Users Online
· Members Online: 0
· Total Members: 188
· Newest Member: meenachowdary055
Forum Threads
Latest Articles
Articles Hierarchy
What Are The Different Types Of Network Security?
What Are The Different Types Of Network Security?
Chances are you’ve heard of the most common vulnerabilities, and how a breach can lead to financial loss or damage to an organization’s reputation.
Truthfully, the only way to protect your business and customer information is to restrict access to confidential files, networks, and other digital resources.
This is where network security comes into play.
The common types of network security include
- Network Access Control,
- IT Security Policies,
- Application Security,
- Vulnerability Patch Management,
- Network Penetration Testing,
- Data Loss Prevention,
- Antivirus Software,
- Endpoint Detection And Response (EDR),
- Email Security,
- Wireless Security,
- IDS/IPS,
- Network Segmentation,
- SIEM,
- Web Security,
- Multifactor Authentication (MFA), and a
- Virtual Private Network (VPN).
Network security is important now more than ever as threat actors seek ways to exploit the global pandemic and work at home culture of 2021 for financial gain.
But how do you get started? What is the fastest and most cost-effective way to build a secure network that will prevent the top cyber attacks?
In this article, I’m going to explain what network security is and why it’s important.
Next, we will examine the different components an organization should be familiar with in order to implement an effective network security program.
Finally, I’ll provide actionable tips you can take to harden the security of your network and systems.
Article Navigation
- What Is Network Security?
- Why Is Network Security Important?
- What Are The Types Of Network Security?
- Top Network Security Threats In 2021
What Is Network Security?
Network security is a combination of technologies, devices, and processes designed to protect an organization’s network infrastructure from unauthorized access, exploitation of its corporate resources, improper disclosure, and denial of services.
The methods a company implements to protect its network may vary from one organization to the next.
However, the main goal of network security is common for any business – ensure the confidentiality of corporate information, secure the integrity of data, and ensure access to corporate resources is always available.
Network Security is a critical component that an organization must implement in order to protect its interests and operate efficiently.
The financial success of an organization today is not totally dependent on savvy marketing techniques and cash flow.
The internet allows for instant communication and lightning speed transactions which businesses rely on today.
In contrast, cyber criminals and hackers are continuously developing methods to disrupt, steal, and compromise this flow of data as it travels on the information superhighway.
Read More: How To Develop & Implement A Network Security Plan
Why Is Network Security Important?
2020 was a year filled with extraordinary trends and unexpected occurrences around the world.
The pandemic literally has changed the way businesses operate. Many employees who once occupied cubicles or open-space desks are now working remotely for an undetermined time period.
Interestingly, businesses that have the means to provide the technology to support a remote workforce have adapted very well, and many eCommerce businesses continue to be profitable.
Although many organizations have met the challenge and have embraced a remote workforce, this trend has not deterred the presence of cyber attacks, in fact, it has simply provided another opportunity for threat attackers.
Ransomware attacks increased 148% over baseline levels from February 2020. This increase is primarily the result of direct attacks against home-based users.
The servers, databases, web applications, and cloud applications have not moved, however, the employees who access them are now remote.
Organizations must be diligent in training employees to be security-aware while at the same time ensuring that the necessary security controls are in place.
What Are the Different Types of Network Security?
The different types of network security include:
- Network Access Control
- Network Security Policies
- Application Security
- Vulnerability Patch Management
- Network Penetration Testing
- Data Loss Prevention
- Antivirus Software
- Endpoint Detection And Response (EDR)
- Email Security
- Wireless Security
- IDS/IPS
- Network Segmentation
- SIEM
- Web Security
- Multifactor Authentication (MFA)
- Virtual Private Network (VPN)
Network Access Control
With organizations embracing Bring Your Own Device (BYOD) politices, it is critical to have a solution that provides the visibility, access control, and compliance capabilities that are required to strengthen your network security infrastructure.
Network Access Control or NAC is a network solution that enables only compliant, authenticated, and trusted endpoint devices to access network resources and infrastructure.
A NAC system utilizes MAC address control and the SNMP protocol to deny network access to non-compliant devices, place them in a quarantined area, or give them only restricted access to computing resources, thus keeping insecure nodes from infecting the network.
A NAC solution can also isolate guests from your internal network, identifying all devices inserted into network switch ports, and can disable a rogue device from the switch port remotely without engaging tech support.
Network Security Policies
A network security policy is a set of standardized practices and procedures that outlines rules for network access, the architecture of the network, and determines how policies are enforced.
Having a network security policy is important because it informs the employees of an organization the requirements for protecting assets within the infrastructure.
These assets take many forms, such as passwords, documents, or even servers. These policies also establish guidelines for acquiring, configuring, and auditing computer systems and networks.
A network security policy that is easily interpreted and enforced can protect the network from accidental or intentional data loss, lessen the risk of cyber-attacks, and preserve the integrity of corporate data.
Application Security
Application security is the process of developing, adding, and testing security features within applications to prevent security vulnerabilities against threats such as unauthorized access and modification.
According to Veracode’s State of Software Security report, 83% of the 85,000 applications it tested had at least one security flaw.
Many had much more, as their research found a total of 10 million flaws, and 20% of all apps had at least one high severity flaw.
It is important for organizations to perform routine application security testing to identify and mitigate flaws in code.
This will deter cyber-attackers from compromising or exploiting critical web applications.
Vulnerability Patch Management
Vulnerability patch management is a continuous process of identifying, prioritizing, remediating, and reporting on security vulnerabilities in systems.
Assets on the network are discovered, categorized, and reported on to remediate security vulnerabilities on target systems.
Vulnerability patch management is critical today because attackers are constantly crawling the internet looking for vulnerabilities to exploit—and taking advantage of old vulnerabilities that are unpatched on corporate systems.
As highlighted in our 2021 security trends report, patch management will become a priority for the C-suite in 2021 as they look for cost-effective solutions to mitigate the costly risk of a breach.
Network Penetration Testing
Network penetration testing is an attempt to measure and evaluate the security of an IT infrastructure by safely trying to exploit vulnerabilities.
These vulnerabilities may exist in operating systems, services and application flaws, improper firewall configurations or risky end-user behavior.
A primary reason why penetration testing is important to an organization’s cyber security program is that it helps personnel learn how to handle cyber-attacks from a malicious entity.
Penetration testing also serves to examine whether an organization’s security policies are functional and effective in deterring attacks.
Data Loss Prevention
Data loss prevention is defined as a strategy that detects potential data breaches or data ex-filtration transmissions and prevents them by monitoring, detecting and blocking sensitive data while in use (endpoint actions), in-motion (network traffic), and at rest (data storage).
A primary reason DLP is important because it helps to detect or prevent the exposure of sensitivity to unintended recipients.
Depending upon the DLP software and policy configuration, DLP can alert the end-user via popup or email message.
This customization deters the leakage of data whether the activity is accidental or malicious.
Antivirus Software
Antivirus software is a type of software used to prevent, scan, detect and delete viruses from a computer.
Once installed, most antivirus software will run automatically in the background to provide real-time protection against virus attacks.
An untold number of new viruses are discovered daily, so it is important and critical to have antivirus software installed and configured to automatically update to the latest detection files to stay ahead of the tons of malicious code running rampant on the internet.
Malware creators today are truly knowledgeable on how to exploit weaknesses in computer systems.
Anti-virus software can be deployed as the first layer of defense to prevent computer systems from becoming infected by a virus.
Endpoint Detection and Response (EDR)
Endpoint detection and response technology is defined as a solution that continuously records system activities and events taking place on endpoints.
EDR provides security teams with the visibility, they need to uncover incidents that would otherwise remain invisible.
EDR is important because it provides a graphical view of how the attacker gained access to the system and what they did once they were inside.
EDR can detect malicious activity on an endpoint as a result of zero-day exploits, advanced persistent threats, fileless or malware-free attacks, which do not leave signatures and can, therefore, evade legacy anti-virus.
Email Security
Email security is a term that describes different procedures and techniques for protecting email accounts, content, and communication against unauthorized access, loss or compromise.
Email is often used to spread malware, spam, and phishing attacks.
It is important for an organization to implement email security to protect against the many forms of cyber-attacks through email, as well as ensure sensitive messages are encrypted as they transit out of the network to the recipient.
Wireless Security
Wireless security is defined as the protection of unauthorized access and malicious attempts to a wireless or Wi-Fi network.
Implementing strong wireless security is important today since many organizations allow their employees to work remotely and connect to the internet over a wireless network.
WiFi is highly susceptible to hacking if weak wireless protocols are enabled. A wireless network designed with current wireless security protocols, such as WPA2 can deter cyber-attacks.
Read more: How To Perform A Wireless Penetration Test
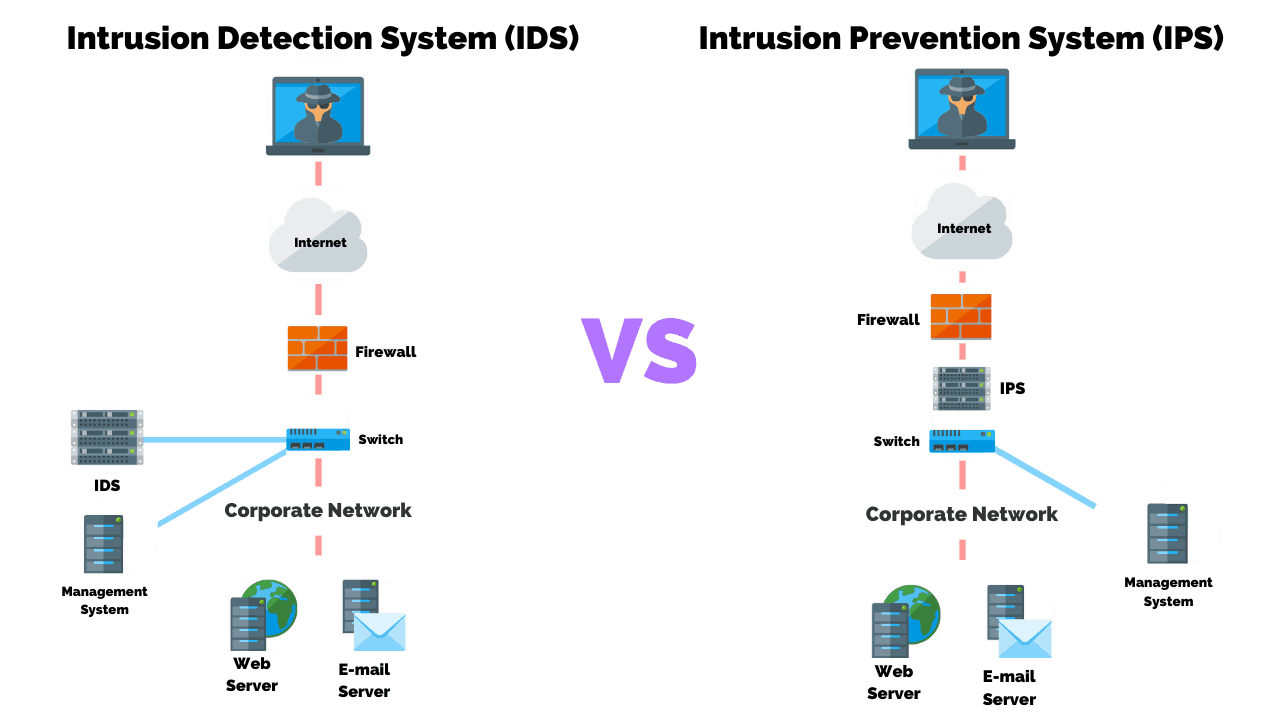
Intrusion Prevention System/Intrusion Detection System (IPS/IDS)
An IPS/IDS are network security measures that are deployed in a network to detect and stop potential incidents. The terms are usually linked together but are distinct in functionality.
The main difference between an intrusion detection system (IDS) and an intrusion prevention system (IPS) is that an IDS is used to monitor a network, which then sends alerts when suspicious events on a system or network are detected.
An IPS reacts to attacks in progress with the goal of preventing them from reaching targeted systems and networks.
An IPS/IDS are critical pieces to the security infrastructure of an organization because one device can detect and report an attack while the other can stop attacks based on security policies.
In modern networking equipment, it is common for both technologies to be combined into a single Unified Threat Management appliance.
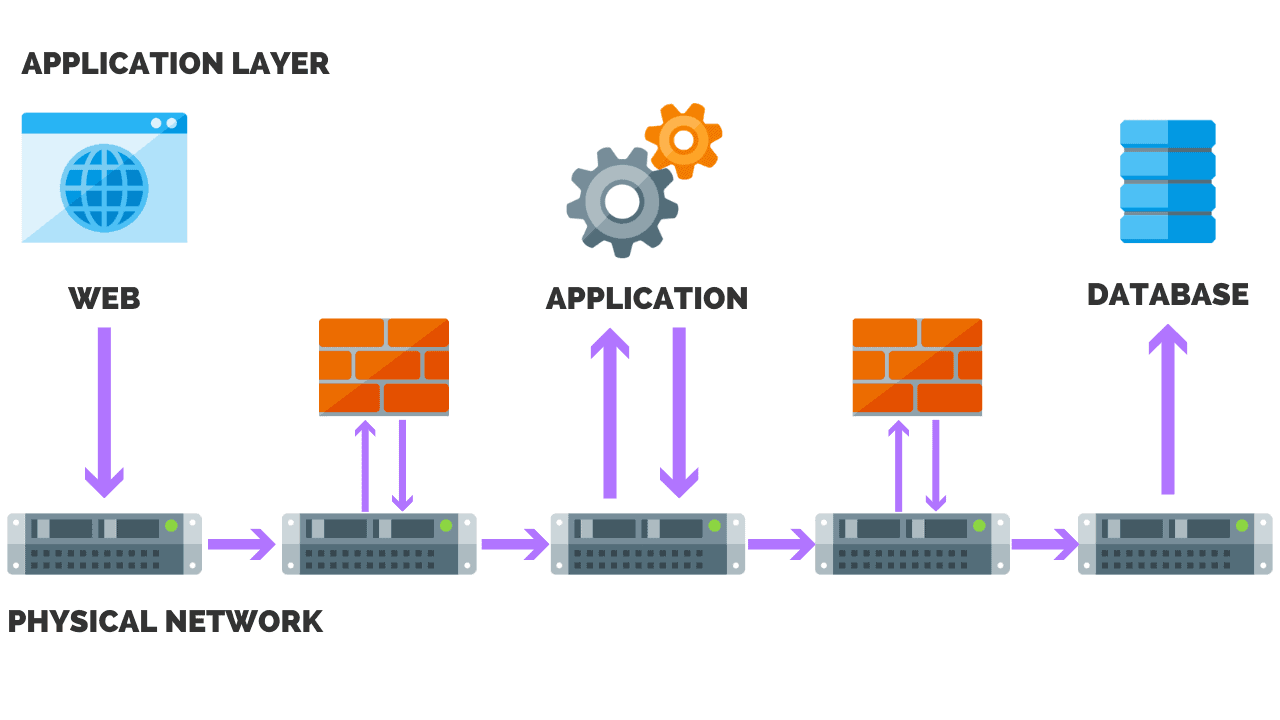
Network Segmentation
Network segmentation is an architectural approach that divides a network into multiple segments or micro subnets, each acting as its own small network.
This allows network administrators to control the flow of traffic between subnets based on granular policies.
Network segmentation is important because it allows organizations to not only improve monitoring, and performance but most importantly to enhance network security.
Network segmentation can prevent malware from spreading by isolating a network in one area, while keeping another segment of the network protected.
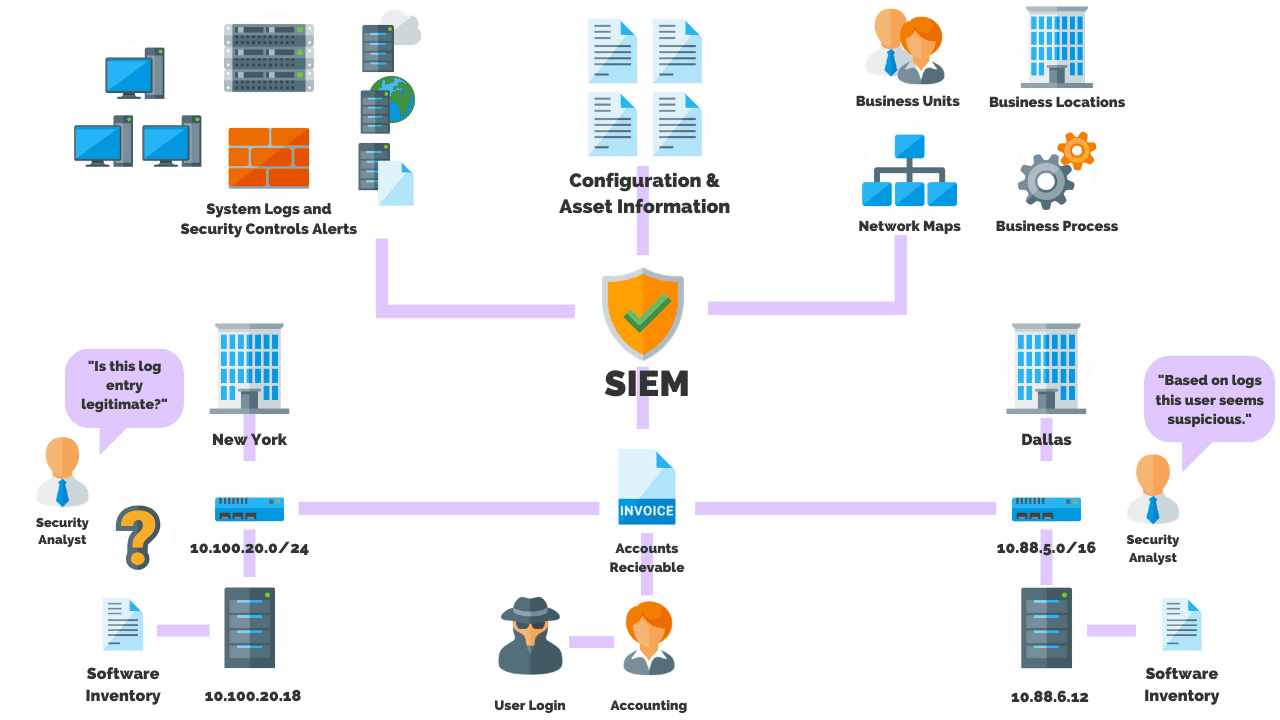
SIEM
A Security Information and Event Management (SIEM) solution supports threat detection, compliance and security incident management through the collection and analysis (both near real-time and historical) of security events, as well as a wide variety of other event and contextual data sources.
A SIEM has three main core features which make it important for an organization.
These features include the detection of incidents to create an attack timeline, manage incidents, and is a log source that meets compliance and regulatory requirements.
Web Security
 Web security is defined as the protection of a web application that is exposed to the Internet.
Web security is defined as the protection of a web application that is exposed to the Internet.
The level protection encompasses tools or resources that detect, prevent, and respond to cyber threats.
It is not uncommon for a business to have a website presence on the Internet.
Many organizations advertise to the public its services, provide a convenient means for accepting online payments, and exchanging personal information.
Web security is important because it protects an organization’s identity and reputation.
Strategies to deter attacks and strengthen web security include – secure coding techniques, ensuring web site supports only current SSL/TLS protocols, frequent web application/vulnerability scanning, and penetration testing.
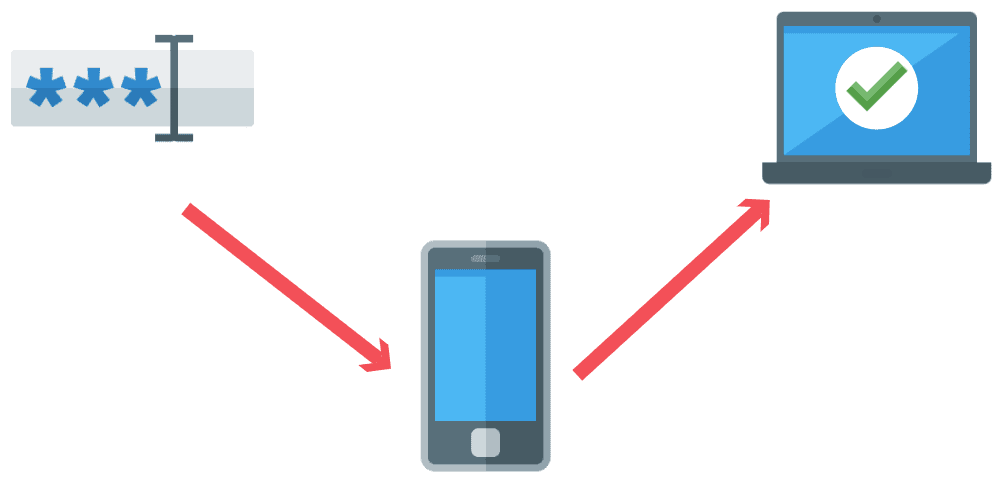
Multifactor Authentication (MFA)
Multifactor Authentication, or commonly referred to as MFA is an authentication system that requires more than one distinct authentication factor for successful authentication.
Multifactor authentication can be performed using a multifactor authenticator or by a combination of authenticators that provide different factors.
The three authentication factors are something you know, something you have, and something you are.
MFA is important because if your username and password is stolen through a data breach, the cyber attacker would not have the additional authentication factor to complete the authentication.
Example of authentication factors are:
- Something you know – Password/PIN.
- Something you have – Hardware/Software Token issued by your organization.
- Something you are – Biometric (Fingerprint, IRIS/Retina Scan).
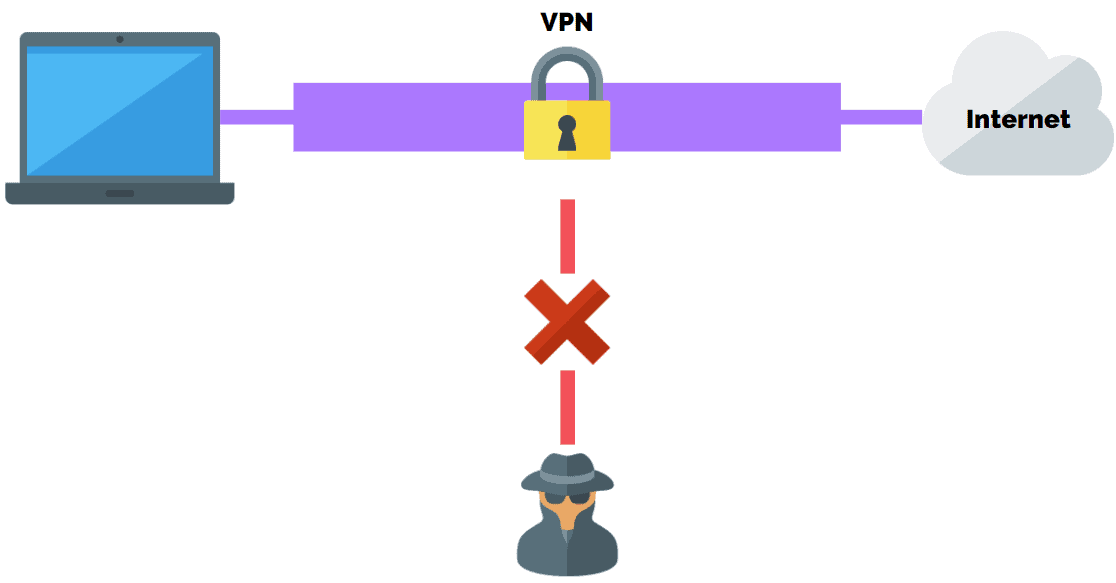
Virtual Private Network (VPN)
A Virtual Private Network, or VPN, is an encrypted connection over the Internet from a device to a network.
The encrypted connection helps ensure that sensitive data is safely transmitted.
It prevents unauthorized people from eavesdropping on the traffic and allows the user to conduct work remotely.
Per the definition, VPN’s are important for business and consumers.
An organization may include a standard VPN package for their remote employees to connect to their office network as if they were in the office.
The VPN provides a secure tunnel between the VPN client and the organization’s VPN server, which prevents the cyber attacker from seeing sensitive information.
Top Network Security Threats In 2021
Now that you have a better understanding of the current tools security professionals use, let’s dive into some of the top threats that are expected to trend in 2021 and how they are expected to impact network security.
Social Engineering
 Social engineering is a manipulation technique that exploits human error to gain private information, access, or valuables.
Social engineering is a manipulation technique that exploits human error to gain private information, access, or valuables.
The common forms of social engineering include:
- Phishing – Refers to an attack that is usually sent in the form of a link embedded within an email. The message is disguised and looks like an email from a reliable source, but it is usually a link to a malicious site.
- Vishing – This attack attempts to trick victims into giving up sensitive information over the phone. In most cases, the attacker strategically manipulates human emotions, such as fear, sympathy, and greed in order to accomplish their goals.
- Smishing – A cyber-attack that uses SMS text messages to mislead its victims into providing sensitive information to a cybercriminal.
Unpatched Vulnerabilities
 Unpatched vulnerabilities refer to a program or software code that contains a flaw.
Unpatched vulnerabilities refer to a program or software code that contains a flaw.
The flaw or bug in the code is usually made public. This allows a cyber attacker to execute their malicious code against the known flaw.
Once successful, the attacker will crawl and search for vulnerable systems, with the goal of exploiting the system.
In 2021, it is estimated that most of the attacks will exploit known vulnerabilities in targeted systems.
In response to the ongoing COVID-19 pandemic, a growing number of organizations will allow its employees to remotely access their resources, thus enlarging their surface of attacks.
Unpatched systems and poorly protected access points will allow threat actors to compromise many companies.
Ransomware
Ransomware is a type of malicious software designed to block access to a computer system until a sum of money is paid.
Increasing pressure to submit to extortion, targeting of the most vulnerable victims, and tactics that make it more difficult to recover encrypted data will keep ransomware the most profitable “line of business” for cybercriminals in 2021 and the single biggest threat for all organizations.
Learn More: How To Prevent Ransomware Attacks: An Expert Guide
Insider Threats
An insider threat is defined as the threat that an employee or a contractor will use his or her authorized access, wittingly or unwittingly, to do harm to the security of their employer.
According to the 2020 Verizon Data Breach report, insiders were responsible for a data breach in 30% of cases. With employees working from home today due to the COVID-19 pandemic, employers cannot physically see what their employees are doing.
Therefore, it can be assumed that the number of insider threats will increase by more than 20% in 2021.
Conclusion
In this article, we defined Network Security and examined current trends expected for 2021.
Due to the uncertainty of the pandemic which dominated the world scene in 2020, many cybersecurity initiatives have shifted to the securing of the remote worker.
We also reviewed common Network Security types.
Although not an exhaustive list of all network security types, organizations at a minimum should have controls in place to address each type in order to secure their network and deter attacks from cyber criminals.
More than ever before, opportunities exist for security teams to be innovative in their approach for securing the network.
As we settle into 2021, stay vigilant and attentive to the trends in cyber security to benefit your organization.


