Users Online
· Members Online: 0
· Total Members: 188
· Newest Member: meenachowdary055
Forum Threads
Latest Articles
Articles Hierarchy
What Is Data Loss Prevention (DLP)?
What Is Data Loss Prevention (DLP)?
Data Loss Prevention is defined as a strategy that detects potential data breaches or data ex-filtration transmissions and prevents them by monitoring, detecting and blocking sensitive data while in use (endpoint actions), in-motion (network traffic), and at rest (data storage).
Data Loss Prevention is also synonymous with the term Data Leakage Prevention. These terms are often used interchangeably, however, Data Loss Prevention is the common term used by DLP solution providers today.
Understanding Sensitive Data
Sensitive data is information that must be protected against unauthorized access to safeguard the privacy or security of an individual or organization. It can exist within entries on a spreadsheet containing employee names and Social Security numbers.
Sensitive data may be the contents of a document describing the secret formula for a brand of soda, or it could be a database that contains the full names, addresses, and driver license numbers for a state’s DMV.
One of the core functions of a DLP strategy and solution is to prevent exposing sensitive data to unauthorized parties.
Organizations today are faced with the challenge of selecting the best security solutions.
This includes implementing a SIEM and IDS/IPS to protect their corporate data.
This is because the unintentional leakage or loss of sensitive data due to a malicious actor, an inside job, or an unknowing employee, can lead to significant financial loss and reputational damage to any organization.
What Is The Average Cost Of A Data Breach?
The average cost of a data breach to companies worldwide is $3.86 million. As business growth continues to rise domestically and globally, expect the threat landscape to increase proportionately.
The five-year trend report below reveals the estimated amount of revenue lost in a single data breach, prompting the need for organizations to invest in some form of data loss prevention technology.
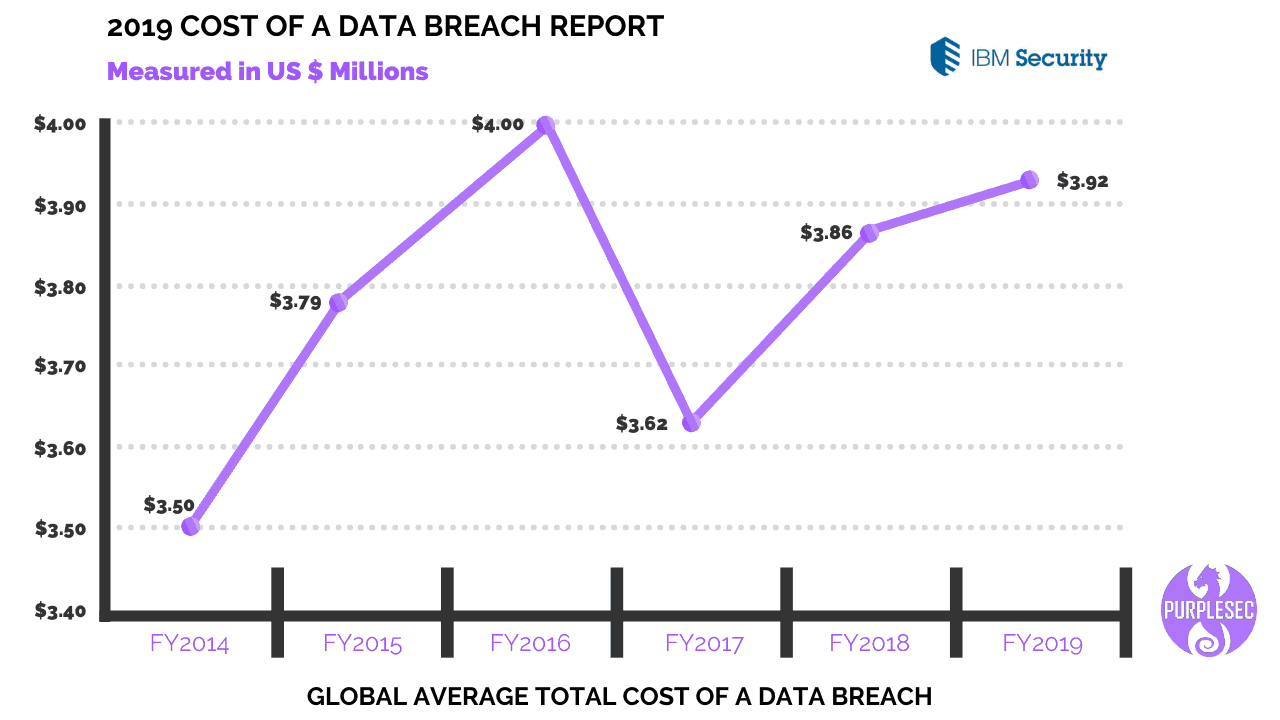
The global average total cost of a single a data breach worldwide is:
- 2014 – $3.50 million
- 2015 – $3.79 million
- 2016 – $4.00 million
- 2017 – $3.62 million
- 2018 – $3.86 million
- 2019 – $3.92 million
What factors attribute to the global average statistics for the cost of a data breach?
Regulatory and compliance standards. For example, a healthcare company is responsible for the secured handling of personal health data of individuals (PHI). HIPAA regulations require that an institution protect the identity of patient data.
Loss of data in this area can result in fines, ranging from $100 to $50,000 per violation.
A credit card processing company has thousands of customer credit card numbers in a file and needs to ensure that the data is encrypted at rest in a storage location, or in transit to the Internet. If consumer data is not encrypted end to end and compromised, the institution could possibly violate compliance as set forth in PCI DSS requirements.
Loss of data in this area is subject to fines ranging from $5,000 to $100,000 per month.
To avoid severe financial loss and negative press, implementing some form of DLP is a compliance requirement for an organization subject to HIPAA, PCI DSS, ITAR, GDPR, and other regulations. In the next section, we’ll examine how DLP works and how to create a successful DLP strategy.
How Does A DLP System Work?
Prior to creating a DLP strategy, we need to first understand what the core components of DLP are and how they work.
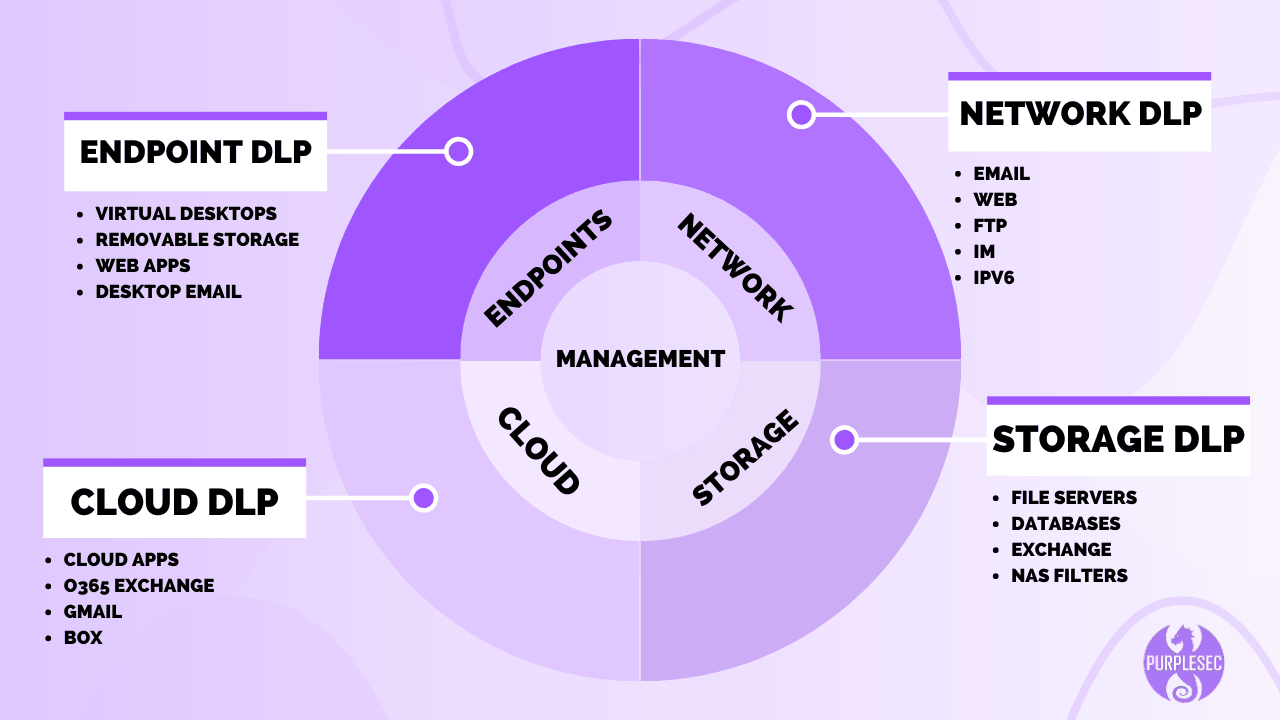
The core components of DLP software have not changed since the early days of DLP, with the exception of DLP for the cloud. More companies are storing their data off-premise in the cloud utilizing Amazon, Azure or Google containers.
- DLP for the Endpoint: Data residing on the desktop, laptop, USB storage, virtual desktops.
- DLP at Rest or for Storage: Usually unstructured data residing on a server or structured data residing on Databases.
- DLP for Network: Data that transits or leaves the network to the Internet.
- DLP for Cloud: Data residing on Google Drive, Office 365 email, personal email providers.
The software is designed to discover, analyze content and context in order to determine if the data presented matches a pattern or expression of a:
- Social Security Number
- Credit Card Number
- HIPAA Term
- Or Keyword
Once the pattern is matched, a violation or alert can be generated. The alert is sent to a management console for review by a support analyst and incident triage.
Now let’s take a closer look at the concept of pattern matching.
Pattern Matching
The concept of understanding DLP is not complex at all. The basic premise is understanding the differences between content awareness and contextual analysis.
A simple way to understand the difference is to consider a letter in an envelope.
The content represents a letter and the context is the envelope. Content awareness involves capturing the envelope and analyzing the content, while the context includes outside factors like size, format, and header, anything that doesn’t include the content of the letter.
The idea behind content awareness is that although we want to use the context to gain more intelligence on the content, we don’t want to be restricted to a single context.
The distinguishing factor amongst the various DLP vendors is the content engine.
This article is not intended to deliver an exhaustive methodology used by all DLP vendors, but let’s take a look at the basic methods used by most DLP vendors.
The science behind the core protections of a DLP system are regular expressions usually referred to as regex. Regex are special strings representing a pattern to be matched in a search operation.
You can use alphanumeric patterns to configure custom dictionaries that match a wide variety of data types. For example, you can define patterns to detect Personal Identifiable Information (PII), driver’s license numbers, credit card numbers, or social security numbers.
One of the most common patterns detected by a DLP is the Social Security Number.
As an example, note how Microsoft utilizes regex and keyword matching to detect Social Security Number patterns:
<Entity id=”a44669fe-0d48-453d-a9b1-2cc83f2cba77″
patternsProximity=”300″ RecommendedConfidence=”85″>
<Pattern confidenceLevel=”85″>
<IdMatch idRef=”FormattedSSN” />
<Any minMatches=”1″>
<Match idRef=”SSNKeywords” />
<Match idRef=”USDate” />
<Match idRef=”USAddress” />
<Match idRef=”Name” />
</Any>
</Pattern>
</Entity>
- Regex matches a formatted SSN (and it’s in the valid SSN range)
- Corroborative Evidence one of the following must occur nearby:
- Keyword match {Social Security, Soc Sec, SSN, SSNS, SSN#, SS#, SSID}
- Text representing a US address
- Text representing a date
- Text representing a name
By utilizing regex patterns and the use of keywords within a dictionary, various vendors have created their DLP products based on the application constructs above.
Another common technique used by DLP vendors is the concept of fingerprinting.
Fingerprinting
Fingerprinting is performed by algorithms that map data such as documents and files to shorter text strings. These fingerprints are unique identifiers for their corresponding data and files, much like human fingerprints uniquely identify individual people.
Document fingerprinting is especially useful for identifying sensitive data within forms, including government forms such as tax documents, HIPAA and other regulatory compliance forms, employee documentation forms used by finance or human resources, and other proprietary forms that a business may use, such as customer order forms or contracts.
By extending data fingerprinting to forms, traditional DLP solutions can detect sensitive data such as social security numbers, credit card numbers, and healthcare information within those forms. Recognizing when these documents contain pieces of sensitive data, it enables DLP solutions to secure those documents during transit to a web application or via email.
Symantec DLP has a combination of advanced technologies that can accurately detect all of the confidential data in your organization—whether it’s at rest or in motion.
The detection technologies in Symantec DLP include:
- Exact Data Matching (EDM) – EDM detects content by fingerprinting structured data sources, including databases, directory servers, or other structured data files.
- Indexed Document Matching (IDM) – IDM applies fingerprinting methods to detect confidential data stored in unstructured data, including Microsoft Office documents; PDFs; and binary files such as JPEGs, CAD designs, and multimedia files. IDM also detects “derived” content, such as text that has been copied from a source document to another file.
As stated, many DLP products use a discovery engine that crawls the data, indexes it and makes it accessible through an intuitive interface. This allows quick searching on data to find its sensitivity and ownership details.
What Are the Top DLP Best Practices?
The top DLP best practices include:
- Identifying the crown jewels
- Researching multiple vendors
- Defining incident response and remediation
- Crawling, walking, and running
- Perform a proof of concept exercise
- Identifying the DLP stakeholders and support team
- Informing stakeholders of the state of the DLP program

1. Identify The Crown Jewels
Know thy business. Identify the proverbial ‘crown jewels’ of your company. This could be Intellectual Property such as a recipe, source code, or formula.
Engage Executive and Senior Leadership to direct the DLP program by providing input on what is critical to the organization. This approach is referred to as the ‘top-down’ approach.
Input from technical leaders can be shared during the maturation of the DLP program in order to enhance value and creativity.
2. Research Multiple Vendors
Define your expectations for DLP in your organizations. Consult with peers in your industry and find out who they are using for DLP and gauge their satisfaction with support, incident workflow, and overall confidence level.
Gartner can also be used as a reference to determine how the DLP vendor has performed over time.

3. Define Incident Response And Remediation
Enterprise DLP is not simply a tool, it is a program. The downfall of many DLP installations is poor planning for incident triage.
It is not unusual for an organization to go through the strategy process, purchase the software, and fail to plan for DLP incident management.
Ensure there is an incident response plan and team in place before going live with the implementation.
4. Crawl, Walk, and Run
I recall working on my first deployment of Vontu/Symantec DLP. One of their sales engineers mentioned the phrase, do not boil the ocean right out of the gate.
He was advising us to go for small wins, instead of turning on every single policy checkbox available.
Doing so would overwhelm the system and inundate the system with massive amounts of incidents, therefore, defeating the purpose of the investment. Same principle applies a decade later.
Start with a small subset of policies and demonstrate value to leadership, then gradually build the system over time as your understanding of the product matures.
5. Perform A Proof Of Concept Exercise
The goal here is to replicate functionality and test the feature sets.
This can also be compared to as a pilot. This is the time to kick the tires and ensure the product meets your compliance needs and observe deficiencies in your triage process.
6. Identify The DLP Stakeholders And Support Team
I t is not surprising to hear many organizations have DLP in the environment and barely utilize the features or have support teams to manage incidents.
t is not surprising to hear many organizations have DLP in the environment and barely utilize the features or have support teams to manage incidents.
Create an internal DLP Committee, comprised of Senior Leaders, Business Unit Managers, Legal, and InfoSec Management.
If internal resources are not available to support DLP Operations, consider partnering with a Managed Service Provider that specializes in DLP.
7. Regularly Inform Stakeholders Of The State Of The DLP Program

Ensure stakeholders are informed of the state of the program.
Consider creating a DLP committee comprised of Executive Leadership members and key Business Unit leaders.
Monthly or quarterly meetings will provide input and will help to continuously drive the program and ensure the quality of the investment is operating optimally.
When Do You Need A DLP Strategy?
A DLP strategy can commence once executive leadership is on board with the solution. This usually takes place after a vulnerability assessment or cost-benefit analysis has been performed.
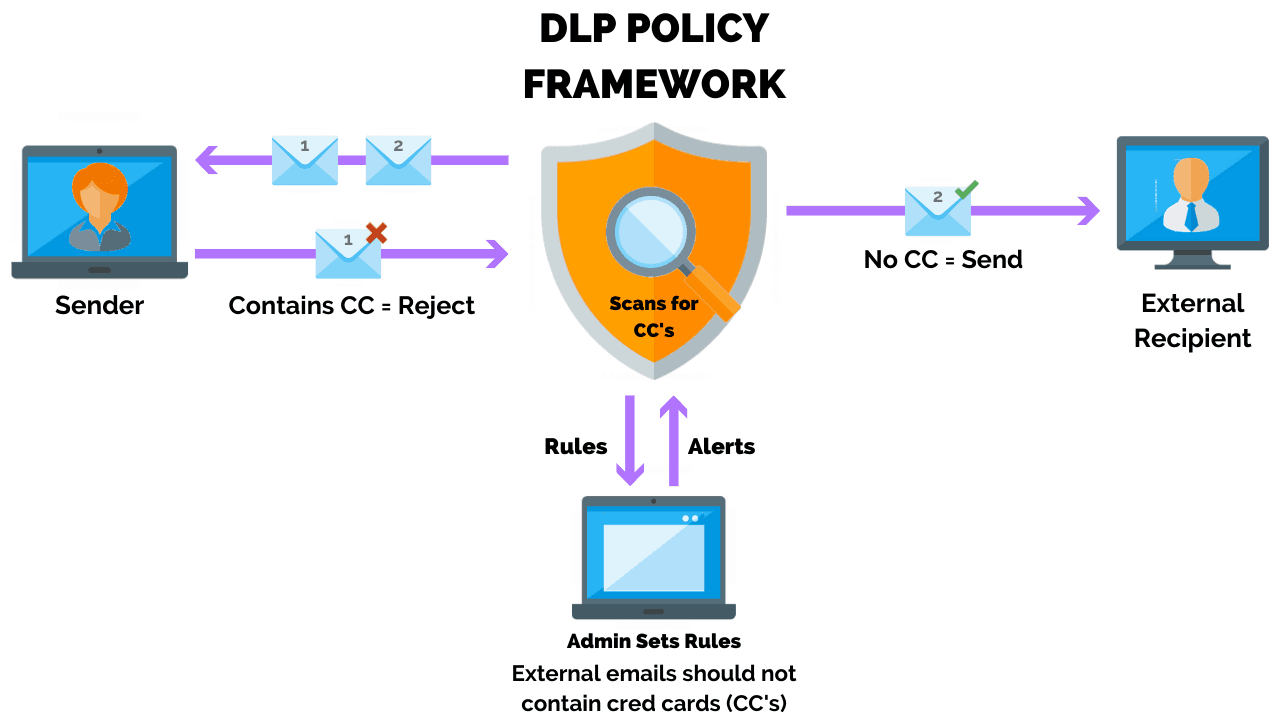
The DLP strategy will provide direction on how to implement the solution, and outlines what, where, and how to protect the data.
I’ll list a few real-world scenarios to bring the strategy process into focus.
Scenario A
A fictional company named MediHealthRecords processes medical insurance claims for a regulated Health Care organization.
They are aware that HIPAA and Medical claim data reside on file servers, but they are not sure where the data is located.
Solution: Implement A DLP At Rest Solution
Here the best choice would be to implement a DLP at Rest solution. The strategy would include a discovery scan of unstructured data, which will crawl the selected storage and locate data matching the pattern of HIPAA and Medical keywords, as set forth in the scan policy.
When a pattern match occurs, a notification alert will be recorded in the DLP database and viewable on the management console by the DLP Analyst.
Scenario B
The Human Resources manager has learned that a few members of the HR department have been emailing sensitive files to their personal Gmail accounts to work on backlogged HR requests over the weekend.
Solution: Implement DLP For Network And Endpoints
A couple of options can be employed. A network security policy can be created to prevent file uploads to Gmail.
The component utilized to enforce this would be data in motion, or DLP for Network.
DLP for Endpoint can also detect http/https, which can be done with advanced application configuration. File upload data can detect the content as it leaves the endpoint to the Internet.
Scenario C
The Sales team is complaining that they cannot store their PowerPoint presentations on USB thumb drives. There isn’t any sensitive data saved, only presentation.
Solution: Implement DLP For Endpoints
The best strategy that fits this scenario is to provide an exception for the Sales team members.
DLP for the Endpoint in most cases allows the ability to whitelist users via a policy based on Active Directory membership.
Scenario D
The CEO would like to know when the secret formula document has moved from its original location or emailed within network.
Solution: Create A DLP Policy
When researching a DLP vendor, ensure that they can demonstrate any scenario involving the protection of your Intellectual Property.
Create a policy that detects the exact match of the document or monitor for specific keywords as it resides in storage or email.
Summarizing Your DLP Strategy
As stated, the examples listed above are real world scenarios that organization’s face every day in the corporate world.
By developing a strategy, an organization can assess which DLP component is applicable to their environment.
It would not be a wise investment to purchase an expensive Enterprise DLP solution that offers an entire suite of DLP features if your organization doesn’t manage unstructured data on-premise or in the cloud.
The cost of implementing a DLP platform can be expensive. Be sure the capital investment is based on a sound cost-benefit analysis, risk assessment, and vendor analysis. This leads to the next topic, who does DLP the best?
Conclusion
The success of a DLP program depends on a well-planned DLP strategy and deployment. We have learned in this article that executive leadership should provide guidance and set the expectations for the overall DLP program.
It is also important to know and understand the organization’s business model. Knowledge of where the most critical data is stored and how it is accessed is key to the success of the DLP strategy.
By understanding the basic principles and components of DLP, your DLP strategy will lead to the establishment of a successful program that will provide governance around data protection for your organization now and for years to come.

