Users Online
· Members Online: 0
· Total Members: 204
· Newest Member: meenachowdary055
Forum Threads
Latest Articles
Articles Hierarchy
What is a Man in the Middle Attack?
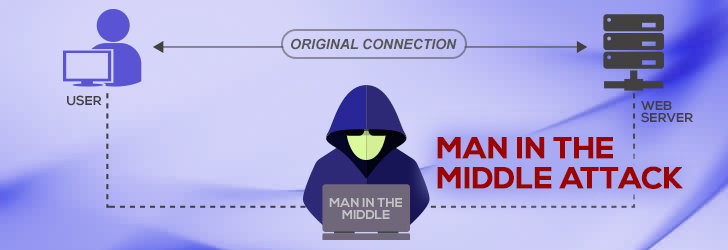
A man-in-the-middle (MITM) attack is a special type of attack in which an attacker covertly relays and potentially alters data between two parties on a network. These parties are usually oblivious to this attack and believe their connection and communication between each other is secured and their messages have integrity; however, that is not the case. The basis of the attack is to circumvent mutual authentication between the two parties and it can only be considered successful if the attacker can successfully impersonate the involved parties to each other. That is to say, the attacker must appear like Person A to Person B and like Person B to Person A. While it is a very common form of attack, most protocols do provide some kind of endpoint verification process to prevent MITM attacks; such as Transport Layer Security (TLS) which can authenticate both parties via a mutually trusted certificate authority.
While the type of attack can indeed be very harmful, it should be noted that there isn’t simply one type of attack which falls under this definition. As a matter of fact, there are quite a few malicious techniques which fall under this description (Cache Poisoning, ARP Spoofing, SSL vulnerabilities, etc). As such, it is highly advised to network administrators to be well-versed in the various types of attacks that exist and what vulnerabilities they exploit to ensure the security of their network.
Defense and Detection
The countermeasures in place against these attacks are broken down into two areas of focus: authentication and tamper detection. Authentication will provide some degree of proof that a message received over a network is from a legitimate source while tamper detection will identify if a message received has been altered.
Authentication is popular with cryptographic systems to protect themselves against MITM attacks and they accomplish this through the exchange of some information (usually public keys) and communicating over a secure link. These systems utilize key-agreement protocols to allow the two communicating parties to define the public key to be shared between them for authentication of messages. For example, TLS has made the Transmission Control Protocol (TCP) a lot more secure against MITM attacks by providing these protocols in the form of client and server certificates which must be issued and verified via a certificate authority (CA). Hypertext Transfer Protocol (HTTP) Public Key Pinning (also called certificate pinning) builds upon this further by protecting against MITM attacks which would target the CA and compromises the certificate. This is accomplished by having the server supply a list of “pinned” public key hashes during the first transaction and having all following transactions require one or more of the keys by the server for authentication.
On the other hand, tamper detection is accomplished through latency examinations but its chances to spot altercations within a message is dependent on certain circumstances. For instance, in cases of long calculations that cause latency of tens of seconds (such as hash functions), this method would be applicable. The two parties would check for discrepancies in their response times when communicating and would identify potential attacks in comparison to any abnormally long response times versus the norm. One could also use forensic analysis by capturing network traffic and analyzing it to determine any nefarious attacks having taken place. This analysis can reveal the source of the attack, if one is found, and should focus on the server’s IP address, the server’s DNS name, and the server’s X.509 certificate; specifically, if the server is self-signed, issued by a trusted CA, revoked, recently changed, or duplicated to other clients on the internet.

