Users Online
· Guests Online: 13
· Members Online: 0
· Total Members: 204
· Newest Member: meenachowdary055
· Members Online: 0
· Total Members: 204
· Newest Member: meenachowdary055
Forum Threads
Newest Threads
No Threads created
Hottest Threads
No Threads created
Latest Articles
Articles Hierarchy
13 IDaaS-2
This set of Cloud Computing Interview Questions and Answers for experienced people focuses on IDaaS
1. Any software application that complies with the standard accepts an _______ that is authenticated by a trusted provider.
a) OpenID
b) OpenUser
c) OpenSSD
d) None of the mentioned
2. Point out the wrong statement :
a) XML checks the ID request against its policies and either allows or denies the request
b) SPML in most instances operates as a reply/request mechanism
c) User centric authentication takes place usually in the form of knowledge cards
d) All of the mentioned
3. Which of the following allows a distributed ID system to write and enforce custom policy expressions ?
a) XACML
b) XML
c) SOAP
d) None of the mentioned
4. _________ is a standard of OASISs PSTC that conforms to the SOA architecture.
a) XACML
b) SPML
c) SML
d) All of the mentioned
5. Point out the wrong statement :
a) Distributed transaction systems such as internetworks or cloud computing systems magnify the difficulties faced by identity management systems
b) The Distributed Audit Service provides accountability for users accessing a system
c) The OpenID and CardSpace specifications support authentication type of data object
d) None of the mentioned
6. Which of the following standard is concerned with the exchange and control of identity information ?
a) IGK
b) IDF
c) IGF
d) All of the mentioned
7. _______ is a Microsoft software client that is part of the companys Identity Metasystem and built into the Web Services Protocol Stack.
a) IHA
b) EHA
c) CardSpace
d) None of the mentioned
8. The _______ Open Source Identity Framework is used to create a vendor-neutral cloud-based authentication service.
a) Higgins
b) Hughes
c) Hinges
d) All of the mentioned
9. Which of the following is authorization markup language ?
a) eXtensible Access Control Markup Language
b) intrinsic Access Control Markup Language
c) hypertext Access Control Markup Language
d) All of the mentioned
10. Which of the following should come in place of question mark for the following figure ?
Attribute Insertion-IDaaS
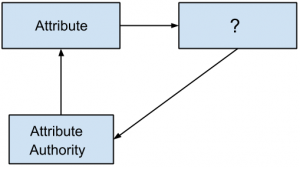
a) Policy Enforcement Point
b) Policy Decision Point
c) Policy Insertion Point
d) All of the mentioned
1. Any software application that complies with the standard accepts an _______ that is authenticated by a trusted provider.
a) OpenID
b) OpenUser
c) OpenSSD
d) None of the mentioned
2. Point out the wrong statement :
a) XML checks the ID request against its policies and either allows or denies the request
b) SPML in most instances operates as a reply/request mechanism
c) User centric authentication takes place usually in the form of knowledge cards
d) All of the mentioned
3. Which of the following allows a distributed ID system to write and enforce custom policy expressions ?
a) XACML
b) XML
c) SOAP
d) None of the mentioned
4. _________ is a standard of OASISs PSTC that conforms to the SOA architecture.
a) XACML
b) SPML
c) SML
d) All of the mentioned
5. Point out the wrong statement :
a) Distributed transaction systems such as internetworks or cloud computing systems magnify the difficulties faced by identity management systems
b) The Distributed Audit Service provides accountability for users accessing a system
c) The OpenID and CardSpace specifications support authentication type of data object
d) None of the mentioned
6. Which of the following standard is concerned with the exchange and control of identity information ?
a) IGK
b) IDF
c) IGF
d) All of the mentioned
7. _______ is a Microsoft software client that is part of the companys Identity Metasystem and built into the Web Services Protocol Stack.
a) IHA
b) EHA
c) CardSpace
d) None of the mentioned
8. The _______ Open Source Identity Framework is used to create a vendor-neutral cloud-based authentication service.
a) Higgins
b) Hughes
c) Hinges
d) All of the mentioned
9. Which of the following is authorization markup language ?
a) eXtensible Access Control Markup Language
b) intrinsic Access Control Markup Language
c) hypertext Access Control Markup Language
d) All of the mentioned
10. Which of the following should come in place of question mark for the following figure ?
Attribute Insertion-IDaaS

a) Policy Enforcement Point
b) Policy Decision Point
c) Policy Insertion Point
d) All of the mentioned
Page 1 of 2: 12
Comments
No Comments have been Posted.
Post Comment
Please Login to Post a Comment.

