropriate in different scenarios. We will look at the firewall, whose main job is to prevent unauthorized access to the network
Firewall
A firewall prevents unauthorized access to the corporate network, and in the Security+ exam, we tend to use a back-to-back configuration, as shown here:
Figure 2: Back-to-back firewall configuration
You can see each of these firewalls is not letting traffic pass through them; this is because we need to open only the ports that we need. If Firewall 1 is traversed, then Firewall 2 will hopefully prevent access to the internal network known as the local area network. To enable applications to pass through the firewall, we must open the port number for each application. Each application has a different port number, if you think of someone who wants to watch the news, the Democrats watch CNN on Channel 21 and the Republicans will watch Fox News on Channel 29. Each TV programme has a different channel number. If we want to enable internet access, we should make an exception to the Hypertext Transfer Protocol (HTTP) on TCP port 80. This is the port number that each web server works on no matter whether we use Internet Explorer, Microsoft Edge, Google Chrome, or Firefox; each of these applications uses TCP port 80 to allow web traffic.
The direction of ports is outbound coming from the internal network going to the external network, or inbound coming from outside to the internal network. If we opened only the outbound port for port 80, the request would go out but the incoming response would be prevented.
The main purpose of a firewall is to prevent unauthorized access to the network. The default setting is to block all traffic allowed by exception. There are many different firewalls:
-
Host-based firewall: This is an application firewall that is built into desktop operating systems, such as the Windows 10 operating system:
Figure 3: Host-based firewall
As the host-based firewall is an application on a desktop, it is vulnerable to attack. If someone disables the service running the Windows firewall service, then the firewall is disabled and the computer becomes vulnerable. Remember from Chapter 4, Delving into Identity and Access Management, services are started using a service account, a type of administrative account. The following image shows a running firewall service:
Figure 4: Windows firewall service
-
Network-based firewall: A hardware product that keeps the network safe. It is vital that only the ports required are open. One of the configurations is the back-to-back configuration where two layers of firewall are rolled out. The network-based firewall is placed at the edge of the network to prevent unauthorized access.
-
Stateful firewall: Looks deep at the application and its traffic to see whether it is allowed through. Example: A packet arrives with the Get<webpage> command, because the Get verb in HTTP is the request to view a web page, the traffic is allowed. However, if the HTTP verbs use the PUT verb that could be used to deface the web page, it is blocked. If HEAD is used, it tries to pull down the website header information and it is also blocked. The stateful firewall knows the size of each packet and will block traffic that is not the size that it should be.
-
Stateless firewall: The stateless firewall could also be called a packet-filtering firewall. It only looks at whether the packet is permitted and never looks in depth at the packet format.
-
Web Application Firewall (WAF): The Web Application Firewall is placed on a web server and its role is to protect the web-based applications running on the webserver.
-
Unified Threat Management Firewall (UTM): The UTM is a multipurpose firewall that is a firewall: that does malware, content, and URL filtering. It is known as an all-in-one security appliance.
Exam tip: A UTM firewall is an all-in-one security appliance that acts as a firewall and does content and URL filtering. It can also inspect malware.
Router
A router is a device that connects two different networks together, when setting up a host machine, it is known as the default gateway. It is used by your company to give you access to other networks, for example the internet. It has a routing table built into it, so it knows which route can be used to deliver network packets. The router is the IP equivalent of a post office sending letters around the world, but instead of letters, IP packets are being transported.
Access Control List (ACL): The router sits on the external interface and uses an ACL so it can also filter the traffic coming into the network by:
-
Port number
-
Protocol
-
IP address
Anti-spoofing: An anti-spoofing filter is placed on the input side of a router interface and only allows packets through that are within the address range of that subnet. It excludes packets that have invalid source addresses.
Access control list– network devices
The Access Control List (ACL) for network devices must not be confused with the ACL for files and folders, they are totally different. Two network devices that use ACL are firewalls and routers. The ACL prevents access by using port numbers, application names, or its Internet Protocol (IP) address. When you install a new firewall or router, there are no rules except the last rules of deny all. The default for either a router or firewall is to block all access allowed by creating exceptions using allow rules for the traffic you want to allow through. If there are no allow rules, the last rule of deny applies, this is called an Implicit Deny.
Example:
John has been doing some online shopping and bought a pair of shoes, but he cannot download the new book that he bought. He has used HTTP to gain access to a website, and then gone to the secure server for payment, using HTTPS for purchases, to protect his credit card details; however, when trying to download the book, the traffic is being blocked by the firewall. The ACL allows TCP port 80 (HTTP) and HTTPS, but there is no allow rule for FTP that used TCP port 21:
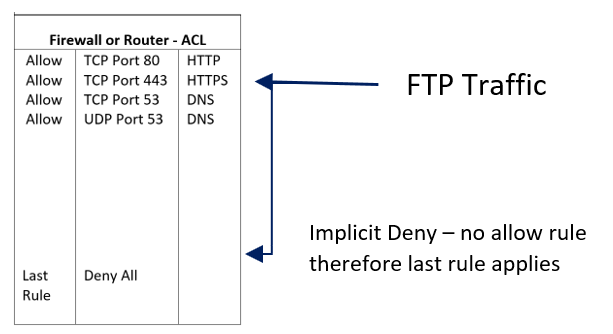
Figure 5: Implicit deny
As there is no allow rule on the firewall for FTP traffic, when the FTP traffic arrives, it is checked against the allow rules, and if there is no matching rule, it then drops down to the last rule, denying all traffic – this is known as Implicit Deny. Although the example is for a firewall, an ACL is used by the router. Both devices are filtering incoming traffic.
Intrusion-prevention system
There are two types of Intrusion-Prevention Systems (IPS), the first is the Network Intrusion Prevention System (NIPS), which can only operate on your network and cannot work inside a host. The second is called the Host Intrusion Prevention System (HIPS), and it operates inside a host machine and cannot operate on the network.
NIPS is an internal network device whose role is to prevent access to the network, and it is placed on the perimeter of your network behind your firewall. Think of NIPS as Rambo with a big gun whose job it is to shoot the bad guys.
Intrusion-detection system
The Intrusion-Detection System (IDS) is the same as the IPS, there is the HIDS which only works on a host, and the NIDS which only works on the network. Think of the IDS as Sherlock Holmes, the famous detective, his job is to find different traffic patterns on the network and then inform Rambo, the NIPS, who will then remove them from the network.
Exam tip: NIPS has the capability to detect as well as protect if there are no NIDS on your network. To protect a virtual machine from attack, you will install a HIPS.
Modes of detection
There are three modes of detection used by the NIPS/NIDS. For the purpose of the exam, you must know them thoroughly:
-
Signature-based: Works off a known database of known exploits and cannot identify new patterns. If their database is not up to date, they will not operate efficiently.
-
Anomaly-based: Starts off the same as the signature-based with the known database but they have the ability to identify new variants.
-
Heuristic/behavioral-based: Instead of trying to match known variants, the Heuristic/Behavioral starts off with a baseline and matches traffic patterns against the baseline. It could also be known as anomaly-based.
Exam tip: Anomaly-based NIPS/NIDS detect new patterns and are much more efficient than signature-based, which can only work with known variants.
Modes of operation
There are different modes of operation for the sensors of the NIPS/NIDS:
-
Inline: The NIPS will be placed on or very near to the firewall as an additional layer of security when the NIPS has been set up in inline mode the flow of traffic goes through the NIPS. This is known as in-band.
-
Passive: The traffic does not go through the NIPS, this mode is normally used by the NIDS as it detects changes in traffic patterns in the local network. This is known as out of band.
When sensors are placed inside the network, they can only detect traffic once it is inside your network and has passed through your firewall. If you wish to detect attacks before they come into your network, the sensor must be placed on the external network to the firewall.
Monitoring data
When analytics (how we analyze the data) analyze the information provided, it is based on rules that are set inside the IPS/IDS. However, no system is foolproof. They try their best but sometimes provide outcomes different than those expected. There are two different types:
-
False positive: The NIDS/NIPS has decided, based on the information gathered, that an attack is taking place. However, when the network administrator investigates it, they find that there is no attack.
-
False negative: The NIDS/NIPS is not updated and attacks have been taking place without detection.
Exam tip:
A false positive is a false alarm, however a false negative doesn't detect anything while you are being attacked.
Switch
A switch is an internal device that connects all users in a local-area network. The switch has a table listing the MAC addresses of the host connected to it:

Figure 6: Cisco switch
Once the switch has been installed, it builds up a routing table; each host is identified by their MAC address. The switch delivers the packet only to the host that requires the packet. Switches can be stacked when there are more than 48 users connected to the network:
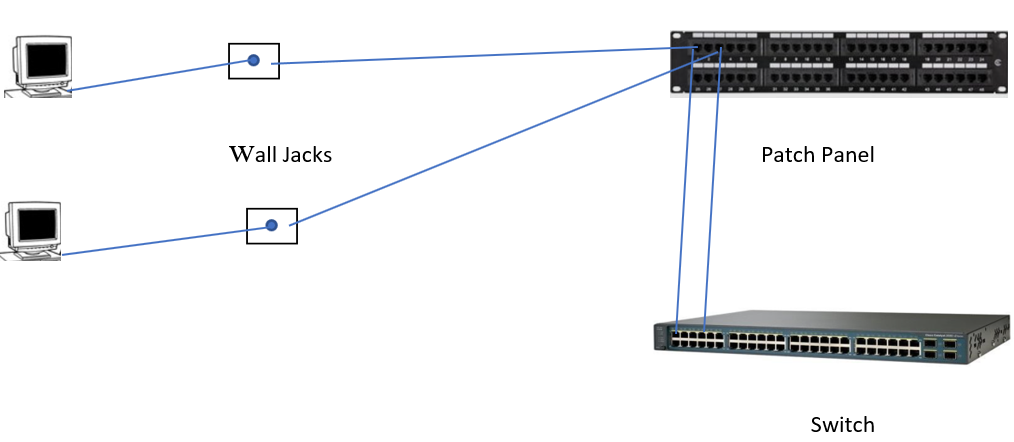
Figure 7: Network connections
A computer has an ethernet cable that plugs into a wall jack, then the wall jack is connected to the patch panel by cables that are laid under floors or above ceilings, a user cannot see them. From the patch panel, there is a cable that goes into one port on the switch. It is very easy to plug a cable into a wall jack the network administrator must place security on the switch. There are two types port security and 802.1x and other protection that can be configured:
-
Port security: When an authorized user plugs their laptop into one of the wall-jack ports, the network administrator can prevent this in future by implementing port security. Port security turns the port off, so no matter who connects to it, they will not get a connection. The downside is that if you have a 48-port switch and put port security on 40 of the ports, it only leaves enough ports to connect eight users; this is not practical, therefore port security should be used sparingly.
-
802.1x: When a network administrator uses 802.1x port security, the device itself is authenticated before a connection is made herefore the same port can be used by an unauthorized device and an authorized device,and only the latter will obtain a connection. The benefit of 802.1x over port security is that none of the ports on the switch has been disabled and the switch has full functionality.
-
Flood guard: Prevents MAC flooding and Denial of Service attacks on a switch by identifying the attack and preventing it.
-
Loop protection: When two or more switches are joined together, they can create loops that create broadcasts. We need to use the Spanning Tree protocol to prevent this from happening by forwarding, listening, or blocking on some ports.
Exam tip:
If you want to prevent someone plugging their laptop into a waiting area, we will use Port Security to shut that port down. But if you want to prevent a rogue Server or a Wireless Access Point from connecting to the network, we will use 802.1x port security, which authenticates the device.
Layer 3 switch
Traditional switches work at layer 2 of the OSI Reference Model and are susceptible to ARP attacks. However, a layer 3 switch operates at the network layer using the IP address, and they route packets the same as a router and are high-performance switches. They operate using IP and not MAC addresses and this means that they are not affected by ARP attacks as they operate at Layer 2.
Proxy server
A proxy server is a server that acts as an intermediary for requests from clients seeking resources on the internet or an external network. Think of it as a go-between who makes requests on behalf of the client, ensuring that anyone outside of your network does not know the details of the requesting host.
The flow of data is from internal to external and it has three main functions: URL filter, content filter, and web page caching:
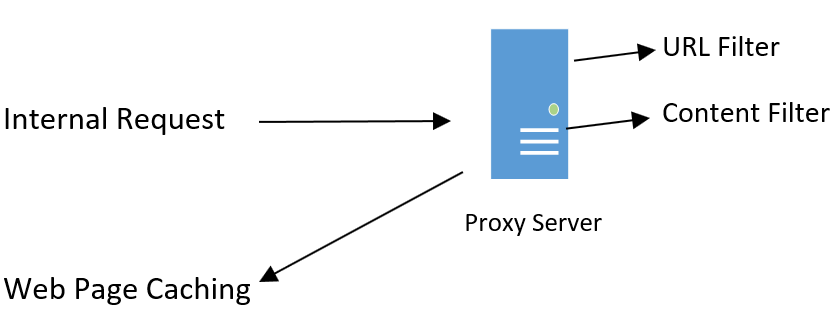
Figure 8: Proxy server
-
URL filter: When a user goes to a website, they type the URL, for example www.nfl.com. Companies may not want their employees going to Facebook or Twitter during working hours, so these websites are placed on the default block page. The URL filter-checks the default block page to see whether there is a website that should be blocked – you will get a warning stating the page is blocked and you cannot access it; additionally, your attempt to access it will be logged.
-
Content filter: Looks at the content on the requested web page. It will block the request if the site involves gambling or inappropriate content.
-
Webpage caching: Most companies within the same industry tend to go to certain websites related to their line of business, or at lunchtimes people look at the sport results. Each time they go to the internet, a session is opened through the firewall; this allows an unsecure session to be seen and also consumes bandwidth. A more secure way of doing this is to have a proxy server cache the pages, but they need to ensure that the frequency of caching ensures that the content is relevant. You could never cache the stock market as the price fluctuates second by second.
-
The purpose of caching is to reduce the bandwidth being used and also make the access to web pages faster as they are actually obtaining content from their Local Area Network (LAN). There are different types of caching:
-
Active caching: The IT team set up jobs to cache webpages, for example cache www.nfl.com at 3 a.m local time to ensure it has the latest results.
-
Caching: When new web pages are being requested (as long as they are not blocked by a filter), the pages are fetched and submitted to the requesting host and a copy is then placed in the cache. That way, the second time it is requested, it is retrieved from the cache.
-
Transparent cache: Intercepts the request by the host and does not modify the search.
-
Non-transparent cache: Intercepts and verifies the request is valid. It looks at the URL filter to see whether the site is blocked. It is used to stop people caching web pages that are restricted.
-
Application proxy: Deals with requests on behalf of another server. A page within an online shop that loads its content and displays data from another location outside of the shop.
-
Reverse proxy
The flow of traffic from a reverse proxy is incoming traffic from the internet coming into your company network. The reverse proxy is placed in a boundary network called the Demilitarized Zone (DMZ). It performs the authentication and decryption of a secure session so it can filter the incoming traffic.
Example: If a company sets up a webinar through Skype or another video conference application, they can invite potential customers. All of the conferencing requests will pass through a reverse proxy that authenticates them and redirects their session to the relevant Skype server.
Remote access
There are times when people who are working remotely need to access the company's network to access resources. There are two main types of remote access:
-
Remote Access Server (RAS): A legacy server where the dial-up networking is used, it is expensive as you need to pay the same cost as a telephone call. The server is located in the company network and the client has software installed to allow communication. Each side has a modem that converts the digital communications in the computer to analog communication that can be transmitted over telephone lines. The speed of the modem is up to 56 Kbps, this make the communication very slow. If you use dial-up networking to access the internet, the pages would load very slowly and look like a map, this is why it has been discontinued.
-
Virtual Private Network (VPN): Located in the company's network and the client has software to allow the connection, but it utilizes the internet, this makes it cheaper to use. Most hotels offer free Wi-Fi and the sessions can be free. The downside is that the internet is the public highway and a secure tunnel is used to protect against attack. The main tunneling protocols are:
-
L2TP/IPSec: The most secure tunneling protocol that can use certification, Kerberos authentication, or a preshared key. L2TP/IPSec provides both secure tunnel and authentication.
-
Secure Socket Layer (SSL) VPN: Works on legacy systems and uses SSL certificates for authentication.
-
Exam tip:
L2TP/IPsec is the only tunneling protocol in the exam objectives, you need to know it thoroughly, especially how IPSec works, both the Authenticated Header (AH) and Encapsulated Payload (ESP). The only other VPN that is mentioned is the legacy SSL VPN that uses a SSL certificate.
Virtual private network using L2TP/IPSec
Before we look at the tunneling protocols, we need to learn a little about encryption – there are two main types of encryption: asymmetric and symmetric. Encryption is the process of taking data in plaintext format and transferring it to ciphertext, a format that makes it unreadable. Encryption is covered in depth later in this book; the two main types are:
-
Asymmetric encryption: Certificates are used for encryption and it uses two keys: a private key and a public key. The public key is used for encrypting data and the private key is used for decrypting data.
-
Symmetric encryption: Uses only one key, called either the private key or shared key, for both encrypting and decrypting data, making it much faster but less secure than asymmetric encryption. Having only one key makes it quicker for encrypting and decrypting large amounts of data; the downside is that it is less secure due to the fact that if someone obtains the private/shared key, they can both encrypt and decrypt the data. When we use symmetric encryption, we tend to create a secure tunnel using an asymmetric technique called Diffie Hellman to create a secure tunnel before the symmetric data is sent across the network or internet.
-
Key length: Certificate keys are formed in units called bits. The fewer the bits, the faster it is to encrypt and decrypt, while a higher number of bits means it is slower to encrypt or decrypt but it is more secure. Typically, we don't use asymmetric keys smaller than 4,096 bits.
Exam tip:
Symmetric encryption is used to encrypt and decrypt large amounts of data as it uses only one key, making it faster than asymmetric, which uses two keys.
A VPN creates a tunnel across the internet, normally from home or a remote site to your work. We need to look at the L2TP/IPSec tunnel that works at Layer 2 of the OSI Reference Model where IPSec is used to encrypt the data, an IPSec packet is formed of two different portions:
-
AH: Consists of either SHA-1 (160 bits) or MD5 (128 bits) hashing protocols, which ensure that the packet header has not been tampered with in transit.
-
ESP: Uses either DES (64 bits), 3 DES (168 bits), or AES (256 bits); these are all symmetric encryption protocols, which means that they can transfer data much faster.
IPSec
IPSec can be used to create a secure session between a client computer and a server. For example, you may have the financial data on a financial server. All members of the finance team will have IPSec tunnels created between their desktops and the financial server. This will prevent anyone using a packet sniffer stealing data from the financial server or any session across the network.
IPSec can also be used as a VPN protocol as part of the L2TP/IPSec tunneling protocol that is used by major vendors who create VPN solutions, such as CISCO, Microsoft, Sonic Wall, or Checkpoint.
IPSec – handshake
The first stage of an IPSec session is to create a secure tunnel—this is known as security association. In the Security+ exam this is called Internet Key Exchange (IKE). Diffie Hellman is used to set up a secure tunnel before the data is:
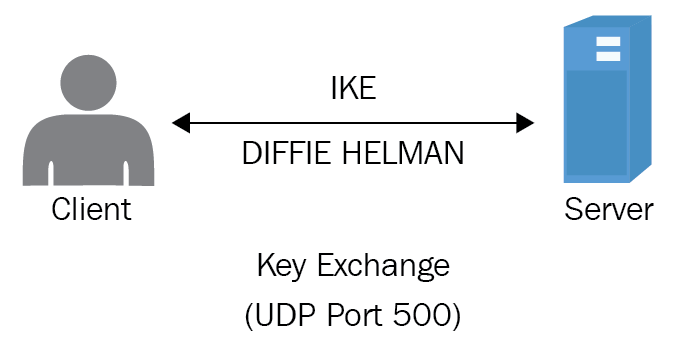
Figure 9: Diffie Helman
The IKE phase of the IPSec session is using Diffie Hellman over UDP port 500 to create what is known as quick mode. This creates a secure session so that the data can flow through it.
The second phase is where the data is encrypted with DES, 3 DES, or AES. AES provides the most secure VPN session as it uses 128, 192, or 256 bits. There are two different IPSec modes:
-
Tunnel mode: Tunnel mode is where the IPSec session is used across the internet as part of the L2TP/IPSec tunnel.
-
Transport mode: Transport mode is where the IPSec tunnel is created with an internal network between a client machine and a server.
VPN concentrator
The purpose of the VPN concentrator is to set up the secure tunnel during the IKE phase. It needs to create a full IPSec tunnel. This normally when you have a site-to-site VPN.
Site-to-site VPN
A site-to-site VPN is where you have two different sites, each with a VPN concentrator at each site and it acts like a lease line. The session is set to always on as opposed to dial on demand:
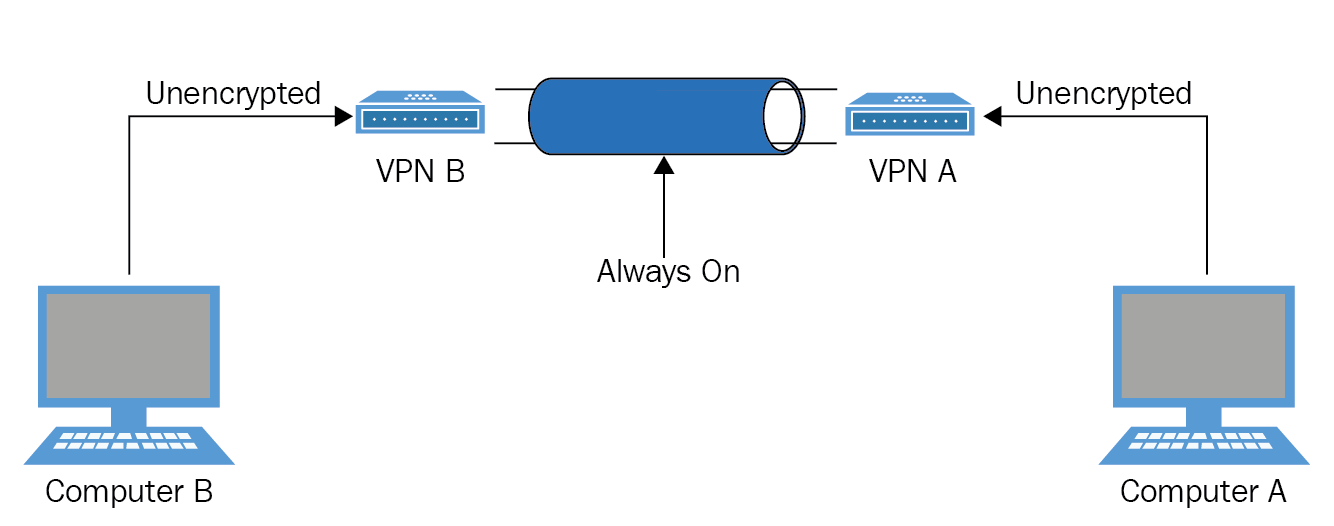
Figure 10: Site-to-site VPN
VPN always on versus on-demand
There are two main session types: the first is on-demand, where a remote worker initiates a VPN session from home or a remote location, and when they finish the session the connection is dropped. The second is where a site-to-site VPN is set up and the session is known as always on, where the session is permanent.
SSL VPN
SSL VPN is a VPN that can be used with a web browser that uses an SSL certificate for the encryption. It has been replaced in recent times with Transport Layer Security (TLS), which is a more modern version of SSL. In the Security+ exam, the SSL VPN is normally used for legacy VPNs that don't support L2TP/IPSec.
Exam tip:
SSL VPN is the only VPN to use an SSL certificate, and it only needs a web browser to make a connection. It could also be replaced by the more secure TLS certificate.
Split tunnelling
Split tunneling is where a secure VPN session is connected and the user opens an unsecure session that would allow the hacker to come in through the unsecured session and gain access to your company's network:
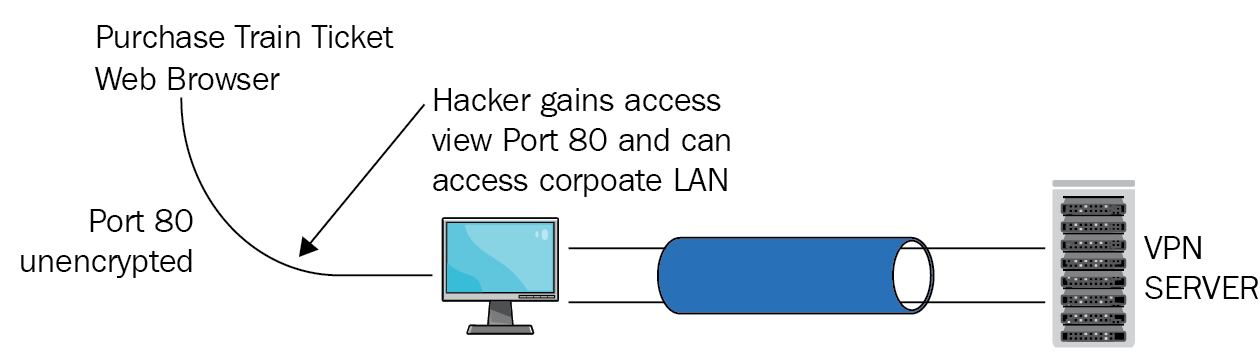
Figure 11: Split tunnel
Example: John connects his L2TP/IPSec session into the company network, then he realizes that he needs a train ticket for tomorrow. Instead of dropping the secure session and then going to the rail website, he leaves it connected. Once he opens up his web browser, he is using HTTP on TCP port 80, which is unsecured. This means that while he has the web browser open, a hacker could access his desktop and use the secure tunnel to gain access to the company network.
Exam tip: A VPN should always set up a full tunnel, no other form of tunneling, such as split tunneling, should be used.
Load balancer
A network load balancer is a device that is used when there is a high volume of traffic coming into the company's network or web server. It can be used to control access to web servers, video conferencing, or email. In the Security+ exam, it is normally a high volume of web traffic. From Figure 12, you can see that the web traffic comes into the load balancer from the Virtual IP address (VIP) on the frontend and is sent to one of the web servers in the server farm:
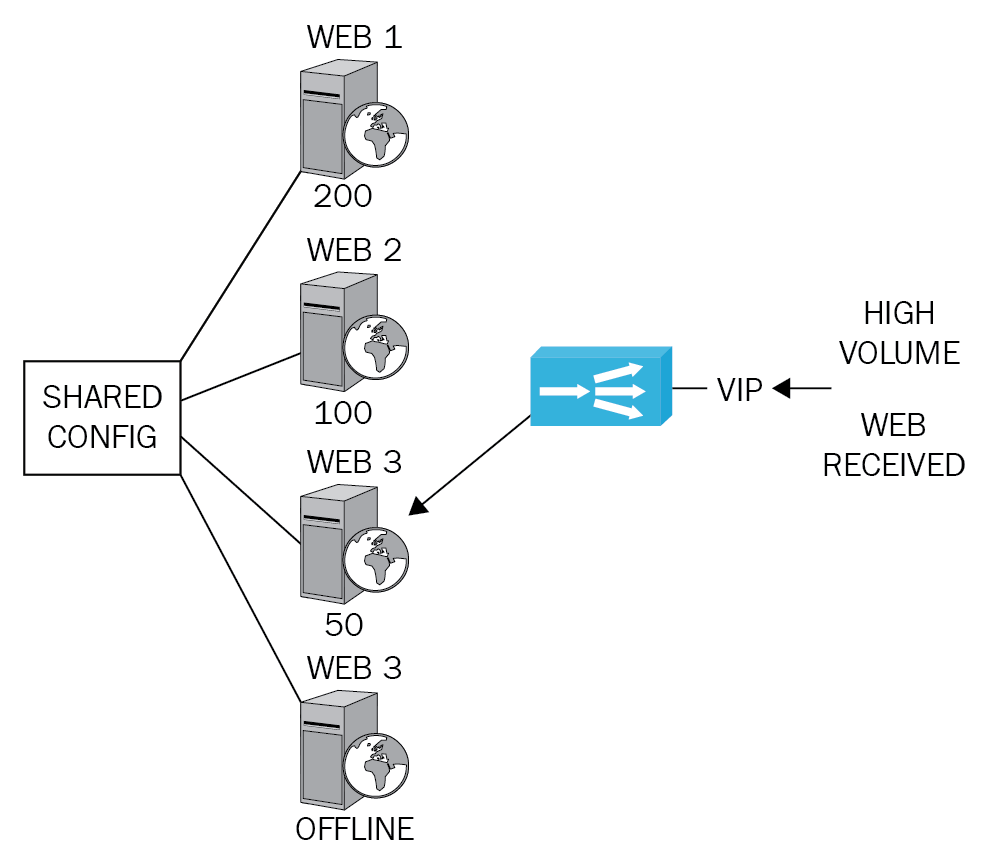
Figure 12: Load balancer
-
Least utilized host: The benefits of a load-balancer are that it knows the status of all of the web servers in the server farms and knows which web servers are the least utilized by using a scheduling algorithm.
The load balancer has selected to send the request to Web 3, which has the least number of requests (50), and Web 4 will not be considered as it is currently offline. A user requesting three different pages may obtain them from different web servers but may not know this as the load balancer is optimizing the delivery of the web pages to the user.
-
Affinity: When the load balancer is set to Affinity, the request is sent to the same web server based on the requestor's IP address. The reason for this is that maybe in one region there is limited bandwidth for other web servers in the server farm.
-
DNS round robin: The load balancer could be set to use DNS round robin as in Figure 13:
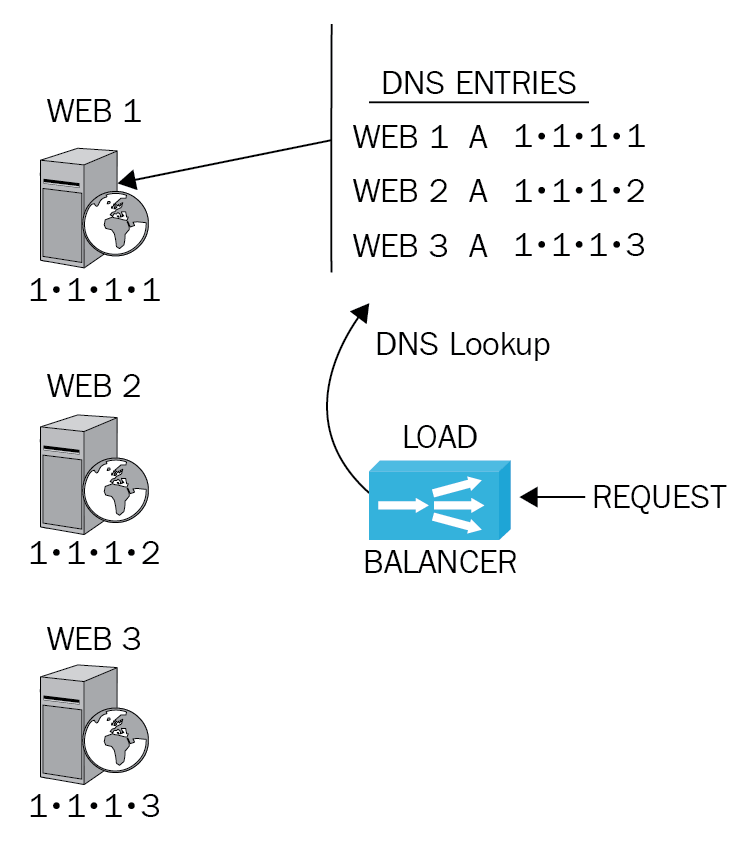
Figure 13: DNS Round Robin
While using DNS round robin when the request comes in, the load balancer contacts the DNS server and rotates the request based on the lowest IP address first, rotates around Web 1, 2, and 3, and then keeps the sequence going by going back to Web 1 on a rotational basis.
Clustering
Clustering is where two servers share a quorum disk on the backend. The normal setup is the active-passive configuration, as shown in Figure 14, and it is commonly used for email or database servers:
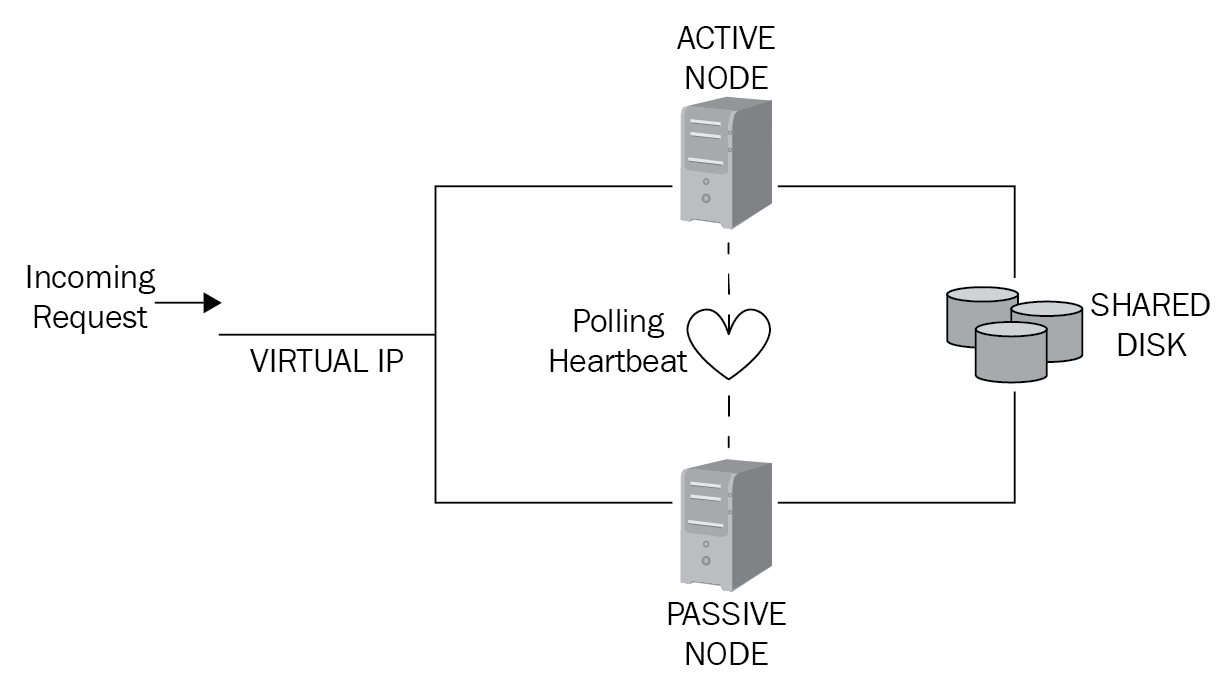
Figure 14: Clustering.
In the preceding diagram, the request comes to the Virtual IP that sends the request to the active node that fulfils the request. In the background, the passive node is also connected to the shared disk, but has a heartbeat polling the active node. If the active node fails, the passive takes over.
The other mode of clustering is where both nodes are active in an active-active configuration. With this configuration, both nodes need to have enough resources to act as a dual active node without suffering from a bottleneck.
Data-loss prevention
Data Loss Prevention (DLP) can stop unencrypted sensitive and personally identifiable information (PII) from inadvertently leaving the company. It cannot scan encrypted data. There are two separate ways it can prevent data loss:
-
USB flash drive: DLP can be set up on a file server to prevent data being copied onto a USB flash drive.
-
Email: Templates can be set up with regular expressions to stop data being sent out in email format.
Example:
An auditor has found that the credit card details of customers have been sent out of the company by email, and this needs to be prevented in the future. The company only accepts VISA, Mastercard, and American Express.
The solution would be to set up a DLP template with the regular expression format for VISA, Mastercard, and American Express. As emails leave the company, they are scanned for this format and if it is included in an email, it is blocked and the security administrator is informed.
Exam tip:
DLP prevents PII and sensitive data from being inserted into an email or copied onto a USB flash drive.

