Certificates are used for both encryption and authentication, and in this chapter, we are going to look at different encryption types and how certificates are issued and used. This is the most difficult module for students to understand, so we have focused on making the most difficult aspects seem easy. If you are going to be successful in the Security+ exam, you must know this module thoroughly. We will start with the Public Key Infrastructure (PKI), both the public and private keys. It is an asymmetric form of encryption.
We will cover the following exam objectives in this chapter:
Comparing and contrasting basic concepts of cryptography: Symmetric algorithms—modes of operation—asymmetric algorithms—hashing—salt, IV, nonce—elliptic curve—weak/deprecated algorithms—key exchange—digital signatures—diffusion—confusion—collision—steganography—obfuscation—stream vs. block—key strength—session keys—ephemeral key—secret algorithm—data-in-transit—data-at-rest—data-in-use. Random/pseudo-random number generation—key stretching. Implementation vs. algorithm selection. Crypto service provider—Crypto modules. Perfect forward secrecy—security through obscurity. Common use cases—low power devices—low latency—high resiliency—supporting confidentiality—supporting integrity—supporting obfuscation—supporting authentication—supporting non-repudiation. Resource versus security constraint
Explaining cryptography algorithms and their basic characteristics: Symmetric algorithms—AES—DES—3DES—RC4—Blowfish/Twofish. Cipher modes—CBC—GCM—ECB—CTR—stream versus block. Asymmetric algorithms—RSA—DSA—Diffie-Hellman—groups—DHE—ECDHE—elliptic curve—PGP/GPG—hashing algorithms—MD5—SHA1-HMAC – RIPEMD. Key stretching algorithms—BCRYPT—PBKDF2—obfuscation—XOR—ROT13—substitution ciphers
Given a scenario, implement a public key infrastructure: Components—CA—intermediate CA—CRL—OCSP—CSR—certificate—public key—private key—Object Identifiers (OID). Concepts—online versus offline CA—stapling—pinning—trust model—key escrow—certificate chaining. Types of certificates—wildcard—SAN—code signing—self-signed—machine/computer—e-mail—user—root—domain validation—extended validation. Certificate formats—DER—PEM—PFX—CER—P12—P7B
The public key infrastructure provides asymmetric techniques using two keys: a public key and a private key. There is a certificate hierarchy, which is called the certificate authority, that manages, signs, issues, validates, and revokes certificates. Let's first look at the components of the certificate hierarchy. A certificate is known as an X509 certificate.
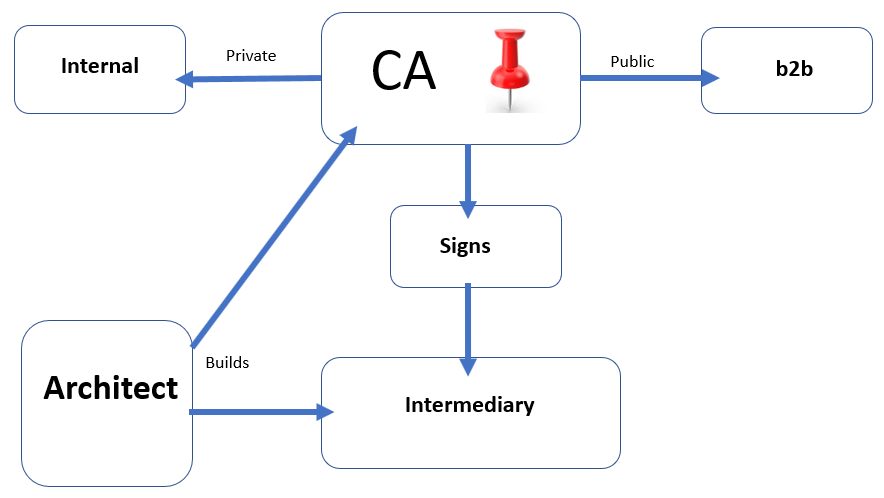
The Certificate Authority (CA) is the ultimate authority as it holds the master key, also known as the root key, to sign all of the certificates that it gives the Intermediary, which then in turn issues to the requester:

Figure 1: Certificate hierarchy
Online CA: An internal online CA is always up and running so that people in the company can request a certificate at any time of the day or night. The environment would not be a government or a top security environment.
Offline CA: An offline CA is for a military or secure environment where clearance and vetting must be completed before someone can be issued a certificate. The CA is kept offline and locked up when it is not being used, but is taken out and switched to issue new certificates. After the issue is it back to offline and stored in the secure area.
Exam tip:
For Business-to-Business (B2B) transactions and working with other commercial companies, your X509 certificates need to come from a public CA.
There are different types of CA:
Public CA: A public CA is also known as a third-party CA and is commercially accepted as an authority for issuing public certificates; examples are Comodo, Symantec, and Go Daddy. There are many more. The benefits of using a third-party CA is that all of the management is carried out by them; once you purchase the certificate, all you have to do is install it. They keep an up-to-date Certificate Revocation List (CRL) where you can check if your certificate is valid. A certificate that is not valid will not work if I am going to sell goods and services to other companies. This is known as B2B and I must use a public CA. For example, I put petrol in my car and go to pay for the petrol. I give the attendant some monopoly money but he refuses to take it; this would be the equivalent of a private CA. Businesses will not accept it as payment. I then go to the ATM cash machine outside and withdraw $100 and I give this to the attendant; he smiles and accepts it and gives me some change. This is the equivalent of a public CA.
If you wish to trade and exchange certificates with other businesses, you need to get your certificate from a public CA. The certificate that follows has been issued to the Bank of Scotland from a public CA called DigiCert Global CA; you can see on the front of the certificate the purpose for use and also the dates that it is valid for. The X509 has an Object Identified (OID) that is basically the certificate's serial number—the same way that paper money has serial numbers:
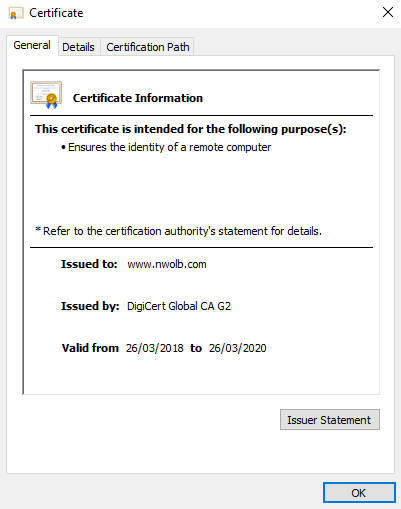
Figure 2: Public CA issued certificate
Private CA: A private CA can only be used internally; however, although it is free, you must maintain the CA. Hopefully, your company has the skill set to do so.
Certificate pinning: Certificate pinning prevents the compromise of the CA and the issuing of fraudulent X509 certificates.
Intermediary authority: The intermediary authority accepts the incoming requests for certificates and issues them once the CA has signed them. The certificates that are issued are known as X509 certificates.
Exam tip:
Certificate pinning prevents CA compromise and the issuing of fraudulent certificates.
Certificate architect: The certificate architect builds both the CA, and if it is already present, he will build the intermediary authority.
Certificate chaining: Certificates in computer security are digital certificates that are verified using a chain of trust where the trust anchor for the digital certificate is the root CA. This chain of trust is used to verify the validity of a certificate as it includes details of the CRL.
Certificates have some form of trust where the certificate can check whether or not it is valid. We are going to look at different trust models; you need to ensure that you know when each is used:
Trust anchor: A trust anchor in a PKI environment is the root certificate from which the whole chain of trust is derived; this is the root CA.
Trust model: A trust model proves the authenticity of a certificate; there are two trust models:
Hierarchical trust model: This uses a hierarchy from the root CA down to the intermediary (also known as a subordinate); this is the normal PKI model. An example can be seen in the certificate hierarchy diagram.
Bridge trust model: The bridge trust model is peer to peer, where two separate PKI environments trust each other. The certificate authorities communicate with each other, allowing for cross certification; sometimes, it is referred to as the trust model.
Certificate chaining: Certificates in computer security are digital certificates that are verified using a chain of trust where the trust anchor for the digital certificate is the root CA. This chain of trust is used to verify the validity of a certificate as it includes details of the CRL.
Exam tip:
When two separate CAs trust each other, they will use a trust model called the bridge of trust.
Web of trust: A web of trust is a concept used in PGP or various versions of PGP to establish the authenticity of the certificate being used. In PGP, two people are going to encrypt data between themselves; the first stage would be to give each other a public key so that they can encrypt the data being sent to the other party. It works with the same concepts as asymmetric encryption although it is on a smaller scale.
Exam tip:
A bridge trust model is used so that two separate CAs can work with each other.
Each time a certificate, is used the first thing that must happen is that it must be checked for validity; there are three separate processes that you must know thoroughly, and these are as follows:
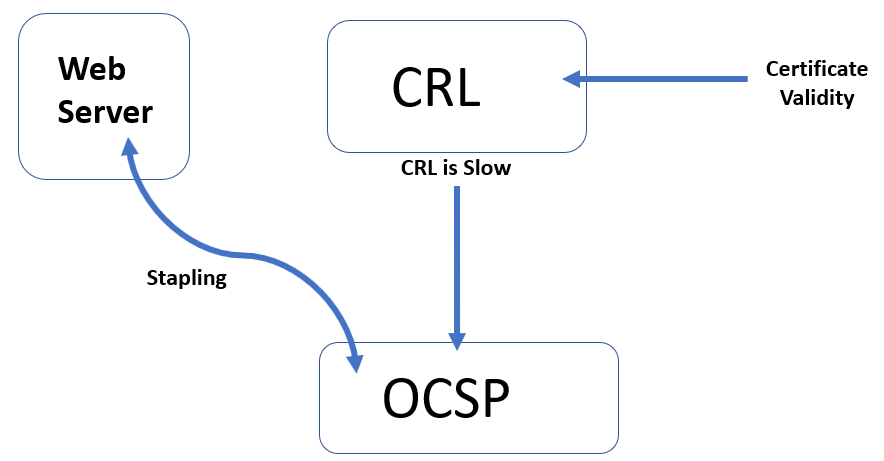
Figure 3: Certificate validity
Certificate Revocation List (CRL): The first stage in checking if a certificate is valid, no matter the scenario, is to check the CRL. If the X509 is in the CRL, it is no longer valid and will not be accepted. No matter how obscure the question posed in the exam, unless it is going slow or it is a web server looking for a faster lookup, it will be the CRL that provides certificate validity.
Online Certificate Status Protocol (OCSP): Only when the CRL is going slow will the OCSP came into play; it is much faster than the CRL and can take a load from the CRL in a very busy environment.
OCSP stapling/certificate stapling: Certificate stapling, also known as OCSP stapling, is used when a web server bypasses the CRL to use the OCSP for a faster confirmation when its certificate is valid.
The validation of a certificate is done by the CRL unless it is going slow—then it will be the OCSP doing this.
We are now going to look at the different ways certificates are managed in a PKI environment, starting with the request for a new certificate and ending with different certificate formats. You must learn all of this information thoroughly as these aspects are heavily tested:
Certificate Signing Request (CSR): It is the process of requesting a new certificate; the process for the exam is that two keys are generated and the public is sent to the CA, which then returns a file that is the X509:
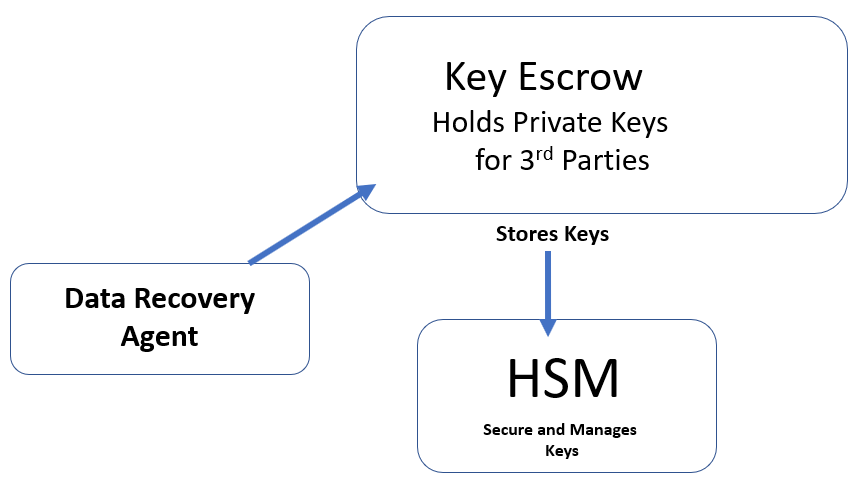
Figure 4: Key escrow
Key escrow: The key escrow holds the private keys for third-parties and stores them in a Hardware Security Module (HSM).
Hardware Security Module (HSM): The HSM can be a piece of hardware attached to the server or a portable device that is attached to store the keys. See the preceding diagram for more on this.
Data Recovery Agent (DRA): If a user cannot access his data because his private key is corrupted, the DRA will recover the data. The DRA needs to get the private key from the key escrow.
The key escrow stores private keys for third parties.
Certificates: There are two main certificate types, the public key and the private key. The Public Key is sent to third parties to encrypt the data, and the private key decrypts the data. If you think of the private key as your bank card, you would never give that to anyone else, especially your wife! The public key is the deposit slip that is tied to your account—if you were in a room with twenty people who wanted to pay $20 into your account, you would definitely give them your deposit slip. You will always give your public key away because when you are encrypting data you will always use someone else's Public Key.
A web server will use certificate stapling to bypass the CRL and use the OCSP for faster certificate validity. This is also known as OCSP stapling.
Object Identifiers (OID): The OID on a certificate is similar to a serial number on a bank note. Bank notes are identified by their serial number. The certificate is identified by its OID.
Certificate formats: There are different certificate formats, and these are as follows:
|
Certificate type |
Format |
File extension |
|
Private |
P12 |
.pfx |
|
Public |
P7B |
.cer |
|
PEM |
Base 64 format |
.pem |
|
DER |
Extension for PEM |
.der |
The certificate equivalent of a serial number is the OID that is located on the X509 itself.
As a security professional, you will be responsible for purchasing new certificates, and therefore you must learn the certificates types thoroughly to ensure that you make the correct purchase. We will start with the self-signed certificate that can roll out with applications like Exchange Server or the Skype server and finish with extended validation where the certificate has a higher level of trust:
Self-signed: A self-signed certificate is issued by the same entity that is using it and normally rolls out with an application such as exchange server or Skype. However, it does not have a CRL there it cannot be validated or trusted.
Wildcard: For a wildcard card certificate for a domain called ianneil501.com, the wildcard certification would be ianneil501.com and can be used for the domain and a subdomain. For example, in the domain ianneil501.com there are two servers called web and mail. The wildcard certification is ianneil501.com and when installed it would work for the Fully Qualified Domain Names (FQDN) of both of these—that would be web.ianneil501.com and mail.ianneil501.com. A wildcard can be used for multiple servers in the same domain.
PEM uses a Base64 certificate.
Domain validation: A domain-validated certificate (DV) is an X.509 (https://en.wikipedia.org/wiki/X.509) certificate that's typically used for Transport Layer Security (TLS) (https://en.wikipedia.org/wiki/Transport_Layer_Security) where the domain name (https://en.wikipedia.org/wiki/Domain_name) of the applicant has been validated by proving some control over a DNS domain (https://en.wikipedia.org/wiki/Domain_name).
Subject Alternative Name (SAN): A SAN certificate can be used on multiple domain names, for example, abc.com or xyz.com, where the domain names are completely different, but they can use the same certificate.
Code signing: Code signing certificates are used to digitally sign software so that its authenticity is guaranteed.
Computer/machine: A computer or machine certificate is used to identify a computer within a domain.
User: A user certificate is to provide authenticity to a user with applications that he uses.
A wildcard certificate can be used on several servers in the same domain. A SAN certificate can be used on servers in different domains.
Extended validation: Extended validation certificates provide a higher level of trust in identifying the entity that is using the certificate. It would normally be used in the financial arena; the background of the URL turns green. The companies applying for the certificate would have to provide more detailed information about the company. See the following screenshot:
Figure 5: Extended validation
There are two main types of encryption that use certificates, and these are asymmetric and symmetric; we need to learn about each thoroughly. Let us start by explaining what encryption is; please remember you are taking plain text, and changing it into ciphertext.
Encryption is where we take plaintext that can be easily read and convert it into ciphertext that cannot be read. For example, if we take the word pass in plain text, it may then be converted to UDVV; this way, it is difficult to understand:
Substitution cipher: Julius Caesar, who died in 44 BC, invented the first substitution cipher where he moved each letter three places. This way, he could make his military plans unreadable if they had been intercepted. What he forgot about was most people in those days could not read! This was called ROT 3, meaning rotate it by three letters. This is now known as the caesar cipher. For example, if I take the word echo and move each letter it on three places you will get the word hfkr—that would be difficult for someone to read and understand.
ROT 13: ROT 13 is a variation of the Caesar cipher; as there are 26 letters in the alphabet, we are rotating the letters 13 times. The key to ROT 13 would be as follows:
|
Letter |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
|
ROT 13 |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|
|
|||||||||||||
|
Letter |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|
ROT 13 |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
When receiving the message—GVZR SBE GRN—then we would apply the ROT 13, but instead of going forward 13 places to decipher we would simply go back 13 places and the message would now be TIME FOR TEA.
Exam tip:
Encryption is taking plaintext and changing it into ciphertext so that it cannot be read.
There are two types of encryption that use certificates and these are asymmetric and symmetric; let us look at each of these in turn:
Symmetric encryption: Symmetric encryption only uses one key, which is known as the private or shared key. The same key encrypts and decrypts the data. The danger of symmetric encryption is that if the key is stolen, the attacker gets the keys to the kingdom. The main reason for using symmetric encryption is that it can encrypt large amounts of data very quickly. The Security+ exam does not focus on key exchange because it only uses one key, but looks at which is the fastest or strongest symmetric key, and that it is used for the encryption of large amounts of data.
Diffie Hellman: When symmetric data is in transit, it is protected by Diffie Hellman, whose main purpose is to create a secure tunnel for symmetric data to pass through.
Diffie Hellman groups: Diffie-Hellman (DH) groups specify the strength of the key. For example, group 1: 768-bit, Group 2: 1024-bit, group 5: 1536-bit, group 14: 2048 bit minimum that is acceptable. Diffie Hellman group 19: 256-bit elliptic curve is acceptable and so is group 20 384-bit elliptic curve.
Asymmetric encryption: Asymmetric encryption uses two keys—a private key and a public key—and is also known as a PKI, complete with its CA and intermediary authorities. The Security+ exam tests the use of both the private and public keys very thoroughly. I have created a diagram to help you understand the purpose of each key. We use the mnemonic South-East-Distinguished-Visitor (SEDC).
The first stage in encryption is the key exchange; you will always keep your private key and give away your Public Key. You will always use someone else's public key to encrypt:
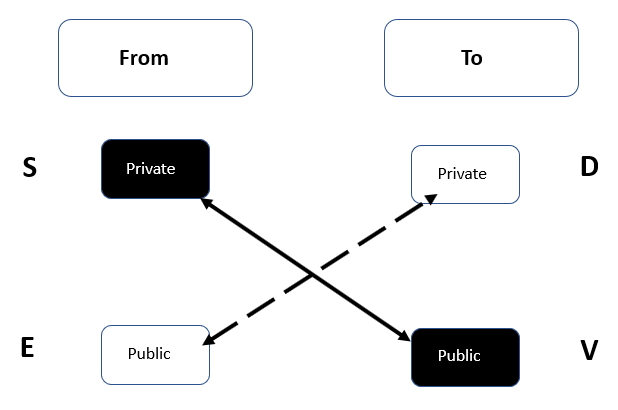
Figure 6: Asymmetric key exchange
In the preceding diagram, there are two different key pairs: the black key pair and the white key pair. These work together. If you think of the private key as being your bank card, you will never give it away, but the Public Key is your deposit slip—you will give it away so that people can pay money into your account.
The person who is sending the data is on the From side and the person receiving the data is on the To side.
The way to remember the labels are on the left-hand side is South-East and on the right-hand side is distinguished-visitor. These labels stand for:
S: Sign (digital signature)
E: Encryption
D: Decryption
V: Validation
For example, Bob wants to encrypt data and send it to Carol; how is this done? Let us look at the following diagram. We can see that Bob owns the black key pair and Carol owns the white key pair. The first thing that needs to happen before encryption can happen is that they give the other person their public key:
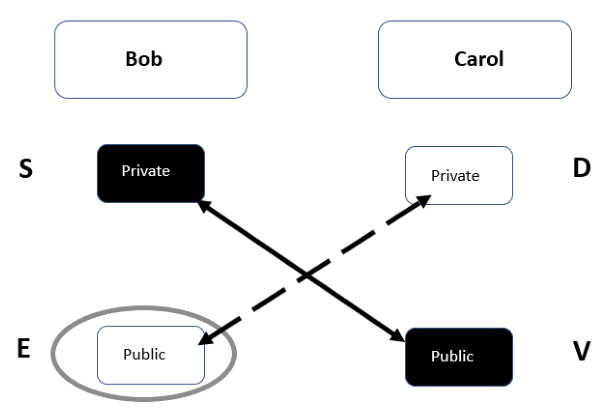
Figure 7: Bob encrypting data
You can see the under the column for Bob that he has his private key, which he will always keep, and the public key that Carol has given him. In the preceding diagram, you can see the label E for encryption, and therefore Bob uses Carol's public key to encrypt the data. Then, under Carol, you can see the letter D for decryption; and therefore, when the encrypted data arrives, Carol uses the other half of the white key pair, the private key, to decrypt the data.
Exam tip:
Encryption stops the data being read by changing plaintext to ciphertext. A digital signature ensures that the data has not been altered as it creates a hash of the message, but the original data can be read.
When we send an email or document to someone, it could be intercepted in transit and altered. Your email address could be spoofed and someone could send an email as if it was from you, but there is no guarantee of integrity. Do you remember in Chapter 1, Understanding Security Fundamentals, that we used hashing to provide the integrity of data, however, in emails we use a Digital Signature? We sign the email or document with our private key and it is validated by our public key.
The first stage in digital signatures is to exchange public keys—the same principle as encryption.
For example, George wants to send Mary an email and he wants to ensure that it has not been altered in transit. See the following diagram:
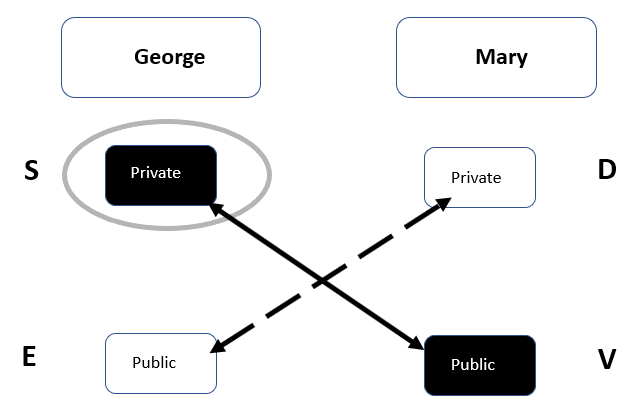
Figure 8: Digital signature
In the preceding diagram, you can see that George is going to sign the email with his private key when he sends it to Mary; she validates it with the Public Key that George has already given to her. When the email has been validated, she knows that the email has not been tampered with.
When people are asked to sign contracts, they sometimes use a third-party provider that asks them to digitally sign the contract; this then makes the contract valid as the digital signature proves the identity of the signatory.
Non-repudiation: When I complete a digital signature, I am using my private key that I should never give away to sign the email or document, proving that it has come has come from me. Non-repudiation means that I cannot deny that it was me who signed the document. I could not say it was done by someone else. In the early sixth century, King Arthur would send messages to his knights on a parchment scroll and then would put his wax seal on the scroll to prove it came from him. The digital signature in modern life is doing the same—it is proving who it came from. The Digital Signature creates a one-way hash of the entire document, so it also provides integrity similar to hashing.
Exam tip:
I will always use someone else's public key to encrypt data. I will never give my private key away. It is like giving away my bank card; it will never happen.
If we look at symmetric and asymmetric keys, they use a cipher that has a number of bits attached to it—the lower the number, the faster and the higher the bits. The slower, however the one with the higher number of bit is stronger.
For example, we have two people who are going to complete a challenge—they are Usain Bolt, who is DES, a 56-bit key, and we have King Arthur wearing armor, who has an RSA of 4,096 bits. The first part of the challenge is a 100-meter dash and when Usain Bolt wins, King Arthur is held back by the weight of his armor and he is 90 meters behind. The second part of the challenge is a boxing match, and Usain keeps hitting King Arthur who keeps laughing at him as he is being protected by his armor. Then, out of the blue, King Arthur lands a knockout blow to Usain. Since the challenge was for charity and the result was a draw, they are both happy.
Concept:
The smaller the key, the faster it is, but it is more insecure. The higher the key, the slower it is, but it is more secure.
For the Security+ exam, you must know the characteristics of each of the symmetric algorithms, from when it is used to its key length. Remember, they will never ask you which key encrypts or decrypts, as the answer would always be the private key, also known as the shared key. Let us look at each of these in turn:
Advanced Encryption Standard (AES): AES comes in three key strengths: 128, 192, and 256 bits. The AES is commonly used for L2TP/IPSec VPNs.
Data Encryption Standard (DES): The DES groups data into 64-bit blocks, but for the purpose of the exam it is seen as a 56-bit key, making it the faster but weakest of the symmetric algorithms. This could be used for L2TP/IPSec VPNs, but is weaker than AES.
Triple DES (3DES): Triple DES (3DES) applies the DES key three times and is said to be a 168-bit key. This could be used for L2TP/IPSec VPNs, but is weaker than AES.
Rivest Cipher 4 (RC4): RC4 is 40 bits and is used by WEP and is seen as a steam cipher.
Blowfish/Twofish: Blowfish is a 64-bit key and Twofish is a 128-bit key, and both were originally designed for encryption with embedded systems. How can you remember which of these is faster as they have similar name? Easy. I have a pond with fish inside and I have a challenge with a guy called Tom. I need to catch two fish from the pond and he only needs to blow into the air. Guess what? He will win each time. Therefore, remember, Blowfish is faster than Twofish.
Diffie Hellman: When using symmetric encryption, symmetric algorithms need Diffie Hellman to create a secure tunnel before they can transfer encrypted data. Diffie Hellman is asymmetric as it uses public and private keys; it does not encrypt data, but its role is to create a secure session.
Asymmetric algorithms use a PKI environment as they use two keys: a private key that is always kept and a Public key that is always given away. Let us now look at different asymmetric techniques:
Diffie Hellman: Diffie Hellman does not encrypt data; its main purpose is to create a secure session so that symmetric data can travel down it. The Diffie Hellman handshake is shown in the following diagram:
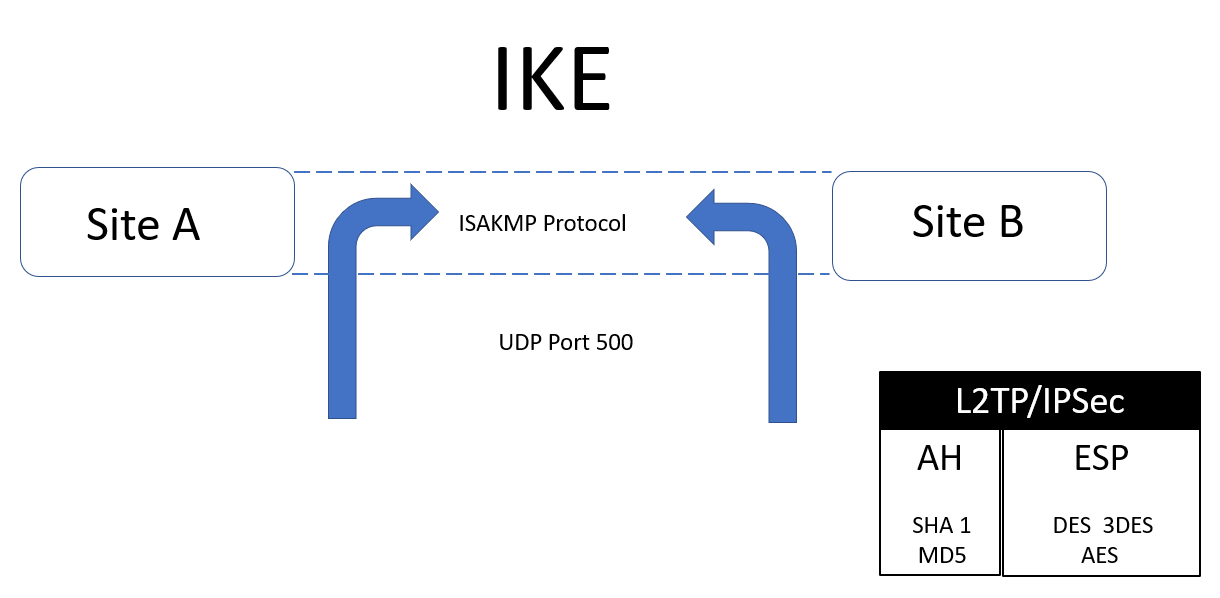
Figure 9: Diffie Hellman
Diffie Hellman creates the keys used in the Internet Key Exchange (IKE); it uses UDP Port 500 to set up the secure session for the L2TP/IPSec VPN. Once the secure tunnel has been created, then the symmetric encrypted data flows down the tunnel.
Rivest, Shamir, and Adelman (RSA): RSA is named after the three people who invented the algorithm. The keys were the first private and public key pairs, and they start are 1,024, 2046, 3,072 and 4,096 bits. They are used for encryption and digital signatures.
Digital Signature Algorithm (DSA): DSA keys are used for digital signatures; they start at 512 bits, but their 1,024-bit and 2046-bit keys are faster than RSA for digital signatures.
Elliptic Curve Cryptography (ECC): ECC is a small, fast key that is used for encryption in small mobile devices, however AES-256 is used in military mobile telephones.
Ephemeral keys: Ephemeral Keys are short-lived keys; they are used for a single session, and there are two of them:
Diffie Hellman Ephemeral (DHE)
Elliptic Curve Diffie Hellman Ephemeral (ECDHE)
Pretty Good Privacy (PGP): PGP is used between two users to set up an asymmetric encryption and digital signatures. For PGP to operate, you need a private and public key pair. The first stage in using PGP is to exchange the keys. It uses RSA keys.
GnuPG: GnuPG is a free version of the OpenPGP; it is also known as PGP. It uses RSA keys.
If we think of encryption as playing table tennis where each person has just one bat and the pace is extremely fast, this is similar to asymmetric encryption as it uses one key.
Then, if we change the game and we give the players two bats, the first bat to stop the ball and then they must switch bats to return the ball, this would be much slower.
The same can be said for encryption; asymmetric is much more secure as it has two keys and uses Diffie Hellman, an asymmetric technique to set up a secure tunnel for the symmetric data. Symmetric encryption uses a block cipher where it encrypts large blocks of data much faster than the asymmetric technique.