Command-line tools are used each day by security professionals, therefore, for the Security + exam, you must be familiar with these, and so I have provided a screenshot for many of these. We are going to see when we would use each of these in turn:
Internet Control Message Protocol (ICMP): ICMP brings back the replies when you use command-line tools, therefore, if you block incoming ICMP on the network firewall, none of the tools will work externally.
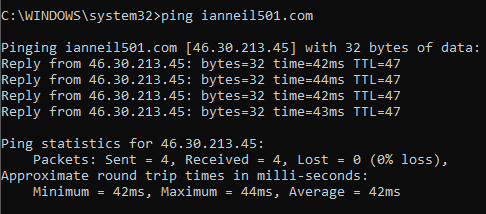
Ping: Ping is used to test connectivity to another host. In the following diagram, you can see that we have pinged the hostname, ianneil501.com, and we have received four replies. The Total Time to Live (TTL) is a maximum of 128 seconds; in this case, it is 47 seconds—see the following screenshot:

Figure 5: Ping
Continuous ping: Continuous ping uses the command ping -t and it is used for diagnostic testing. Normally, we run ping -t when we cannot connect and then once we can connect, we will get replies—see the following screenshot:
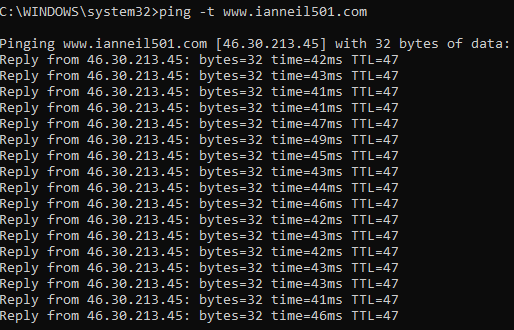
Figure 6: Continuous ping
Netstat: Netstat is used to see the established connections and the listening ports. If you reboot the computer, all of the established ports will disappear—see the following screenshot:
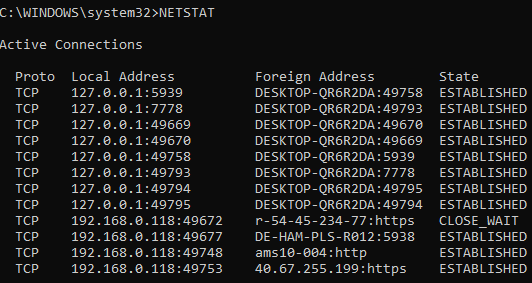
Figure 7: Netstat
Tracert: Tracert is used to trace the route between your computer and a target. This is a maximum of 30 hops and if you have a reading of less than 2 ms, it is a great connection, but less than 25 ms is a good connection. If you get a reading of over 800 ms, it means that you have poor connectivity, for example, a router that is starting to fail—see the following screenshot:
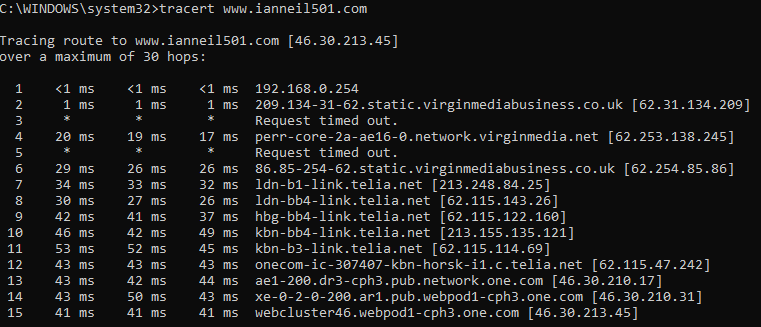
Figure 8: Tracert
Exam tip:Netstat shows the established and listening port, but if you reboot the computer, the established connections disappear.
Nslookup: Nslookup is a diagnostic tool to verify the IP address of a hostname in the DNS server database. We can also use the command set type=MX, for example, which brings back the DNS details on all mail servers in the domain—see the following screenshot:
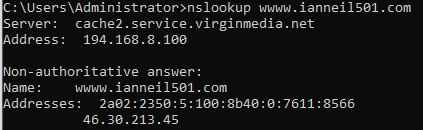
Figure 9: Nslookup
Dig: Dig is the equivalent of nslookup in a Linux/Unix environment. As we can see in the following screenshot, the IP address of Google is 216.58.220.100:
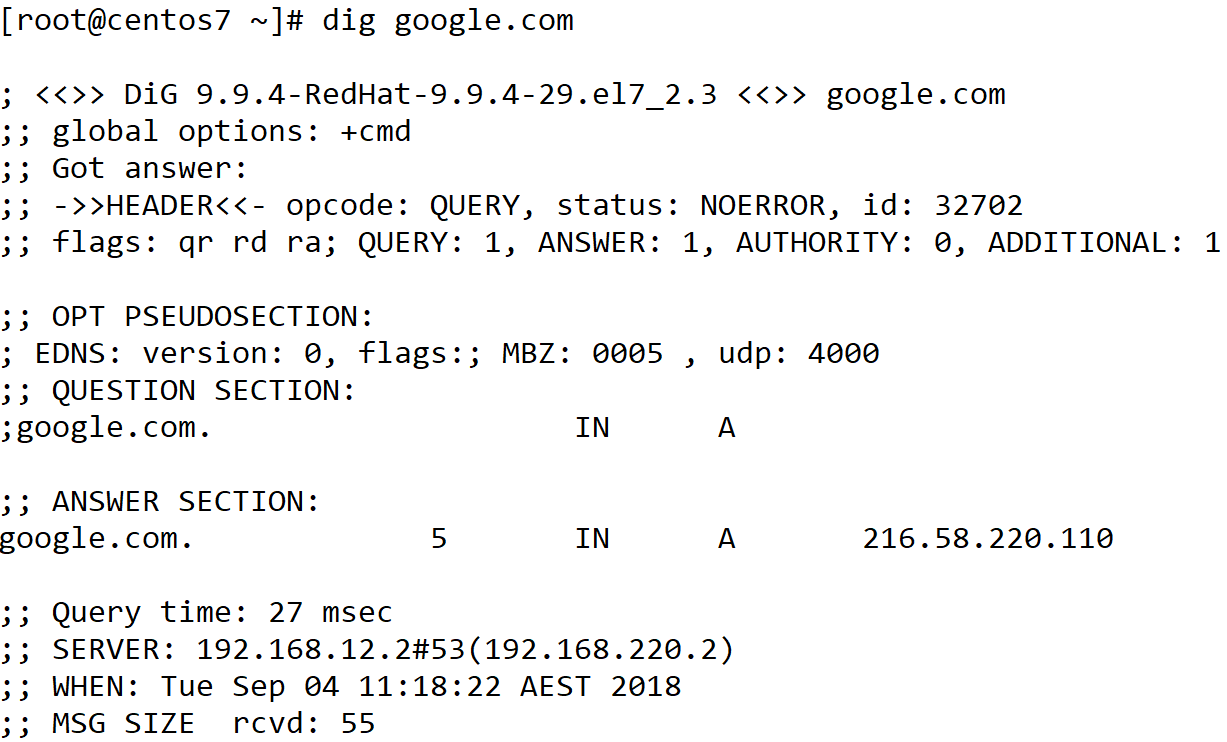
Figure 10: Dig
Address Resolution Protocol (ARP): ARP is used to translate the IP address to a MAC address; the command arp -a shows the ARP cache. You can also use arp -s to add a static entry into the ARP cache—see the following screenshot. You could prevent ARP poisoning by using IPSec:
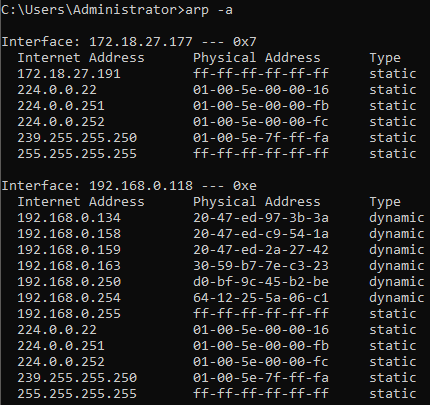
Figure 11: ARP
ipconfig/ip/ifconfig: These commands show the IP configuration. The Windows version is ipconfig, but Unix/Linux can use ip or ifconfig.
The ipconfig /displaydns command is run in the following screenshot, and it shows the DNS cache on a computer:
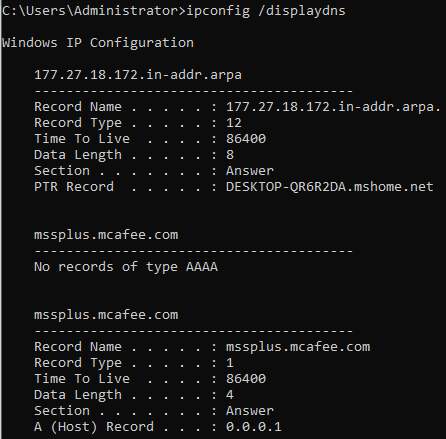
Figure 12: DNS cache
Ipconfig /flushdns is used to clear out all entries in the DNS cache—see the following screenshot:
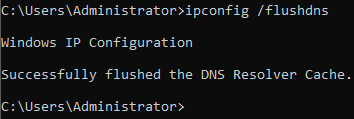
Figure 13: Clear DNS cache
tcpdump: tcpdump is used by Linux/Unix as a packet sniffer command.
tcpdump -i eth0 shows information on the first ethernet adapter, as shown in the following screenshot:
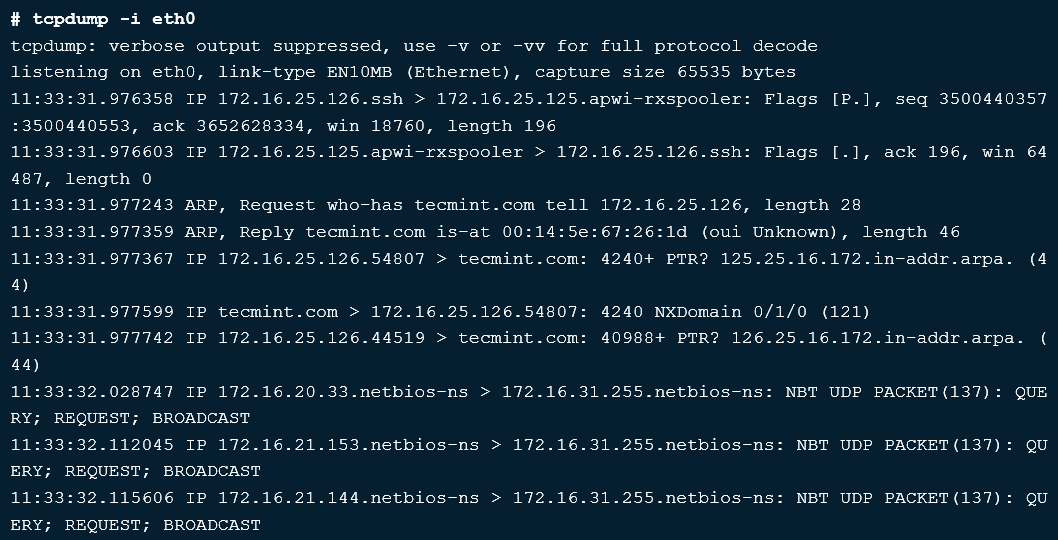
Figure 14: tcpdump
Nmap: Nmap is a free and open source network mapper that can be used for network discovery and security auditing. Many systems and network administrators also find it useful for tasks, such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
Netcat: Netcat, or nc, is a utility for showing network connections in a Linux/Unix environment. The command netcat -z is being used to scan ports 78-80, and from this you can see that ports 78 and 79 are closed, but port 80 being used by HTTP is open. The -v switch means verbose and shows all information—see the following screenshot:
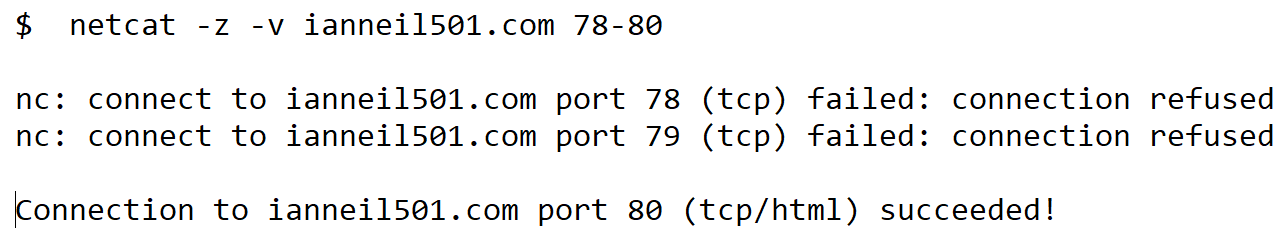
Figure 15: Netcat
There are various applications that security administrators can use to analyze and stop various attacks. Let's look at these here:
HIDS/HIPS: HIDS/HIPS are both used inside host computers; the HIDS to detect attacks and the HIPS is used to protect the computer against attacks. Both have filters set up to choose an alert type to filter. Look at the following diagram, where we are setting a filter for insecure SSH connection attempts:
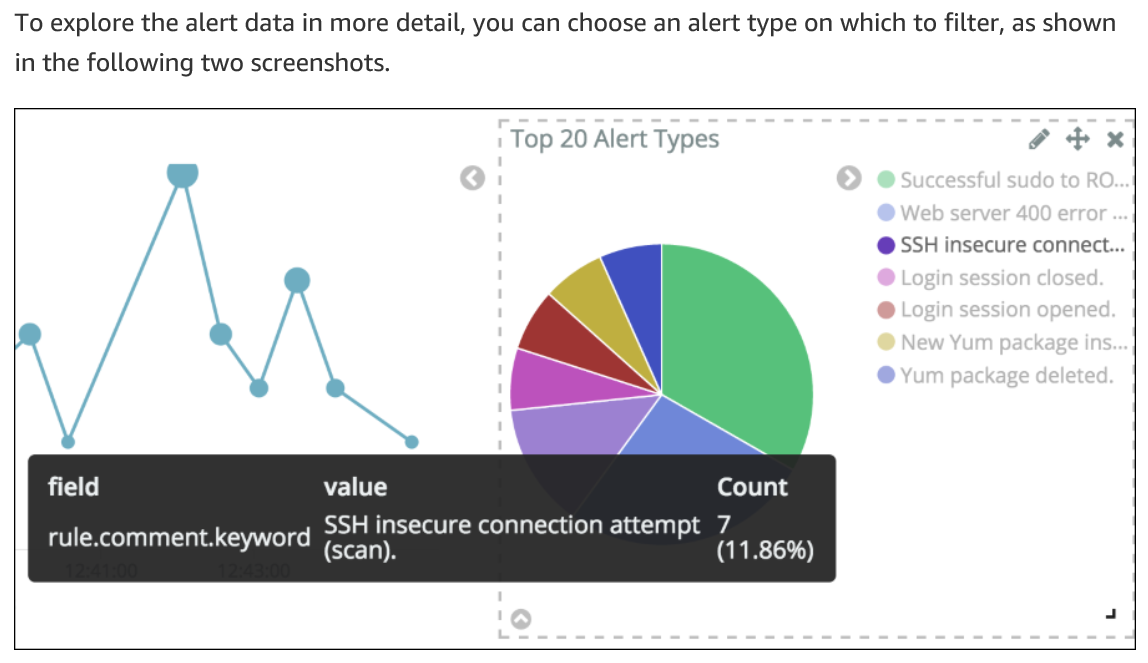
Figure 16: HIDS output
Antivirus/advanced malware tools: There are quite a few antivirus/anti-malware tools that will scan the computer on a regular basis, and they then produce reports. The following is a list of viruses that have been quarantined, followed by a scan of sensitive documents held on a desktop. The AVG Antivirus free software in the following screenshot shows four viruses that have been quarantined so that they cannot cause any damage:
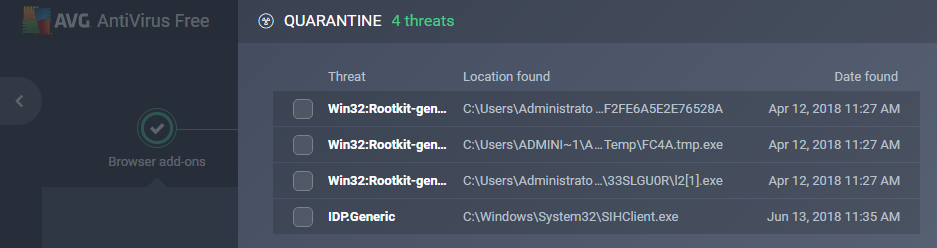
Figure 17: Quarantined viruses
The following screenshot shows a scan for sensitive documents held on a desktop, and you can see that 135 documents have been found. We may need to install Data Loss Prevention (DLP) to protect these:
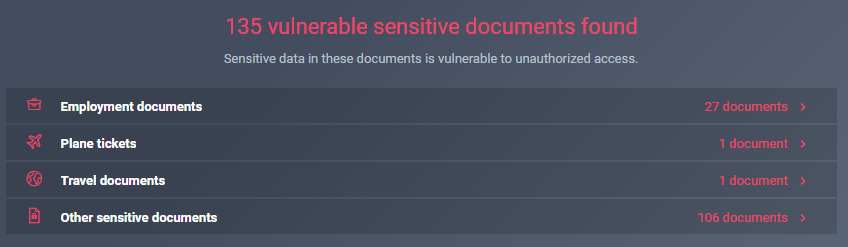
Figure 18: Sensitive documents scan
File integrity checker: Microsoft has a System File Checker (SFC) that can replace corrupted files by replacing them with a copy held in a compressed folder with system32. You run it with the command sfc /scannow, as shown in the screenshot:
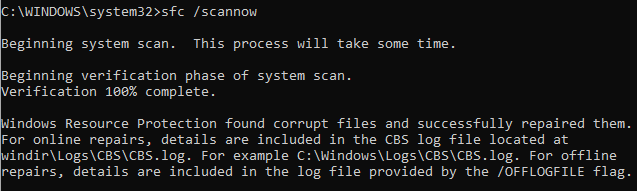
Figure 19: System file checker
File Checksum Integrity Verifier (FCIV): This is also a Microsoft utility that can generate MD5 or SHA-1 hash values for files to compare the values against a known good value. FCIV can compare hash values to make sure that the files have not been changed. This can help you identify changes that have been made to your computer system.
Host-based firewall: A host-based firewall can be used to prevent unauthorized access to the desktop, and we can set up allowed rules for those applications that we wish to use. The firewall in the following screenshot allows antivirus updates, checkpoints, VPN DNS name resolution, Firefox, and Java:
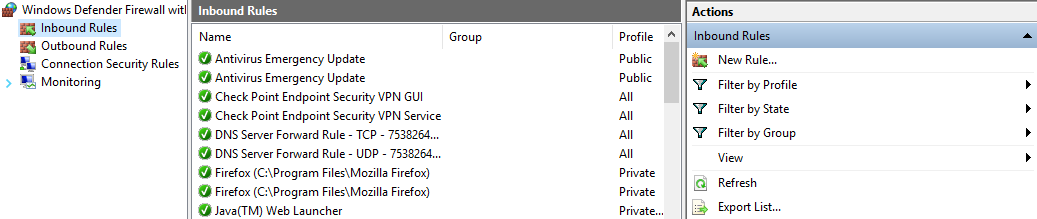
Figure 20: Host-based firewall
Application whitelisting: Application whitelisting determines the rules on what applications are allowed to be run on a computer. The following is an example of application whitelisting using the Microsoft Application Control Policy tool called Applocker. This would then mean that the end user could only install and use these approved applications; if the application is not on the list, it is not allowed to be installed:
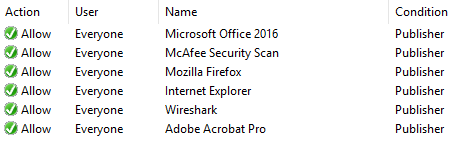
Figure 21: Application whitelisting
Removable media control: Removable media are at a very high security risk as it is easy to steal data using them. However, we can prevent this by using a group policy; you can see one of the following options in the screenshot is Prevent installation of removable devices. This would prevent someone inserting a USB drive or another form of removable media to steal data:
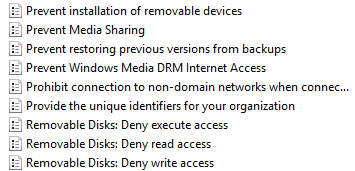
Figure 22: Removable media policies
Patch management tools: Microsoft has got a patch management tool called Windows Server Update Services (WSUS) that allows you to pull down the latest updates from the Microsoft website for different products.
Exam tip:Applications must be added to the whitelist so that they can be approved to be used.
Unified Threat Management (UTM): The UTM is a firewall that can also prevent URL filtering, content filtering, and malware inspection. The following screenshot shows the setting of the Sophos UTM firewall version 9 where you can see the various information that it provides:
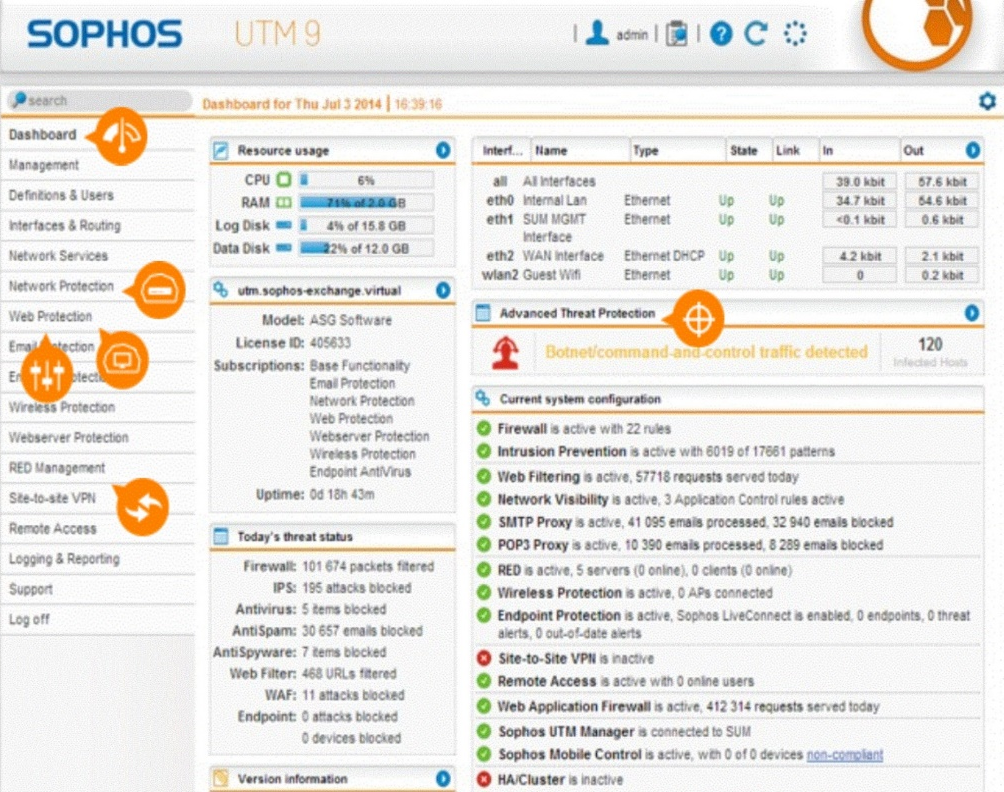
Figure 23: Sophos UTM 9
Data Loss Prevention (DLP): DLP templates can be set up to prevent emails with sensitive and PII data from being emailed out of the company. DLP can prevent the removal of documents on a file server.
Example: We wish to set up a template to prevent Visa, Mastercard, Diners Club, JCB, Discover, and American Express details from being emailed out. This is done by creating a template that consists of a regular expression. Should the pattern be matched, the email will be blocked and an administrator will be notified. The regular expression is shown here:
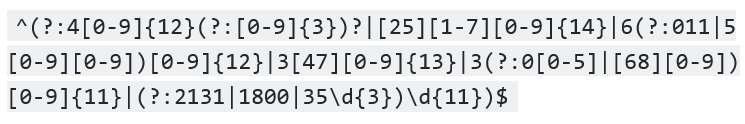
Figure 24: Regular expression for credit cards
Data Execution Prevention (DEP): When DEP is enabled, it prevents harmful programs such as viruses and other threats from trying to execute in restricted areas of the operating system. From the command prompt, you can run the command wmic OS GetDataExecutionPrevention_SupportPolicy . The values will either be 0.1.2 and 3. The following screenshot shows that it has a value of 2, which means it is enabled:

Figure 25: Data execution prevention
Web Application Firewall (WAF): A WAF is used to prevent attacks on web servers and the applications that they host. The following screenshot is an example of the log file from a Sonic Wall web application firewall log:
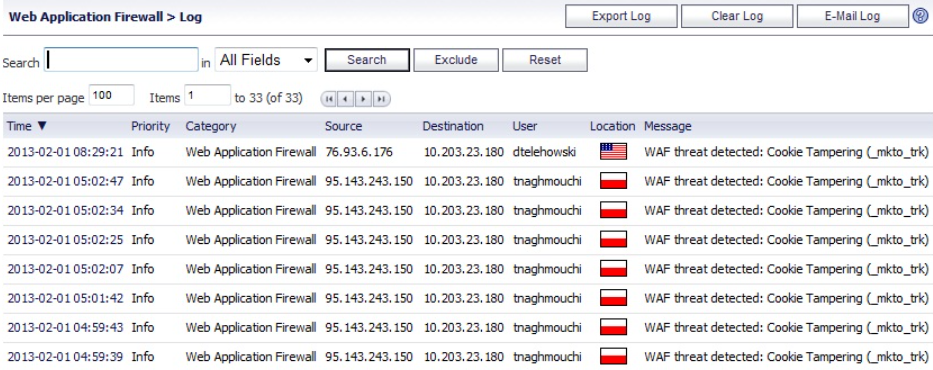
Figure 26: WAF log file
What is the purpose of an incident response plan?
Name three different categories of incidents.
Name three different types of roles required to deal with an incident.
What should the Help Desk do when an incident has just been reported?
What is the purpose of an incident response exercise?
What is the first phase of the incident response process and what happens there?
What is the last phase of the incident response process?
What would happen if the last process of the incident response process is not carried out?
What is order of volatility?
What is the first action I should take if your company has a web-based or remote attack?
What should I do if I find a USB flash drive in one of the servers?
What is the process of chain of custody and why would you investigate it?
What is the purpose of legal hold?
What is the purpose of record time offset and what purpose does it provide?
What is the first stage a forensics officer should carry out when he has just taken possession of a laptop computer?
What is the first stage a forensics officer should carry out when he has just taken possession of a hard drive or removable drive?
Why would a forensics officer take hashes of data before he starts his investigation?
What are the benefits of a security administrator using a SIEM system?
Can I delete data that I have copies of on a WORM drive?
Why would we carry out active monitoring?
What tools can I use to find the operating system running on a computer?
If I am using an unencrypted media package that runs across my network, how can I capture the passwords?
If I want to find information about the operating system of a remote web server, what is the best tool to use?
What is the purpose of a network mapper?
If I have disabled the SSID on my wireless access point, can someone still find the SSID?
What type of vulnerability scanner can audit files and find out account vulnerabilities?
What is the most basic vulnerability scanner that can only find missing patches?
What tools can I use to ensure that the settings on my server are correct?
What is the purpose of using the technique of steganography?
How can I find the attack method a hacker would use to exploit my website?
What is the quickest form of backup?
What is the quickest form of tape backup?
What are the most common types of backup? Name two.
How many tapes would I need to recover my data if I use a differential backup?
What would happen to command line troubleshooting tools if I block incoming ICMP on the network firewall?
What tool is used to test connectivity and what command would you use to make it continuous?
What is normally the maximum value of a packets TTL?
What does the command-line tool netstat -an provide and what would happen if I rebooted the computer?
What tool can I use in a Windows environment to verify the hostname entry in the DNS server?
What are the commands to display the DNS cache and then clear all entries from it?
What command-line tool displays the route to a remote web server?
What is a packet tracing tool used in a Linux/Unix environment?
What is the command-line tool to show the session between two hosts in a Linux/Unix environment?
What is the purpose of a file integrity checker?
If an application is neither on the blacklist or the whitelist, how can I ensure that I can install it on my computer?
How could I prevent 4,000 people from installing USB flash drives on their computers?
What tool is a firewall that can URL filter, content filter, and provide malware inspection?
What tool can prevent PII and sensitive data from leaving your network via email or from being copied onto a USB flash drive.
What is the tool that can prevent malicious programs from accessing the registry?
What tool would you use to prevent an attack on a web-based application?
An incident response plan is written for a particular incident and lays out how it should be tackled and the key personnel required.
The different categories of incidents are as follows:
Unauthorized access
Loss of computers or data
Loss of availability
Malware attack
DDoS attack
Power failure
Natural disasters such as floods, tornados, hurricanes, and fires
Cyber security incidents
The different roles required to deal with an incident are as follows:
Incident response manager—a top level manager takes charge
Security analyst—technical support to the incident
IT auditor—check that the company is compliant
Risk analyst—evaluates all aspects of risk
HR—sometime employees are involved in the incident
Legal— gives advice and makes decisions on legal issues
Public relations—deals with the press to reduce the impact
The help desk identifies the incident response plan required and the key personnel that need to be notified.
An incident response exercise is to carry out the incident response plan and any shortfalls.
The first phase of the incident response process is the preparation phase where the plan is already written in advance of any attack.
The last phase of the incident response process is lessons learned where we review why the incident was successful.
If we do not carry out lessons learned, the incident may re-occur. Lessons learned is a detective control where we try to identify and repair any weaknesses.
Collecting the most volatile evidence first.
The first action would be to capture the network traffic so that we can identify the source of the attack.
You should collect the data in the volatile memory first.
Chain of custody lists who has handled the evidence before it goes to court. Any break in the chain or the evidence leaving your site is a breach of the chain of custody and the judge would ask for it to be investigated.
Legal Hold is a process to ensure the securing data so it cannot be deleted, for example putting someone's mailbox on hold. This is sometimes called litigation hold.
Record time offset is used for time normalization across multiple time zones.
He should take a system image so that it can be used for investigation.
He should take a forensic copy so that it can be used for investigation.
To ensure that when he is finished that he can prove integrity of the data.
A SIEM system can be used to correlate logs from multiple places and give real time reporting of incidents.
Data cannot be deleted from a WORM drive, as it is write-once, read many.
Active monitoring is used to identify an incident in real time.
You can use a protocol analyzer to find the operating system running on a computer.
You can use a protocol analyzer to capture the data and command going to a network-based application.
Banner grabbing is the best tool to use if you want to find information about the operating system of a remote web server.
A network mapper can identify all hosts on your network, their patch level, and any services running on them.
You can use a wireless packet sniffer or a SSID de-cloak device to find the SSID of your WAP, as it is embedded in the network traffic going to the WPA.
A credentialed vulnerability scanner can audit files and find out account vulnerabilities.
A non-credentialed vulnerability scanner that can only find missing patches.
A compliance scanner ensures that the settings on your server are correct.
Steganography allows you to hide a file, an audio, video, or image inside another a file, audio, video, or image. You may notice a larger file or faded image.
You would set up a honeypot to find the attack method a hacker would use to exploit your website.
The quickest form of backup is a snapshot of a virtual machine.
The quickest form of tape backup is a full backup, as all backups need a full backup to start with.
The two most common tape backups are full and incremental.
You will need two tapes to perform a differential backup.
If incoming ICMP was blocked on the network firewall, none of your command-line tools would work as ICMP bring back the replies.
Ping is the tool that is used to test connectivity and the command ping -t is used for continuous ping.
The normal maximum value of a packets TTL is 128 seconds or less.
Netstat -an shows listening and established ports. If you reboot your computer, the established sessions will disappear.
DNS lookup is used in a Windows environment to verify the hostname entry in the DNS server. Dig is the Unix/Linux equivalent.
Ipconfig /displaydns displays the DNS cache and Ipconfig /flush clears all entries.
Tracert is used to display the route to a remote web server over a maximum of 30 hops.
tcpdump is a packet tracer used in a Linux/Unix environment.
Netcat or nc shows the session between two hosts in a Linux/Unix environment.
A file integrity checker can determine whether a file has been altered by an application or is corrupt.
If an application is neither on the blacklist or the whitelist, you need to add it to the whitelist so that you can install it on your computer.
You can use group policy to prevent 4,000 people from installing USB flash drives on their computers.
A UTM is a firewall that can URL filter, content filter, and provide malware inspection.
DLP can prevent PII and sensitive data from leaving your network via email or from being copied onto a USB flash drive.
DEP can prevent malicious programs from accessing the registry by restricting the area that programs can access.
A web application firewall can prevent an attack on a web-based application.