In this chapter, we are going to look at attacks and vulnerabilities. Each type of attack will have its own unique characteristics. This module is probably the most heavily tested module in the Security+ exam. This chapter needs to be thoroughly understood as sometimes those type of attack questions are very vague, so if you do not understand the concepts fully, you may not understand what is being asked.
We will cover the following exam objectives in this chapter:
Given a scenario, analyze indicators of compromise and determine the type of malware: Viruses—crypto-malware—Ransomware—worm—Trojan—rootkit—keylogger—adware—spyware—bots—RAT—logic bomb—backdoor
Comparing and contrasting types of attacks: Social engineering—phishing—spear phishing—whaling—vishing—tailgating—impersonation—dumpster diving—shoulder surfing—hoax—watering hole attack—principles (reasons for effectiveness)—authority—intimidation—consensus—scarcity—familiarity—trust—urgency. Application/service attacks—DoS—DDoS—man-in-the-middle—buffer overflow—injection—cross-site scripting—cross-site request forgery—privilege escalation—ARP poisoning—amplification—DNS poisoning—domain hijacking—man-in-the-browser—zero day—replay—pass the hash. Hijacking and related attacks—clickjacking—session hijacking—URL hijacking—typo squatting. Driver manipulation—shimming—refactoring. MAC spoofing—IP spoofing. Wireless attacks—Replay—IV—evil twin—Rogue AP—Jamming—WPS—Bluejacking—Bluesnarfing—disassociation—RFID—NFC. cryptographic attacks—birthday—known plain text/cipher text—dictionary—Brute force—rainbow tables—online versus offline—collision—downgrade—replay—weak implementations
Explaining penetration testing concepts: Active reconnaissance—passive reconnaissance—pivot—initial exploitation—persistence—escalation of privilege—penetration testing versus vulnerability scanning—black box—white box—gray box
Explaining vulnerability scanning concepts: Passively test security controls—identify vulnerability—identify lack of security controls—identify common misconfigurations—intrusive versus non-intrusive—credentialed versus non-credentialed—false positive
In this chapter, we are going to look at attacks and vulnerabilities. Each type of attack will have its own unique characteristics. This module is probably the most heavily tested module in the Security+ exam. This chapter needs to be thoroughly understood as sometimes those type of attack questions are very vague, so if you do not understand the concepts fully, you may not understand what is being asked.
We will cover the following exam objectives in this chapter:
Given a scenario, analyze indicators of compromise and determine the type of malware: Viruses—crypto-malware—Ransomware—worm—Trojan—rootkit—keylogger—adware—spyware—bots—RAT—logic bomb—backdoor
Comparing and contrasting types of attacks: Social engineering—phishing—spear phishing—whaling—vishing—tailgating—impersonation—dumpster diving—shoulder surfing—hoax—watering hole attack—principles (reasons for effectiveness)—authority—intimidation—consensus—scarcity—familiarity—trust—urgency. Application/service attacks—DoS—DDoS—man-in-the-middle—buffer overflow—injection—cross-site scripting—cross-site request forgery—privilege escalation—ARP poisoning—amplification—DNS poisoning—domain hijacking—man-in-the-browser—zero day—replay—pass the hash. Hijacking and related attacks—clickjacking—session hijacking—URL hijacking—typo squatting. Driver manipulation—shimming—refactoring. MAC spoofing—IP spoofing. Wireless attacks—Replay—IV—evil twin—Rogue AP—Jamming—WPS—Bluejacking—Bluesnarfing—disassociation—RFID—NFC. cryptographic attacks—birthday—known plain text/cipher text—dictionary—Brute force—rainbow tables—online versus offline—collision—downgrade—replay—weak implementations
Explaining penetration testing concepts: Active reconnaissance—passive reconnaissance—pivot—initial exploitation—persistence—escalation of privilege—penetration testing versus vulnerability scanning—black box—white box—gray box
Explaining vulnerability scanning concepts: Passively test security controls—identify vulnerability—identify lack of security controls—identify common misconfigurations—intrusive versus non-intrusive—credentialed versus non-credentialed—false positive
In today's world, viruses and malware and rife; there are many different variants and we will look at each of these in turn:
Virus: A virus is a program that embeds itself into a program and is executed in many different ways, for example by clicking on a link on a web page or opening up an email attachment. Once it has been activated, it replicates itself, going from host to host. A lot of viruses use port 1900.
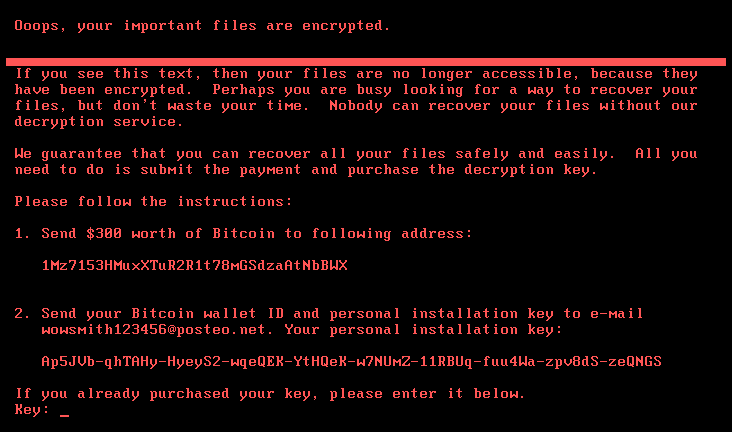
Ransomware: Ransomware is when the attacker encrypts the files on a user's computer and then a link comes up asking for money to release the files. An example of this is shown in the following screenshot. Ransomware could also be when you download a free program and it says that you have problems with your computer so you need to purchase the full version of the software. Remember, this is quite subtle—the rule of thumb is that if you have to part with money, then it is ransomware:

Figure 1: Ransomware
Crypto-malware: Crypto-malware is a type of ransomware that encrypts a user's files and demands ransom. Sophisticated crypto-malware uses advanced encryption methods so that files cannot be decrypted without a unique key.
Worm: A worm is a program that replicates itself to spread to other computers, exploiting weaknesses in security. Common ports are 1098, 4444, and those in the 5000 range. An example of a worm is Nimda. The Nimda virus was released in September 2001; its name is admin spelt backwards and that referred to a file called admin.dll. When it runs, it continues to propagate itself. The main target of Nimda was Microsoft's IIS web server and file servers. It would create a Denial of Service attack and its job was to simply slow down networks to a halt. When it accessed a server, it would run down mapped network drives to everyone connected to the server, then it rewrote the system files so that they had an EML extension. Once it had totally destroyed a machine, a huge white envelope appeared on the desktop; this meant that it would no longer function.
Trojan: Trojans are known for creating a backdoor on your computer that gives malicious users access to your system, stealing confidential or personal information. They try to exploit system32.exe and then run a DLL file to attack the operating system kernel; this is the management of the operating system. The Trojan will try and find password information, so set up a SMTP engine that uses a random port to send these details to the attacker.
Trojans attack the /System 32 and the SysWOW64 directory by placing a .dll file there.
Trojan.BHO.H File C:\WINDOWS\SysWOW64\fezegepo.dll
Trojan.Vundo File C:\WINDOWS\system32\fezegepo.dll
For example, Ghost RAT is a remote access Trojan that was originally designed by threat actors in China. A user clicks on a link and a dropper program called server.exe installs Ghost RAT with a svchost.dll that then allows the attacker to take control of the computer. It can then log keystrokes, download and upload files, and run a webcam and microphone feeds.
Remote Access Trojan (RAT): A RAT is a program that sends login details back to the attacker to enable them to take full control of the computer.
Rootkit: A rootkit is a designed to enable access to a computer or areas of its software that is not otherwise allowed to access. For example, it could be either c:\windows\system32 for a Windows computer or bin/ and /usr/bin/ for Linux/Unix computers.
Backdoor: A backdoor in a piece of software or a computer system that is created by the program developers in case someone locks themselves out of the program; it is generally undocumented. Attackers use this to gain access to the system.
Logic bomb: A logic bomb is a virus that is triggered by either an action or a time; an example would be the Fourth of July or Christmas Day. On March 20, 2013, in South Korea, a logic bomb dictated the date and time, and the malware began erasing data from machines to coordinate the destruction across multiple victims. The malware consisted of four files, including one called AgentBase.exe that triggered the wiping. Contained within that file was a hex string (4DAD4678) indicating the date and time the attack was to begin—March 20 2013 at 2 p.m. local time (2013-3-20 14:00:00). As soon as the internal clock on the machine hit 14:00:01, the wiper was triggered to overwrite the hard drive and master boot record on Microsoft Windows machines and then reboot the system. It attacked the government and banking sector.
In a Linux environment, a rootkit virus attacks the /usr/bin directory.
Keylogger: The main idea behind keyloggers is to track and log keystrokes; you can install the keylogger by putting it on a very small thin USB drive on the rear of a desktop computer. It will never be seen.
Adware: Adware is an unwanted program that keeps popping up with unwanted advertisements. One way to stop adware is to enable a pop-up blocker.
Spyware: Spyware is renowned for slowing down computers as it uses your computer's processor power and RAM resources to continually track what you are doing on your computer and send the information to a third party.
Botnet: A bot is a program that takes over control of a computer; a botnet is a collection of bots that have been set up for malicious purposes normally to carry out a Denial of Service (DoS) attack.
Social engineering attacks rely on someone's personality as they try to exploit them. There are various social engineering attacks; let's look at each of them and the principles of why they are effective:
Phishing and spear phishing: Phishing attacks are done by emailing someone who tells you that your account is going to expire so you need to complete the attached form. They ask you for all of your personal details that could be later used for identity fraud. The email looks as if it has come from a legitimate body, so the user is fooled into carrying out the required instructions:
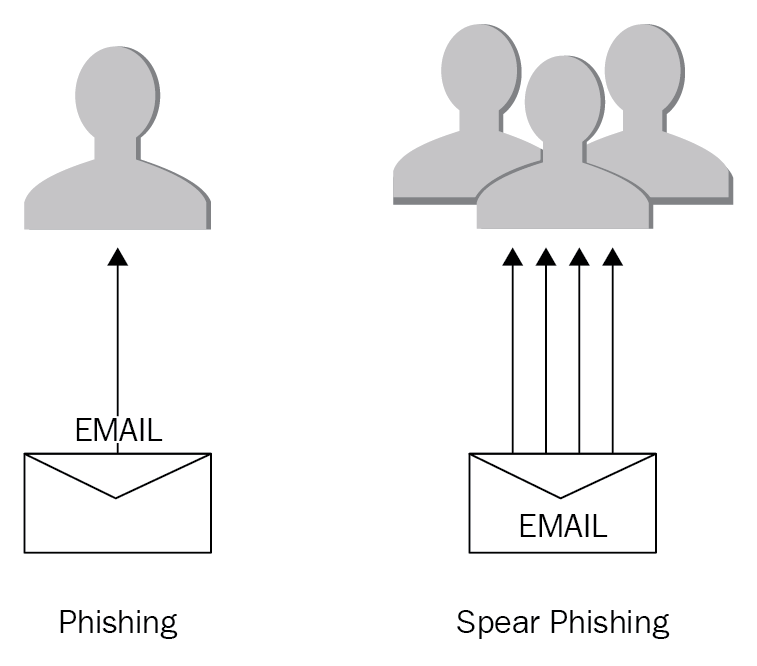
Figure 2: Phishing attack
Whaling: A whaling attack targets either a chief executive officer or a high-level executive. CEOs and high-level executives have intense days, so what looks like a minor request they action quickly so that they can get their next task done and end up being attacked.
Vishing: A vishing attack uses a VOIP phone, another telephone, or someone leaves a voicemail to try and extort information.
Tailgating: Tailgating is where someone opens a door using their ID badge and then someone follows them in before the door closes. This is especially effective if the person going through first is a middle-aged man and the tailgating person is a pretty lady—they made be old school and keep the door open for the lady.
Impersonation: Impersonation is when someone will put on the uniform of a traffic warden or policeman. An example of this is when you are driving down the road and you are flagged down by a policeman—he is holding something that looks like a speed gun. He tells you that you have been speeding and this will result in penalty points on your license if it goes to court, or you can pay an on-the-spot fine of $40. You pay the fine, he gives you a receipt. This is effective as the victim is not expecting this to happen and most people in the situation panic and pay the fine.
Dumpster diving: Dumpster diving is where someone removes the trash from your trash can in the hopes that a letter holds Personally Identifiable information (PII) that can be used later to commit fraud. The best way to prevent this is to shred all mail that has PII information before you dispose of it. This is effective as most people just throw letters in the bin without a second thought.
Shoulder surfing: Shoulder surfing is where a person is standing behind someone using a computer so that they can see sensitive information. Another example is where someone is using an ATM cash machine and the person behind them is using their smartphone to video the transaction. This is effective as the victim is concentrating on withdrawing their money and is not aware of being watched.
Hoax: The jdbgmgr.exe virus hoax involved an e-mail spam (https://en.wikipedia.org/wiki/Email_spam) in 2002 that advised computer users to delete a file named jdbgmgr.exe because it was a computer virus (https://en.wikipedia.org/wiki/Computer_virus); see following figure:
Figure 3: Hoax virus
This email said that this cute little bear was a virus and it should be deleted, as anti-virus software from anti-virus vendors would not find it; this was true as it was not a virus. It was an operating system file and to delete it would damage your computer. The reason why this attack worked was the bear was there and the anti-virus did pick it up on a scan, therefore it looked real. Another example of a hoax would be purchasing fake anti-virus software that does not work.
Watering hole attack: Companies from the same industry visit very similar websites, therefore the attacker identifies a website that members of that industry are likely to visit and then infects it with a virus. This is effective as the people that they target have been using this website for years and trust the content from it.
Authority: An email may be sent out by someone of authority such as the CEO or HR manager ordering you to complete a form that can be accessed by clicking on a link; see the following e-mail. This is effective as nobody wants to defy the Chief Executive Officer (CEO):
From: Ian Neil (CEO)
To: All Staff
Subject: UPDATE YOUR FINANCIAL DETAILS
Dear All
The finance team are moving to a new finance application and have told me that personnel within the company have not updated their bank details. You need to click on this link and update your details: http://update.details.wehackyou.com.
Failure to do so by the end of play today will result in disciplinary action against those individuals that do not comply:
Kind Regards
Ian Neil
Chief Executive Officer
Intimidation: Intimidation is where someone pretends to be someone of high authority, for example, a policeman; they then threaten the person so that if they don't do as they are told that they will be in trouble. This is effective as the person dealing with this attack is made to believe that they have no other choice but to do as asked.
An email from your CEO, a high-level executive, or the HR manager telling you to fill in a form or click on a link is a social engineering authority attack.
Urgency: Urgency is where someone arrives at a reception desk and demands access quickly; they could target a new receptionist who may get flustered and let them in. A good example of this is when a fireman demands access to the server room before the building burns down. This is effective as the receptionist panics as they believe that there is a fire.
Allowing a fireman into your server room is a social engineering urgency attack.
Scarcity: This attack is like trying to buy a room for a weekend away; you and 10 friends pick a hotel and go onto the website and it says only one room left in red. You purchase this last room, and so do your 10 friends, and guess what? There is still only one room left! Another example is: while the CEO is in a conference, his personal secretary receives a phone call from someone claiming to be in charge of domain names. The secretary is told that he is ringing her to renew the domain name and that it must be done in the next 30 minutes or else the company will lose their domain name. He states that the renewal would be $45. The secretary knows that the company website and email addresses cannot operate without the domain name. This is effective as she cannot disturb the CEO during an important meeting, so she purchases the domain name renewal. It may well be 3—4 months away.
Familiarity and trust: Hackers make themselves familiar to those around them, and they come around a lot, and eventually they become trusted. At that point, they can begin working their way inside the company, gaining access to areas of the company that they should not be able to access. This is effective as they become part of the furniture and nobody questions their actions.
Consensus: People like to be accepted by their peers and co-workers; someone might ask for some information and state that he/she obtained this information last week from a co-worker and just needs to update it. This works as the person supplying the information does not want to be seen as acting differently from other members of the team. Sometimes, this is referred to as social proof.
If you are going to gain the CompTIA Security+ qualification, you need to know the different types of attacks that you may encounter; there are numerous attacks and you need to know each of these, their characteristics, and how they can be prevented. Let's look at each of these in turn.
Denial of Service Attack (DoS): A denial of service attack is where the victim is flooded with a high volume of requests from another host so that it is not available for any other hosts to use. A common method of this is SYN flood attacks where the first two parts of a three handshake occur and the victim is holding a session waiting for the ACK that never comes.
A SYN flood attack is where only the first two parts of the three-way handshake have taken place, leaving your computer is a state of limbo. DDoS has a high volume of these.
Distributed Denial of Service Attacks (DDoS): A DDDoS attack is where a botnet is set up to flood a victim with an enormous amount of traffic so that is taken down; you can see in Figure 4 that an attack coming from China took out the Facebook network. Look at the enormous amount of traffic; luckily enough, Facebook is very well-organized and was back up and running within 30 minutes. Stateful firewalls are set up to prevent DDoS attacks from gaining access to your network:
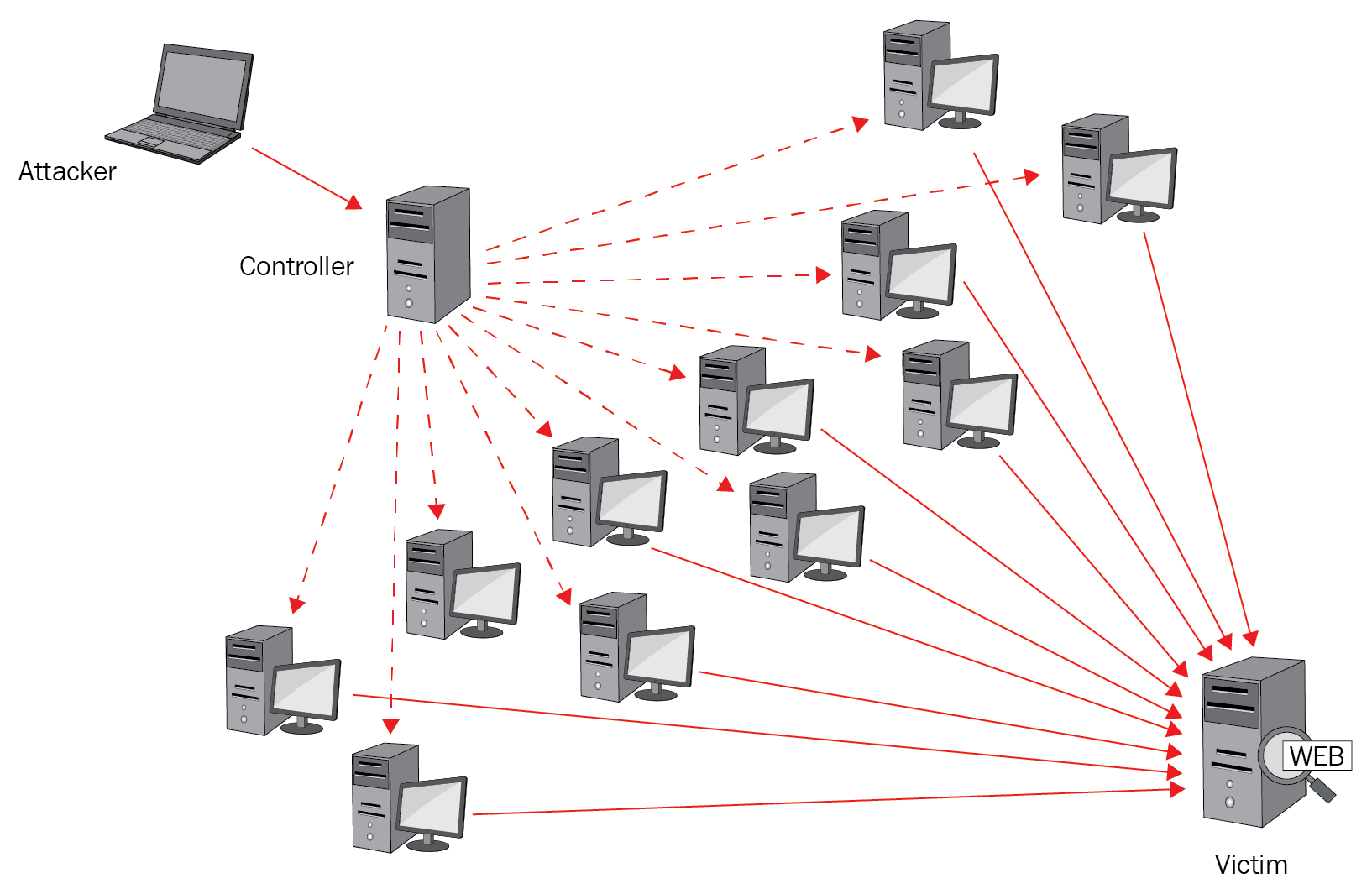
Figure 4: DDOS attack
Amplification attack: A DNS amplification is a Distributed Denial of Service (DDoS) attack in which the attacker exploits vulnerabilities in DNS servers to turn initially small queries into much larger payloads, which are used to bring down the victim's servers.
Man-in-the-Middle (MIM) attack: A MIM attack is where the attacker intercepts traffic going between two hosts and then changes the information in the packets as it going between them in real time. See Figure 5, where Mary is contacting Carol, but John is the man-in-the-middle and changes the conversation as it goes backwards and forwards. A man-in-the-middle can inject false information between the two hosts:
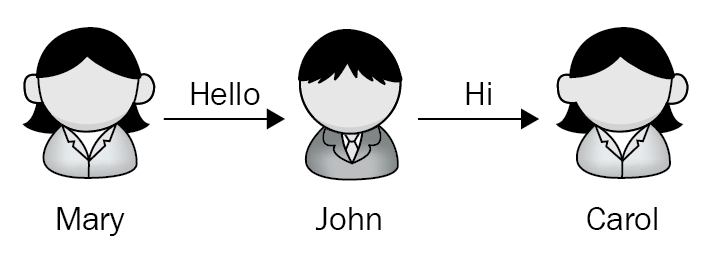
Figure 5: Man-in-the-middle
For example, a hacker is imitating the conversations of both parties for gaining access to funds. The attacker intercepts a public key and with this he can put in his own credentials to trick the people on both sides into believing that they are talking to each other in a secure environment. While online shopping from home or a mobile device, the victims think that they are buying goods from a legitimate source but instead their money is being stolen.
Man-in-the Browser (MITB) attack: The MITB attack uses the same approach as a man-in-the-middle attack (https://www.owasp.org/index.php/Man-in-the-middle_attack), but in this case a Trojan is used to intercept and manipulate calls between the main application's executable (the browser) and its security mechanisms. The most common objective of this attack is to cause financial fraud by manipulating transactions of internet banking systems, even when other authentication factors are in use.
Exam tip:Kerberos prevents replay attacks as it uses updated sequence numbers and time stamps.
Padding Oracle on Downgraded Legacy Encryption (POODLE): A Padding Oracle on Downgraded Legacy Encryption (POODLE) attack is a man-in-the-middle attack that exploits the use of SSL 3.0 on legacy systems; this is extremely insecure. Encryption in SSL 3.0 uses either the RC4 stream cipher or a block cipher in CBC mode. A downgrade attack is when you abandon a higher level of security for an older low-level security system; in this case we are downgrading the computer's browser to an older version of the browser SSL 3.0 using CBC.
Replay attack: A replay attack in a man-in-the-middle attack that intercepts the data but replays it at a later date. Kerberos, a Microsoft authentication protocol, can prevent this as each entry has updated sequence numbers and time stamps. For example, communication takes place between two hosts on a Windows network that uses Kerberos authentication. Data is being transmitted with USN 7 appearing and then USN 10 appears; the receiving host will then realize the data is not as it should be. When USN and USN 8 or USN 9 are received the next day, they will be rejected as being out of sequence, preventing the replay attack.
A POODLE attack is a MIM downgrade attack using SSL 3.0 in CBC mode.
Zero day attack: A zero day attack is when an exploit has been found but at this time there is no solution to prevent it, so the attackers attack more, as there is no solution to prevent or detect the attack unless you have previously taken a baseline. If we look at Figure 6, we can see when the exploit happens. It takes two more days for a solution to prevent it—no anti-virus, SIEM, NIDS, or NIPS will be able to stop the zero day attack as they have don't have the ability to detect it that day. They will be waiting for an update:
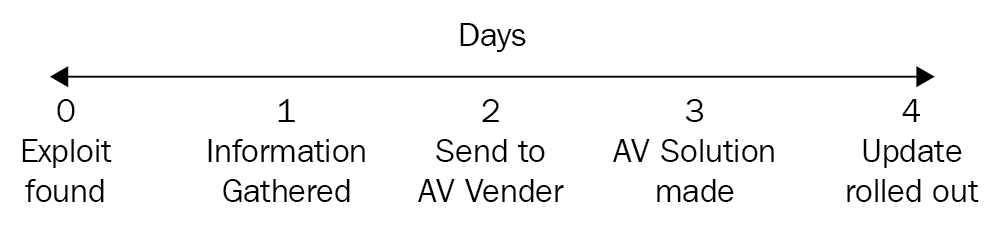
Figure 6: Zero day exploit
The only way to detect a zero day exploit is when you have taken a baseline of your computer previously, then you can check the changes since the baseline; this will identify a zero day exploit. If you have no previous baseline, then you will not detect it.
Pass the hash attack: The attacker first obtains the hashes from the targeted system that is using an NT Lan Manager (NTLM) using any number of hash-dumping tools. They then use a pass-the-hash tool to place the obtained hashes on a Local Security Authority Subsystem service. A Windows-based authentication system believes that the attacker is a legitimate user, and will automatically provide the required login credentials. This can all be accomplished without any need for the original password, and account lockout cannot be enforced as this attack is operating at a lower layer. You need to disable NTLM to prevent the passing of the hash attack.
Domain hijacking: Domain hijacking is where someone tries to change the domain registration of a domain with the internet authorities so that they can control the domain for profit. For example, an attacker manages to re-register the domain name of a well-known company and can now access the control panel with the original domain's company called Hosting A. He then takes out a hosting package with Hosting B, where he copies over all of the files from Hosting A and moves them into Hosting B. He then points the DNS Records to Hosting B, where he can take sales from customers who believe they are trading with the original company.
A zero day virus cannot be traced or discovered by any security device as it may take up to five days before a patch or update is released.
DNS poisoning: When DNS resolution occurs, the first place that is checked is the DNS cache on the local machine; after that, it goes to the hosts file and then onto the DNS server. DNS poisoning is the process of putting bad entries into the DNS cache, diverting the request to the fraudulent website that has been made to look like the legitimate website. See Figure 7:
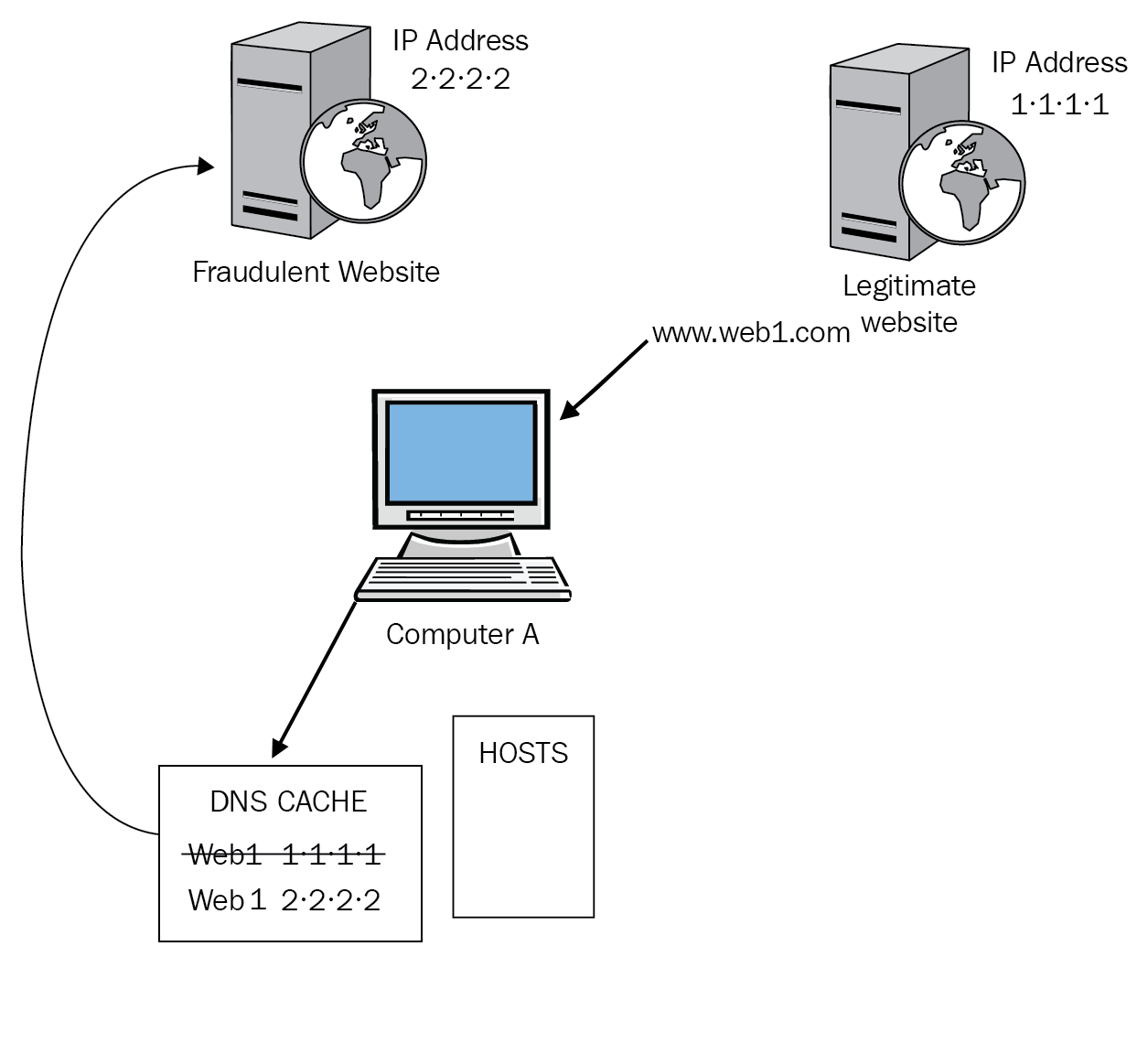
Figure 7: DNS poisoning
If we look at Figure 7, Computer A has already been to the legitimate website called Web 1, and its proper IP address of 1.1.1.1 has been placed in its DNS cache. When DNS resolution is performed, the DNS cache is searched first then the hosts file is next, followed by the internal DNS server. The attacker has now deleted the entry for Web 1 and inserted his entry for Web 1 with an IP address of 2.2.2.2. Now, when the user enters the URL www.web1.com, the only entry in the DNS cache is Web1 2.2.2.2 and the user is diverted to a website that looks like the legitimate website. When he enters his card details to make a purchase, his account is emptied.
DNSSEC: DNSSEC encrypts DNS traffic and is designed to prevent DNS spoofing attacks and DNS cache poisoning and prevents your DNS queries traffic from being captured. DNSSEC produces RRSIG records for each entry in the DNS database.
ARP poisoning: ARP operates at Layer 2 of the OSI reference model and operates using MAC addresses. ARP poisoning is an attack that must be done locally. ARP cache poisoning, or ARP poison routing, is where an attacker sends (spoofed) Address Resolution Protocol (ARP) messages to a local area network. ARP spoofing may allow an attacker to intercept data frames on a network, modify the traffic, or stop all traffic. ARP poisoning can be prevented by using IPSec tunnels across your internal network.
MAC spoofing attack: MAC spoofing is where you steal the Media Access Control (MAC) address of another networked device and use it to gain access to the network, for example a wireless access point that uses MAC filtering.
IP spoofing: IP spoofing is the creation of Internet Protocol (IP) packets with a false source IP address to hide the identity of the sender or to impersonate another computing system so that they cannot be traced when they carry out a malicious attack.
Privilege escalation: A privilege escalation attack is where an attacker wants to grant himself more permissions than he is entitled to. With a higher level of privilege, the attacker will be able to run unauthorized code or make changes to the IT infrastructure. They may try to use someone else's account to access the active directory and allocate themselves a higher level of privilege. For example, John, an administrator, leaves his laptop unattended when the boss asks him to come into his office. Mary, who is a normal user, goes into John's laptop and clicks on the shortcut to the directory service and makes herself a member of the administrator's group. When John comes back, he does not realize anything has happened as his laptop seems the same as when he left it.
Programming attacks are when we use scripts or overload the expected characters or integers expected. Let's look at these in turn:
Christmas tree attack: A Christmas tree attack is where the packet has a number of flags or settings set to open. An example is that the flags are set to one; for example the URG, PUSH, and FIN flags are all set to a value of 1, meaning that they are open. A large number of these data-heavy packets can slow down or overload a network. As the URG is set to 1, this means that this packet should have a higher priority over other packets.
Dynamic Link Library (DLL) injection: It is a technique used for running code within the address space of another process by forcing it to load a DLL. This makes the application run differently than first designed. For example, you could install a malware DLL into another process.
Cross-site request forgery (XSRF): An XSRF attack is where a user clicks on the link of a legitimate website where embedded programming is executed. An XSRF attack can be used to modify firewall settings (https://searchsecurity.techtarget.com/definition/firewall), post unauthorized data on a forum, or conduct fraudulent financial transactions. A compromised user may never know that such an attack has occurred until the loss of money has been discovered.
Exam tip:
In a Christmas tree attack, the URG, PUSH, and FIN flags are all set to 1, meaning that they are open. As URG is set to 1, it says that this packet has a high priority over other traffic.
Cross-site scripting (XSS): XSS is where a user can inject malicious code inside another user's browser. It uses both HTML tags and JavaScript. The following is a very simple server-side script to display the latest comments:
print "<html>"
print "Latest comment:"
print database.latestComment
print "</html>"
The attacker could alter the comment to have HTML tags for a script, as follows:
<html>
Latest comment:
<script> (Javascript code is placed here) </script>
</html>
When the user loads the page into the browser, it will now launch the JavaScript and then the attack would be successful. Here are some examples of using JavaScript.
JavaScript can use the command var that means variable; an example would be to set a variable for money then allocate it a value of 300.00. You can see we use var for the variable and then use money as its label. In the next row, we use the money variable and give it a value of 300.00:
<script type="text/javascript">
<!——
var money;
money = 300.00;
//-->
</script>
We will use Javascript to set the day of the month; you will notice the Javascript code between the html tags <script> to start the script and <\script> to end the script. The command var is very common in Javascript:
<!DOCTYPE html>
<html>
<body>
<p>Click the button to display the date after changing the day of the month.< /p>
<button onclick="myFunction()">Try it</button>
<p id="demo"></p>
<script>
function myFunction() {
var d = new Date();
d.setDate (15);
document.getElementById("demo").innerHTML = d;
}
</script>
</body>
</html>
A XSS attack can be identified by looking for the command var and for a variable with the html tags <script> and </script>. Scripts with var are likely to be Javascript. It is a very popular exam topic:
Buffer overflow: A buffer overflow occurs when a program tries to store more data than it can hold in a temporary memory storage area. Writing outside the allocated memory into the adjacent memory can corrupt the data, crash the program, or cause the execution of malicious code that can allow an attacker to modify the target process address space:
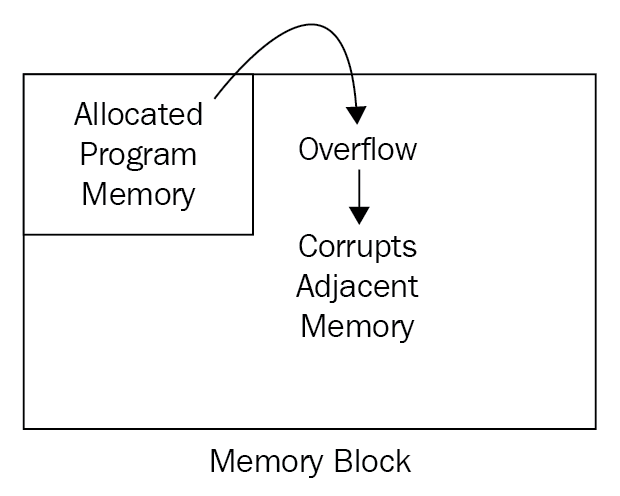
Figure 8: Buffer overflow
In the example here, we are going to set up a buffer to be a maximum of 64 characters, then we are going to use strcpy to copy strings of data. A string of data is used to represent a number of text characters. The problem that arises is that strcpy cannot limit the size of characters being copied. In the example here, if the string of data is larger than 64 characters, then a buffer overflow will occur:
int fun (char data [256]) {
int i
char tmp [64];
strcpy (tmp, data);
}
Integer overflow: An integer overflow is the condition that occurs when the result of an arithmetic operation, such as multiplication or addition, exceeds the maximum size of the integer type used to store it. It is similar to buffer overflow but uses numerical values this time. It will not overflow into memory as it is not being written to memory but can lead to unexpected values being stored. An integer data type allows integers up to two bytes or 16 bits in length (or an unsigned number up to decimal 65,535); when the two integers are to be added together that exceed the value of 65,535, the result will be an integer overflow.
SQL injection attack: When you use a SQL database, you can run queries against the SQL database using transact SQL. An example is if I want to know the customers that I have in my SQL database. I can run the following transact SQL query: Select* from Customers. This will display all of the customers in my SQL database. An SQL injection attack is where the SQL command is modified to gain information from the database by ending the statement with 1=1. Since one does equal one, the statement is true and information will be gained.
Exam tip:Strcpy could create a buffer overflow as it cannot limit the size of the characters.
Stored procedure: A Stored Procedure is a pre-written SQL script that might ask you for a list of all customers that have purchased items over $1,000 in the last 7 days. When this is written, it is saved as a Stored Procedure called ABC. When I run the ABC stored procedure, it will give me all of the information I require, but an attacker cannot modify the script inside.
Input validation: Input Validation is where data is entered either using a web page or wizard; both have been set up to only accept the data in the correct format within a minimum and maximum value, a range. Have you ever completed a web form quickly and maybe put your zip or post code into another field? This results in an error in the form and it fails to process the submit button. The web form then has a list in red at the top, of the incorrect parameters, with a red star next to each of these. Once you have corrected the entries, then the form will accept these and submit. Input validation can prevent, SQL injection, buffer overflow, and integer overflow attacks.
In this section, we will look at attacks where he hacker hijacks either a device, cookie, or a piece of software. Let's look at these in turn:
Bluejacking: Bluejacking is where the attacker has taken control of a Bluetooth device such as a phone. They are then able to make phone calls, send text messages, and even message your friends so that they dislike you.
Bluesnarfing: Once again, an attacker is hijacking your Bluetooth phone but this time they are extracting your contact details or any sensitive information from your phone.
Input validation could prevent SQL injection, buffer overflow, and integer overflow attacks.
Session hijacking: When you visit a website, your desktop can store your browsing information in a file called a cookie. This is a security risk as it can used to identify you. For example, the second time you visit a website it may say at the top: Good Morning Mr Smith. If someone can copy your cookie and place it on their machine, the website will also see them as Mr Smith. This is known as session hijacking.
URL hijacking: URL hijacking is a process in which a website is falsely removed from the results of a search engine and replaced by another web page that links to the remote page. Another form is typosquatting.
Typosquatting: When someone types in the URL of a website into their browser, they may transpose two characters of the website name as they have typed it very quickly. Typosquatting is where the attacker creates websites with those transposed names to redirect their session to a fraudulent website. This is also known as URL hijacking.
A stored procedure could prevent a SQL injection attack as it is a pre-written script that is executed and cannot be altered when executed.
Clickjacking. Clickjacking is a malicious technique of tricking a web user into clicking on an icon or link. The outcome is different from what the user perceives they are clicking on, thus potentially revealing confidential information or taking control of their computer. An attacker establishes a malicious website that invisibly embeds the Facebook Like or Share button in a transparent iframe. When the victim clicks within the malicious site, the click is directed to the invisible Like or Share button.
Device drivers allow an operating system such as Windows to talk to hardware devices such as printers. Sophisticated attackers may dive deep into the device drivers and manipulate them so that they undermine security on your computer. They could also take control of the audio and video of the computer, they could stop your anti-virus software from running, or your data could be exposed to someone else. There are two main techniques for driver manipulating, and these are as follows:
Shimming: A shim is a small library that transparently intercepts API calls and changes the arguments passed. They also can be used for running programs on different software platforms than they were developed for. Normally, it is to help third-party software applications work with an operating system.
Refactoring: Refactoring is the process of changing a computer program's internal structure without modifying its external functional behavior or existing functionality.
There are a variety of cryptographic attacks, and we will now look at these in turn; you need to know these thoroughly for the Security+ exam. We will start with the birthday attack and finish with key stretching:
Birthday: The birthday paradox states that in a random gathering of 23 people, there is a 50% chance that two people will have the same birthday. If we store passwords as hashes, then all passwords that are the same will produce the same hash if we are using the same hashing algorithm. The birthday looks for collisions in hashes; if they find two hashes of the same value, the attacker also knows that the password is the same.
Digital signatures: Digital signatures can be to a attack.
Rainbow tables: Rainbow tables are lists of pre-computed passwords with the corresponding hash; you can obtain free rainbow tables from the internet. Some of the larger rainbow tables are 460 GB in size. These tables speed up the cracking of passwords that have been hashed.
Collision attack: A collision attack on a cryptographic hash tries to find two inputs producing the same hash value; this is known as a hash collision.
Salting passwords: Salting password values is where a random set of characters is inserted into the password hash. This prevents duplicate passwords being stored and prevents rainbow tables and collision attacks. This also creates a longer password, slowing down brute force attacks.
Key stretching: Key stretching is similar to salting a password by inserting random strings to prevent rainbow table and collision attacks. Bcrypt and PBKDF2 can be used for key stretching. For example, a company has a password policy of not using complex passwords and therefore have suffered many attacks. To prevent this in the future, they use Bcrypt to key stretch the weak passwords, making it more difficult to crack. They should have also introduced both complex passwords and key stretching to make the passwords more secure.