In this chapter, we will be learning about the deployment and security issues of virtualization. We will get acquainted with the deployment and storage environments of the cloud models. We will also learn about different scenarios to learn when to use on-premises, hosted, and cloud environments.
We will cover the following exam objectives in this chapter:
Summarize cloud and virtualization concepts: Hypervisor—Type I—Type II. Application cells/containers. VM sprawl avoidance—VM escape protection. Cloud storage—cloud deployment models—SaaS—PaaS—IaaS—private—public— hybrid—community. On-premises versus hosted versus cloud. VDI/VDE. Cloud access security broker. Security as a service.
Explain how resiliency and automation strategies reduce risk: Elasticity—scalability—distributive allocation—redundancy—fault tolerance—high availability—RAID.
The demand for cloud services has risen in recent years as the workforce has been more mobile; the cloud solution is very cost-effective and maintains the high availability of systems. Before you decide to move to a cloud service provider (CSP), you need to ensure that you trust them 100%.
This module will look at different cloud models, coupled with cloud storage and how machines in the cloud are created. There are many good reasons why cloud computing has become popular:
Elasticity: The cloud is like a pay-as-you-go model where one day you can increase resources and then the next day you can scale down the resources. You can even add more processor power, faster disks, more memory, or dual network cards whenever you want—there's no need to wait for delivery times, but the cost increases:
Example 1: A toy firm is hiring 50 temporary workers from October onward to deal with the rush for toys at Christmas. If the toy company were not on the cloud, they would have to purchase another 50 high desktops, but instead they lease virtual machines from a CSP. Once the Christmas rush has ended, the lease of their machines ends. You only pay for what you need.
Example 2: An IT training company uses 12 laptops for the delivery of different courses. Each week the image changes and they have to roll it out 12 times—this is time-consuming. Images are stored in a library on a file server.
When they move to the cloud, they just roll out one image and the CSP clones it so they don't need to reimage each laptop. Today, they are delivering Word 2016, therefore the cloud machines need an i5 processor with 4 GB of RAM for 2 days. They go to a CSP and lease the hardware specification that they need.
The next week, in another location, they will deliver Skype for Business, so there is no need to reimage the laptops but they now leave quad i7 processors with striped disk sets and 64 GB of RAM. The course is now for 5 days, so it is longer and more expensive. The image is uploaded and the cloud machines are upgraded, resulting in a much higher cost as they are using more resources. They do not need to purchase the additional hardware and the setup is more cost-effective.
Scalability: Scalability is the ability of a company to grow while maintaining a resilient infrastructure. The cloud enables a company to grow and grow without the worry of needing to make capital expenditure while doing so. It enables the company to grow faster than an on-premises company that needs to invest more money into bricks and mortar. As the cloud allows elasticity, it goes hand in hand with becoming scalable. As your company grows, the cloud provider can allow you to lease more resources. If at any time you want to reduce the amount of resources needed, the cloud provider can also reduce resources.
Example: Company A is a newly formed business that has hit the marketplace running; there is a need for the company to rapidly expand and open new offices in Chicago and London, as sales in those locations are astronomical.
Normally, when a new site is opened, it needs to invest $50,000 in IT equipment, so the company has turned to a cloud model for the new equipment. They will lease the offices until sufficient sales have been made to invest in purchasing a property. All of the employees will have laptops and high-speed fiber broadband.
The network infrastructure will be cloud-based, therefore there is no need to purchase physical servers that would have an impact in reducing their cashflow. Cashflow is maintained, even though new equipment has been provided.
No capital expenditure (capex): When you move your infrastructure to the cloud, there is no capital expenditure; normally IT resources have a maximum lifespan of 3-5 years. As technology keeps moving and hardware becomes obsolete, this means they may have to find $50-100,000 every 5 years just for hardware.
Example: A company is looking to upgrade their desktops and servers with the cost of hardware being $250,000 and a disposal fee of $25,000 in 5 years' time.
If they move to the cloud, it is going to cost them $60,000 a year. However, they don't need to find the whole $250,000 in one lump sum as the CSP will update their hardware perpetually so that the hardware will never be obsolete.
It will also help the company maintain a better cashflow, as capital expenditure is not required. The difference in price is 1.8% higher per year, which could be justified as there are no maintenance fees or disaster recovery site required, making it very cost-effective. The CSP deals with maintenance and disaster recovery as part of the cloud plan.
Location-independent: As you are accessing the cloud through a browser, it is location-independent, therefore it offers faster recovery if your premises have a disaster.
Example: One of your company offices is located in Northern California and recently was burned down by a wildfire, however, since your data and infrastructure are cloud-based, you can operate quickly from another location as long as you have internet access. If you had a traditional network, the infrastructure would have been burned down, your desktops would have been gone, and it could take a week or two to get back to an operational state.
Regional storage of data: The cloud is regulated, therefore data from a country must be stored within that region as laws on data compliance can change from region to region.
No maintenance fees: The CSP provides ongoing maintenance, so when the cloud contract is signed there are no hidden costs.
No disaster recovery site required: The CSP provides a 99.999% availability of its IT systems, therefore, once your data is in the cloud, there is no requirement for a disaster recovery site as the CSP provides that as part of the contract.
Exam tip:
Private cloud = single tenant. Public cloud = multitenant.
Community cloud = same industry.
We will first of all look at the different cloud models and their characteristics, the most common cloud model is the public cloud, so let's start with that:
Public cloud: The most common model, where the CSP provides cloud services for multiple tenants. This is like being one of many people who rents an apartment in an apartment block:

Figure 1: Public cloud
Just like in the public cloud, none of the tenants owns their apartment.
Example: A small company does not want to invest $50,000 in IT systems, so they purchase their cloud package from a cloud provider where they and another company are hosted by the cloud provider. This is similar to someone renting one apartment in a block from a landlord—you lease but do not own the flat. This is a multitenant environment where the cloud provider has multiple companies on the same virtual host.
Private cloud: A private cloud is where a company purchases all of its hardware from. They normally host their own cloud because they do not want to share resources with anyone else, but at the same time, their workforce has all of the mobile benefits of the cloud. It is similar to someone buying a house because they want privacy. The private cloud needs isolation from other companies, which is why it is known as single-tenant:

Figure 2: Private cloud
Example: An insurance company wants its sales staff on a cloud environment where they can access resources from anywhere—whether they are at home, at a customer's site, or in a hotel room. The problem they have is that they do not wish to share resources with other cloud tenants. Therefore, they purchase the hardware and their IT team hosts its own private cloud. The benefit of this is that the sales team can access any resources they want at any time of day or night.
It is known as single-tenant, but like owning your own home, they buy the equipment.
Community cloud: The community cloud is where companies from the same industry collectively pay for a bespoke application to be written, and the cloud provider manufacturers host it:
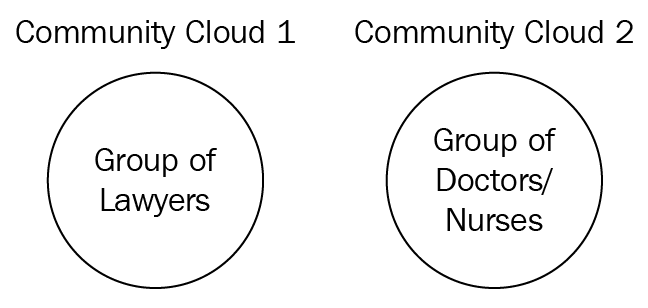
Figure 3: Community cloud
In the preceding diagram, you can see lawyers on the left-hand side and on the right-hand side is a group of medical people—doctors and nurses. The lawyers cannot share the same software package as medical people, since they have different requirements. Therefore, Community Cloud 1 is for lawyers who have brainstormed and financed the perfect legal application, which is hosted in the cloud—this is private to them. Community Cloud 2 is for a group of medical people, it could maybe be two hospitals, who have designed and shared the cost of making the perfect medical software package, which is hosted by the CSP.
Example: There is no application that can provide all of the functionality required for pawnbrokers to list the assets that have been pawned with the payment made against each asset. Then, they need assets that have not been reclaimed to be sold on the internet, as well as being sold in their shops.
Three of the largest pawnbroking companies enter into a business venture where they get together and design the perfect application to enable their companies to be more efficient and save labor costs over time. The cloud provider creates this application and hosts it. This saves them the costs of purchasing new hardware. The cloud provider will also back up the data each night and guarantee a 99.99% availability of the systems. This is known as a community cloud as the application is no good to anyone who is not a pawnbroker.
Hybrid cloud: Companies that decide not to host their company in the cloud are known as on-premises, but during their peak time they may expand into the cloud—this is known as cloud bursting. A mixture of both on-premises and cloud is known as a hybrid model:
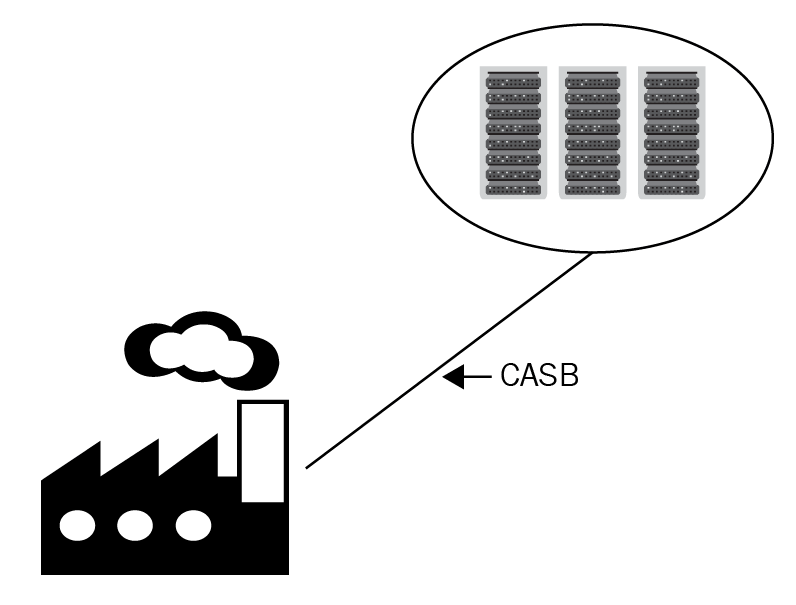
Figure 4: Hybrid cloud
In the bottom left-hand corner, we have a brick factory. This is known as on-premises, where the company owns a brick-and-mortar building. In the top left are servers in the cloud. The cloud access security broker (CASB) enforces the company's policies between the on-premises situation and the cloud.
There are different types of cloud services, and these are very heavily tested in the Security+ exam, therefore we will show screenshots of the types of offerings. We will first look at infrastructure as a service which is the model that you may have more control over:
Infrastructure as a service (IaaS): If you think of a network infrastructure, you think of desktops, servers, firewalls, routers, and switches—the hardware devices for a network. When you purchase these devices, they have a default factory setting and these settings need to be configured. Desktops are bare-bones, meaning that they have no operating system installed. IaaS is the same; you need to preconfigure these devices, install an operating system, and maintain the patch management. See the pricing for IaaS in the illustration that follows.
Distributive allocation: When you decide to use an IaaS model, you may install a virtual load balancer to provide a distributive allocation of some of your server capacity. As we know from previous chapters, a load balancer will allocate the load across multiple servers to ensure that no single server is overburdened:
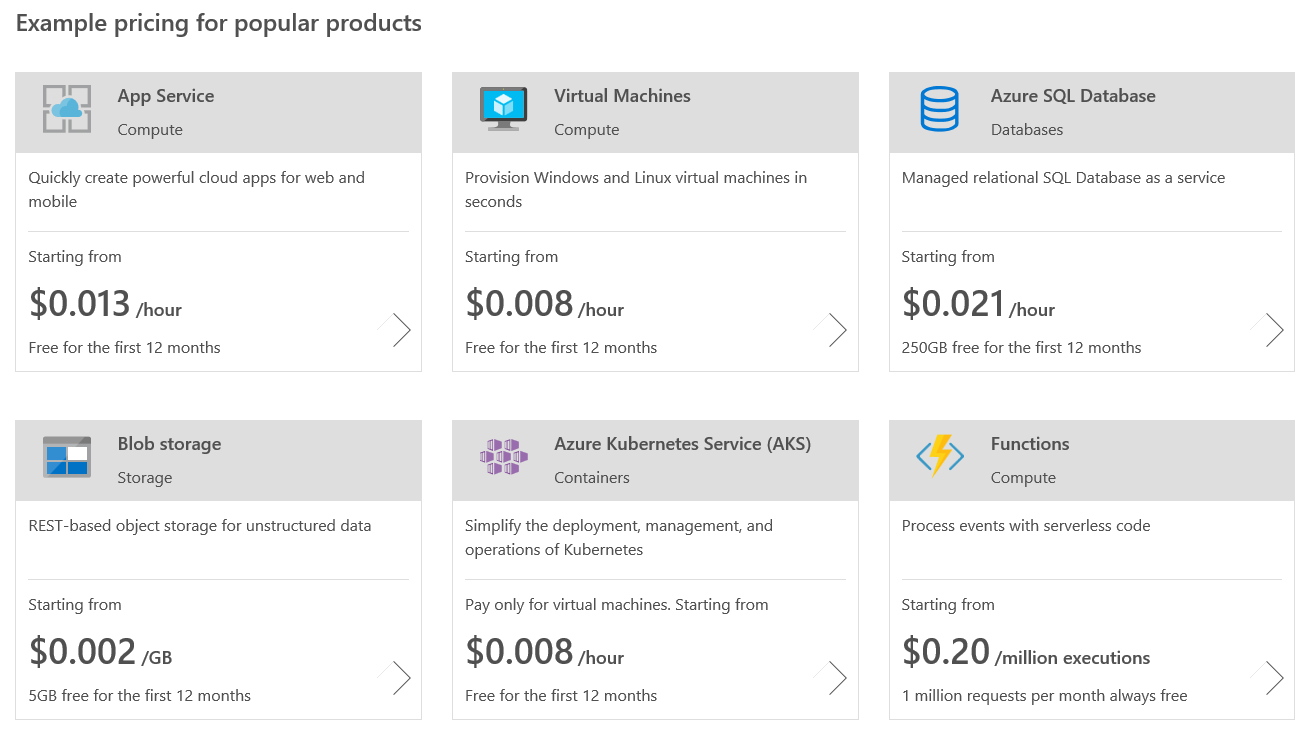
Figure 5: Microsoft's IaaS offering (July 2018)
Exam tip:
IaaS is where you will install the operating system and patch it. This is the model you have more control over.
Software as a service (SaaS): This is where the CSP hosts a bespoke software application that is accessed through a web server. Let's look at three examples of this—Goldmine, Salesforce, and Office 365.
Goldmine: Goldmine is an SaaS package, that is, a customer relationship management (CRM) package, that is used by companies that sell products and services. It will host lists of their customers, with contact numbers and addresses:
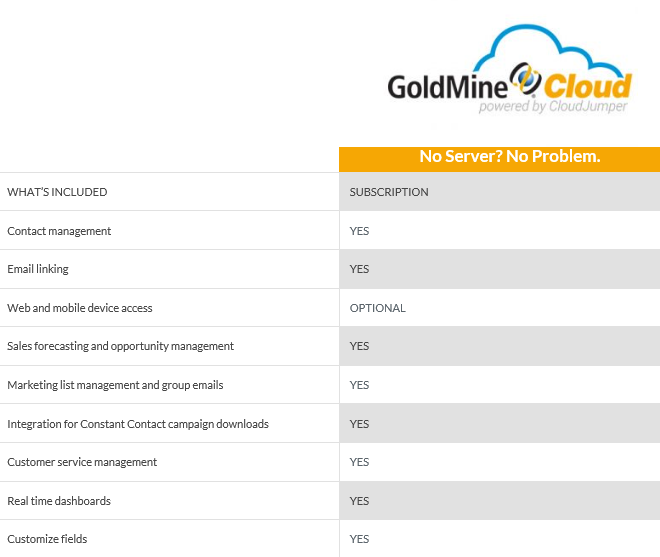
Figure 6: Goldmine—SaaS
Salesforce: Salesforce is an internationally used software package employed by sales teams to show a sales forecast over a period of time. It will allow salespeople to enter potential sales leads, categorize them, and hold any correspondence between the parties:
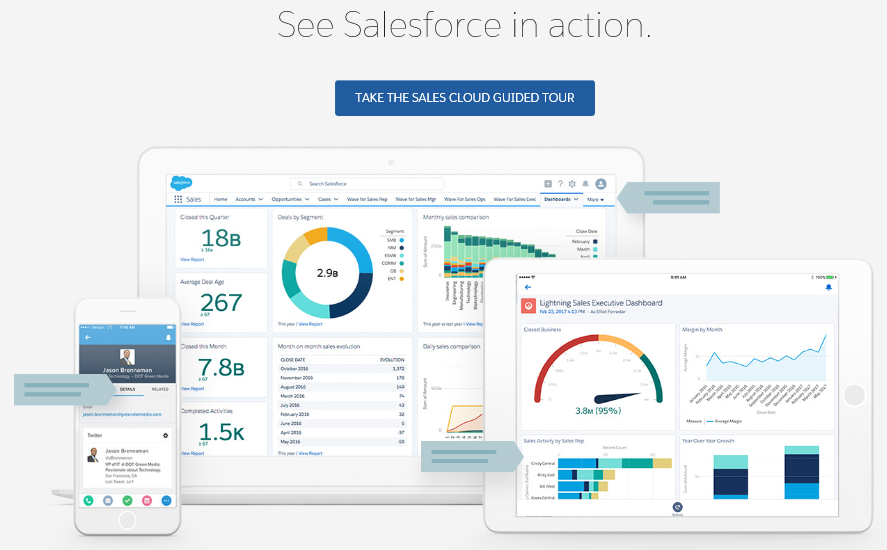
Figure 7: Salesforce—SaaS
Office 365: Office 365 is a Microsoft product where the packages range from email to various Office applications that are all hosted in the cloud. Each user has a 1 TB storage space. The premium package comes with Skype, exchange for email, and SharePoint, which is a document management system:
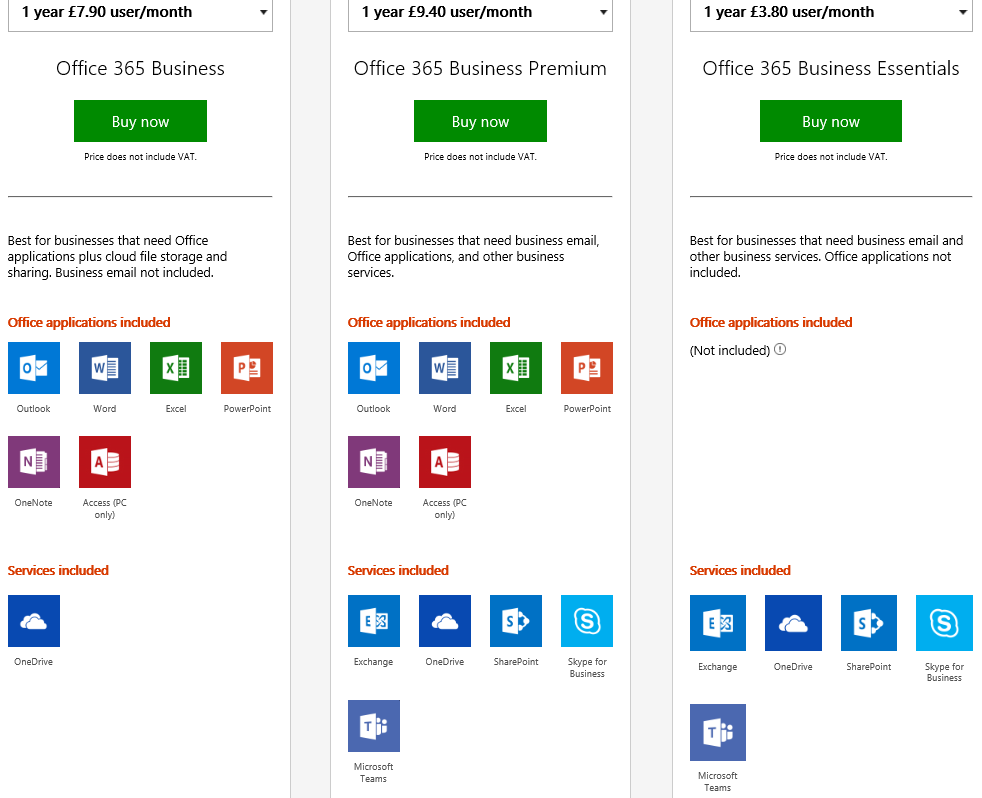
Figure 8: Microsoft Office 365—SaaS
Platform as a service (PaaS): This provides the environment for developers to create applications; an example of this is Microsoft Azure. The platform provides a set of services to support the easy development and operation of applications, rolling them out to iOS, Android devices, as well as Windows devices.
Security as a service (SECaaS): This is where companies sign up to the cloud, but require security and they come to a CSP to provide security services to them. An example of this is Okta, which focuses on the identity and access management (IAM) that allows people to have secure access to applications from anywhere at any time:
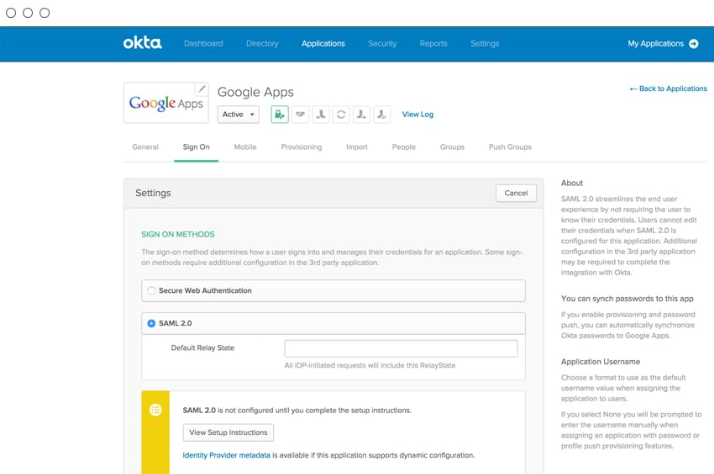
Figure 9: Okta security as a service (SECaaS) for Google Apps
The preceding diagram shows Okta providing secure web authentication into Google Apps.
We are going to look at different disk setups—some of which can provide fault tolerance or redundancy, meaning that if a disk fails, then the data is still available. RAID 0 is used for faster disk access, but provides neither fault tolerance nor redundancy. Let's first look at the different RAID setups, as these will be heavily tested.
There is a need for the disk setup on servers to provide redundancy; this is where if one disk fails, the data is still available. We have already looked at failover clustering in Chapter 5, Understanding Network Components, where two servers share a quorum disk—the single point of failure in that scenario would be the shared disk. We are going to look at different Redundant Array of Independent Disks (RAID) levels and their characteristics:
RAID 0: RAID 0 uses a minimum of two disks with a maximum of 32 disks:
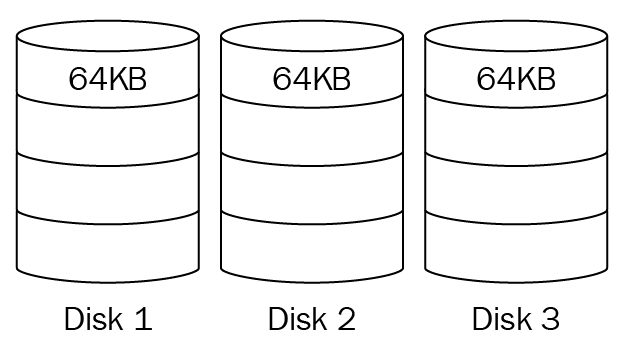
Figure 10: RAID 0
This is known as a stripe set, as the data is written across Disks 1-3 in 64 KB stripes. Should one disk fail, then all of the data will be lost, so RAID 0 does not provide fault tolerance or redundancy. The benefit of RAID 0 is its faster read access, so it may be used for the proxy server's cache.
RAID 1: RAID 1 is two disks, known as a mirror set:
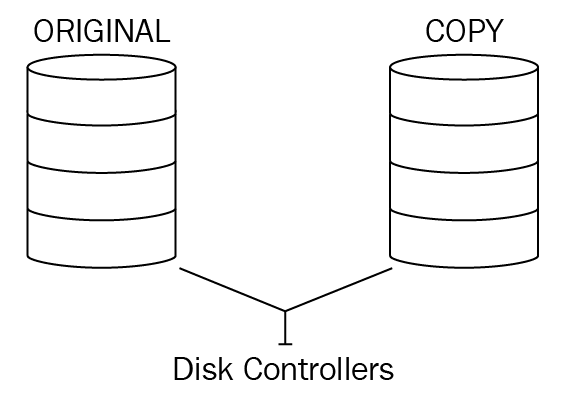
Figure 11: RAID 1
You can see from the preceding mirror set that the disk on the left has the original data and the disk on the right is a copy of that data. Should Disk 1 fail, you would "break the mirror" and then Disk 2 would provide the copy of the data for those who need access to it. At a later stage, we will add another disk and then reestablish the mirror set.
RAID 5: RAID 5 has a minimum of three disks and is known as a stripe set with parity; it is written across the disks in 64 KB stripes just like RAID 0, but one of the disks when each stripe is written has a parity block, so the parity is shaded:
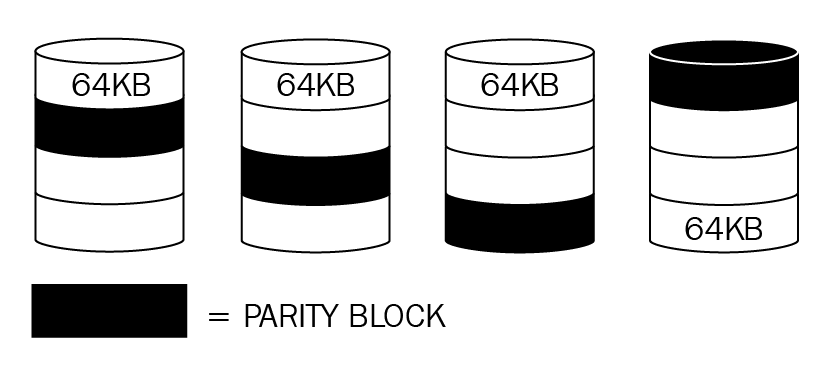
Figure 12: RAID 5
RAID 5 can suffer a single-disk failure but still allow access to the data, as the parity bits can recreate the missing data, but access will be slower than normal. This will give the IT team time to replace the missing disk.
Example: The preceding diagram represents a RAID 5 set, but we are using a mathematical equation to represent the disk set so that you can see the impact of losing one disk and then losing two disks:
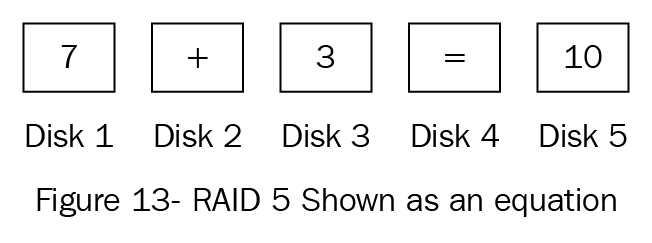
Figure 13: RAID 5 as a mathematical equation
Each of the disks has a numerical value. For example, if Disk 3 fails, the equation would be (7 +? = 10) and the answer would be 3. If we lose a second disk, Disk 1, the equation would then be (? + ? = 10) and you could not work it out; the same happens if you lose two disks—parity cannot recreate the missing data.
RAID 6: RAID 6 has a minimum of four disks and the same configuration as RAID 5, but it has an additional disk that holds another copy of the parity:
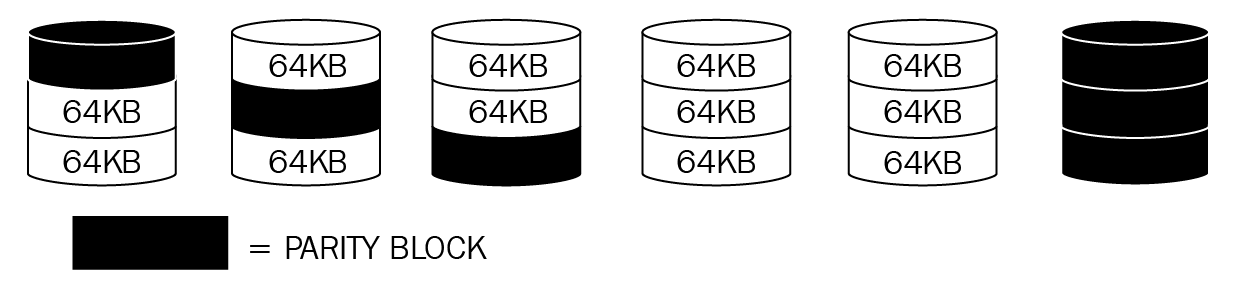
Figure 14: RAID 6
A RAID 5 disk set can afford to lose one disk but still be available. The good thing about a RAID 6 set is that it can lose two disks and still be redundant as it has double parity.
RAID 10: RAID 10 is also known as RAID 1+0—it is a RAID configuration that combines disk mirroring and disk striping to protect data. It requires a minimum of four disks, and stripes data across mirrored pairs. As long as one disk in each mirrored pair is functional, data can be retrieved:
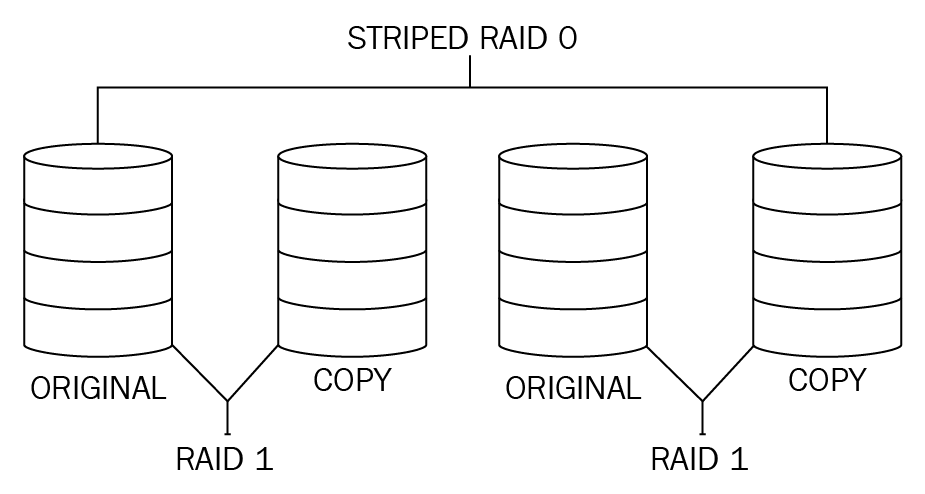
Figure 15: RAID 10
From this diagram, you can see a RAID 1 on the left and then it is striped, so this will allow you to lose two disks.
A storage area network (SAN) is a hardware device that contains a large number of fast disks, such as solid-state drives (SSDs), and is isolated from the LAN as it has its own network. A SAN typically has host bus adapters (HBAs) (https://searchstorage.techtarget.com/definition/host-bus-adapter) and switches (https://searchnetworking.techtarget.com/definition/switch) attached to storage arrays and servers. The disks are set up with some form of redundancy, such as RAID 5 and upward, so that the storage space is redundant:
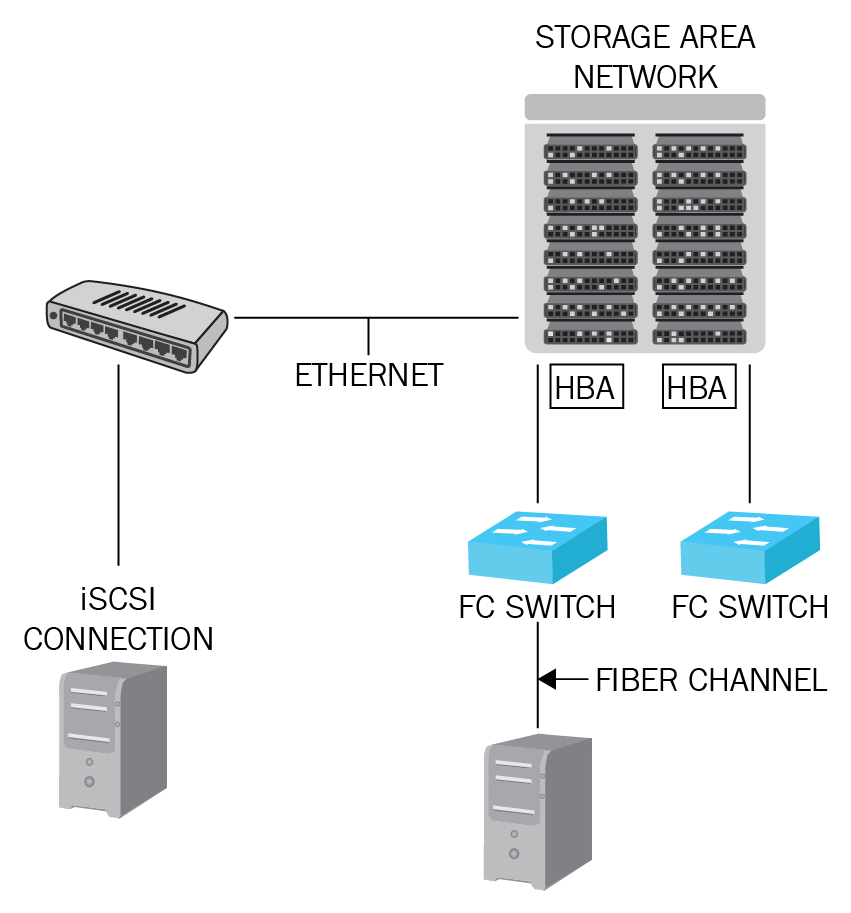
Figure 16: Storage area network
Each switch and storage system on the SAN must be interconnected, and the physical interconnections must support bandwidth levels that can adequately handle peak data activities. There are two connection types:
Fiber channel: Fast but expensive as it needs fiber channel switches
iSCSI connector: Runs Small Computer System Interface (SCSI) commands over Ethernet, and can connect through normal Ethernet switches and still offer good speed
The servers that use SAN storage are diskless, but use the SAN storage as if they had disks installed, but you need very fast connection speeds so that the server does not suffer performance issues. Example Server 1 is a virtual host and it needs another 200 TB of data to host more virtual machines. It connects to the SAN using Ethernet and Ethernet switches, this connector is known as an iSCSI connector:
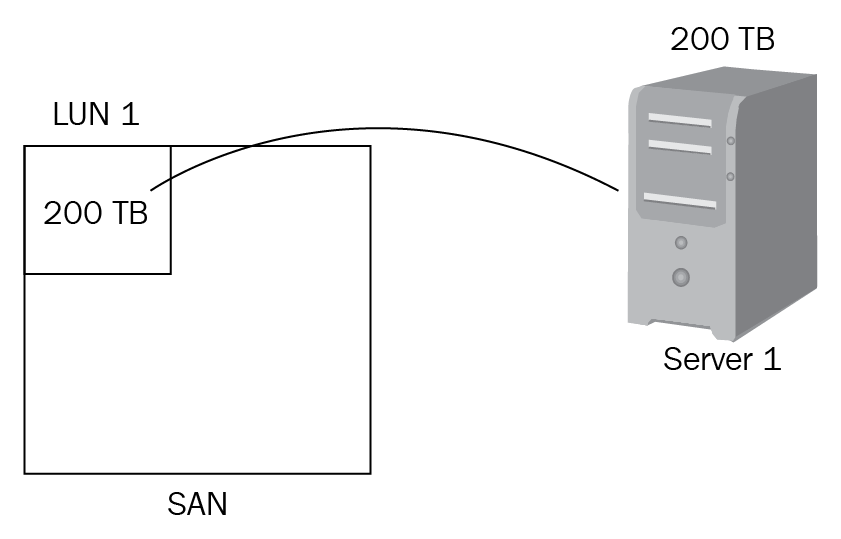
Figure 17: SAN—iSCSI Connector
The SAN allocates 200 TB by giving it a logical unit number (LUN). This is known as an iSCSI target. Server 1, which has been allocated the space, is known as the iSCSI initiator. Server 1 is diskless but still sets up the disk space using disk management as if it were a physical disk. To prevent latency, the connection between Server 1 and the SAN must be fast.
It is quite common to use cloud storage to hold your data from the iCloud provided by Apple, Google Drive provided by Google, OneDrive provided by Microsoft, or Dropbox provided by Dropbox, Inc. The consumer versions of cloud storage allow you to have limited storage space, but offer to sell you a business version or additional storage by charging a monthly subscription fee. Let's look at the following image:
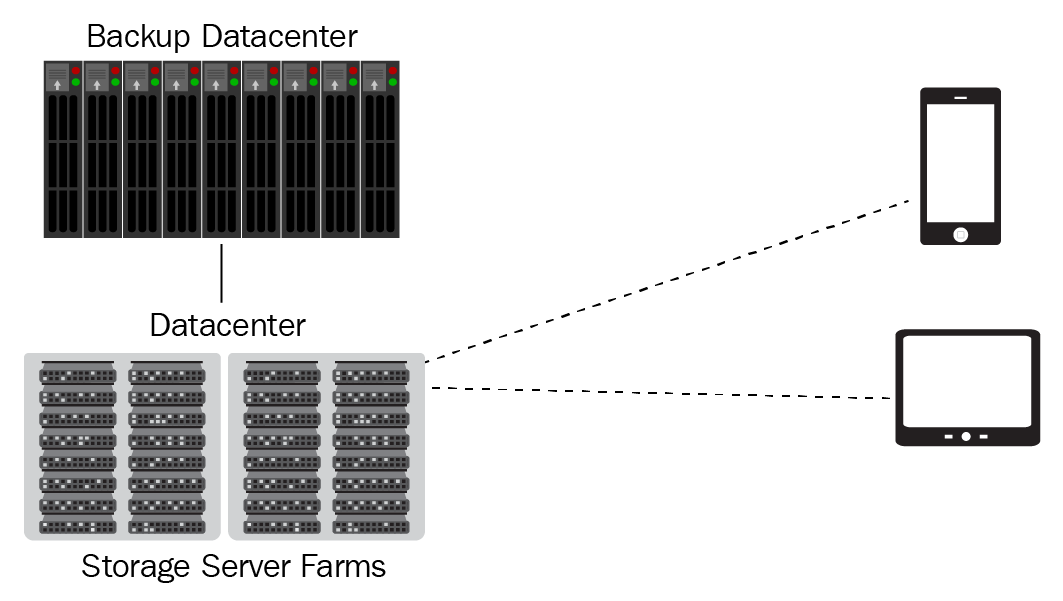
Figure 18: Cloud storage
In this diagram, you can see on the left-hand side a datacenter that has a vast amount of storage servers in a configuration called a server farm. The datacenter is a secure location where your data resides, but the data must stay within your world region. The datacenter has a backup datacenter to provide redundancy. The storage on these servers is likely to be diskless SAN storage.
A virtual network is very similar to a physical network in many ways, but for the Security+ exam, we must know the concepts of virtualization. To be able to host a virtual environment, we must install a hypervisor on a computer hosting the virtual machines. There are two different types of hypervisor:
Type 1 hypervisor: This is a enterprise version that can be installed on a computer without an operating system, called bare metal. Examples are VMWare ESX, Microsoft's Hyper V, or Zen used by Amazon Web Services (AWS).
Type 2 hypervisor: This needs an operating system, such as Server 2016 or Windows 10, and then the hypervisor is installed like an application. An example of a Type 2 hypervisor is Oracle's VM VirtualBox or Microsoft's virtual machine.
Exam tip: Type 1 hypervisor can be installed on a bare metal machine—examples are VMWare, Hyper V, and ESX.
The main server in a virtual environment is called a host and the virtual machines are called guests. This is very similar to a party where the person holding the party is a host and the people attending the party are called guests. There are various different components to virtualization:
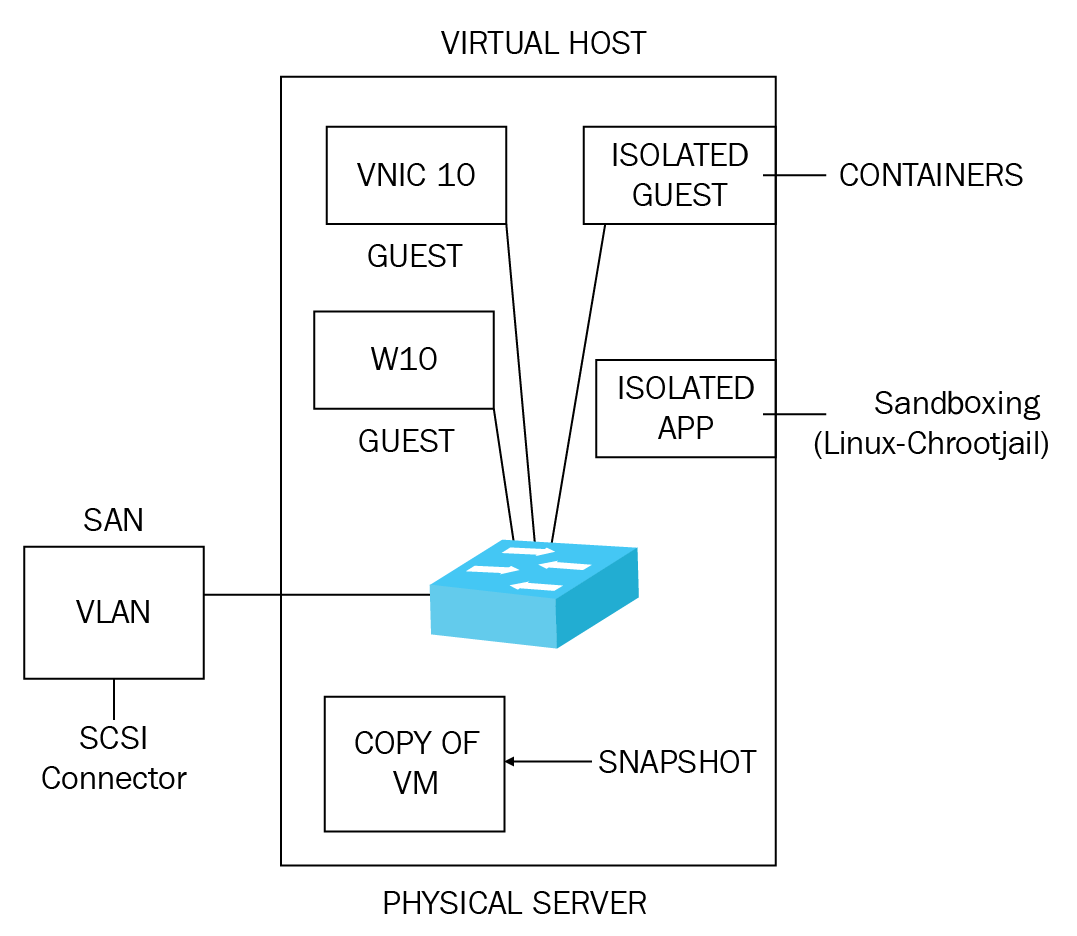
Figure 19: Virtualization
Now, we will look at each of the components:
Host: The host may hold 100 virtual machines and therefore the main resources that the host needs are storage that normally uses a SAN, memory, and processor cores. These can be increased through time and so the host is scalable (it can grow).
Example: Server 1 is a virtual host, already has 50 guest machines, and is running out of physical disk space, but there is a requirement for Server 1 to host another 20 guest machines. There is enough memory and there are enough processing cores, but there is a lack of disk space. The solution would be to create a LUN on the SAN, giving Server 1 another 10 TB of disk space that it can allocate to the new virtual machines. Server 1 then connects to the SAN and configures the disk space allocated in disk management.
Guest: Windows 10 is an example of a guest machine and needs the same amount of resources for a virtual machine as a physical Windows 10 machine. An isolated guest machine is known as a container. The following screenshot shows a virtual host with two guest machines, Server 2016 and Windows 10:
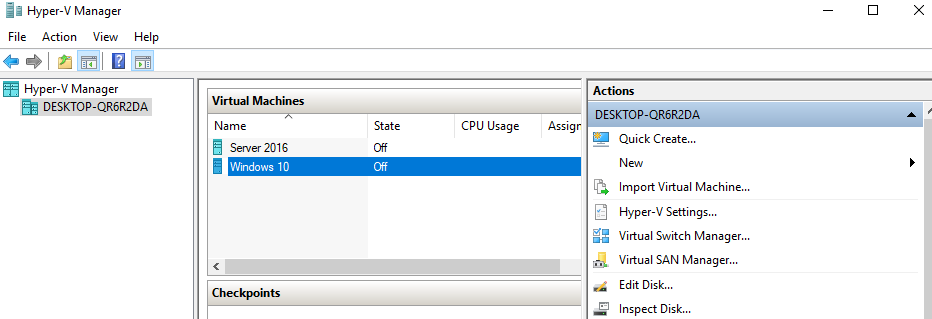
Figure 20: Virtual host with two guest machines
Containers: Isolated guest virtual machines are called containers.
Virtual switch: Although a virtual switch can act like a switch connecting all of the machines, it can also create three different types of network: internet, external, and private. For each external network, the host needs a physical network card. Therefore, if you have two external networks, the host needs a minimum of two physical network cards. An internal network can create VLANs within this network:
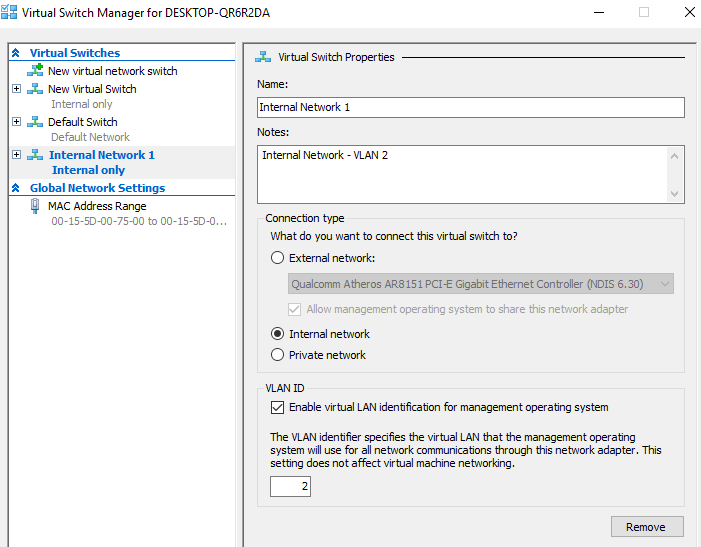
Figure 21: Virtual switch—Internal Network 1 with VLAN 2
Sandboxing: Sandboxing is where an application is placed in its own virtual machine for patching and testing, or if it is a dangerous application that you don't want roaming across your network. In a Linux environment, this is known as a chroot jail.
Snapshot: This is like taking a picture with a camera, whatever the virtual machine's setting is at that time is what you capture. You might take a snapshot before you carry out a major upgrade of a virtual machine so that if anything goes wrong, you can roll the machine setting back to the original. If you have spent an hour upgrading and patching a virtual machine, you may snapshot it afterward to save the settings. Please see a snapshot for Server 2016; Microsoft calls it a snapshot in Server 2008 but a checkpoint from Server 2012 R2 onwards, but it is basically a snapshot:
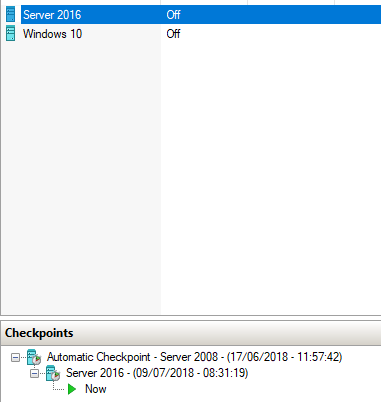
Figure 22: Snapshot of Server 2016
VLAN on a SAN: When we create VLANs, we create these on switches in a physical environment. But, in the virtual environment, when the virtual switch is created on a SAN, the VLAN is said to be created on a SAN. A VLAN on a SAN uses an iSCSI connector.
Exam tip:
When we create a VLAN on a SAN, we will always use an iSCSI connector.
A virtual desktop infrastructure (VDI) is a pool of virtual desktop pools for groups of users who share the same needs, such as a sales team whose members need access to the same applications and utilities on their desktops.
When the salespeople access their desktops, their settings are copied elsewhere; if the desktop becomes corrupt, another desktop from the pool is taken and the settings are then placed on the new desktop.
Example: A company has 50 users, who access their desktops remotely, as they are hosted in a virtual environment. There are another 100 virtual. There are 100 virtual machines all set up and waiting to be allocated to users. When a user uses their virtual machine, all of their desktop settings are copied onto another disk. If the virtual machine that they are using fails, then a new virtual machine is taken from the pool and their settings are then applied so that their desktop is recovered in the span of a few minutes.
When users use a virtual machine as their desktop, they can be set up in two ways: permanent or nonpermanent:
Example 1: A college has desktops for students set up in a virtual environment. During the day, the teacher has four different groups all carrying out the same activity, however, each group needs a pristine desktop. Therefore, it is set up as nonpermanent so when the user logs off, the image reverts back to the original setting.
Example 2: Employees in a corporate environment are using virtual machines as their desktops. User A has just spent 10 hours working on a project, therefore when they log in on the next day, they need to get the same desktop or productivity would be lost. Their desktop is therefore set up as permanent.
The servers for both cloud and virtualization, the storage servers and virtual hosts, are located in server farms that are in data centers. If these servers get too hot, the devices will fail. Therefore, in a data center, we have hot and cold aisles:
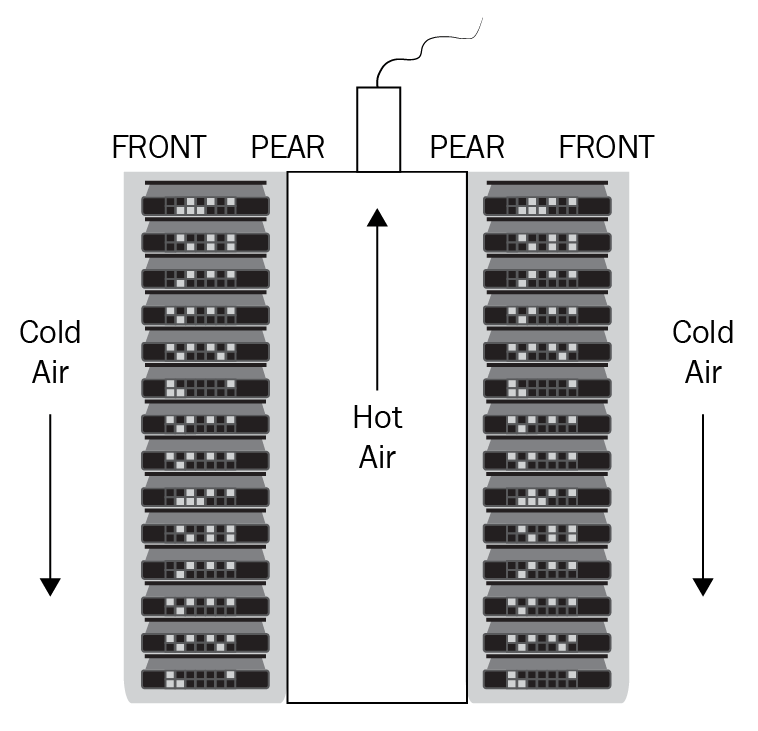
Figure 23: HVAC
The cold aisle is where the cold air comes in and that faces the front of the servers. The rear of the servers face each other, they push out hot air into the hot aisles, and this is allowed to escape through a chimney. This way, the temperature can be regulated and this ensures the availability of the IT systems.
Let's look at some of the network environments.
On-premises is where your company's network is inside a physical building; you will then have physical firewalls, routers and switches. Each person will have a physical machine, the software is normally held on disks and, the IT team is on-site. You have total control and responsibility over your resources.
Hosted services are technology services offered to you or your company by a provider that hosts the physical servers running that service somewhere else. Access to the service is usually provided through a direct network connection that may or may not run via the internet. The hosted services provider has full responsibility over your resources, including backup.
Cloud-hosting services provide hosting on virtual servers, which pull their computing resources from high-end servers that obtain their storage from a SAN. Access to resources is either via a lease line or the internet. The cloud provider has full responsibility over the hardware and availability of the IT systems:
Example 1: A company that makes Easter eggs has its own on-premises where they manufacture the eggs, and delivery trucks to take them to their suppliers. They may need to take on additional staff around Easter, so they then have a small public cloud for the busy period—this is known as a hybrid model.
Example 2: A new company cannot afford its own IT administrators as the turnover is limited, so they decide to subscribe to Microsoft's Office 365 for all of their needs. They adopt a cloud model and get email, Skype, and all of their Office 2016 applications. This is more cost-effective for them.
In this exercise, you are going to go to Amazon Web Services, which provides a calculator to see how much you could save by moving your infrastructure into the cloud. The instructions are accurate at the time of printing, but you may need to use them as a guideline if Amazon changes its website.
Search Google for: Amazon Web Services, pricing. Or go to Amazon Web Services and press the Pricing tab. Perform the following steps:
Select Pricing:
AWS Pricing: Calculate My Cloud Savings
Currency: Euro
Environment: Compare against on-premises
AWS Region: EU (Ireland)
Server Type: db (This means database)
App Name: SQL
Number of VNs: 10
CPU Cores: 4
Memory: 64 GB
Hypervisor: VMWare
DB Engine SQL Server Enterprise
Storage: SAN
Raw Capacity: 100 TB
Press Calculate TCO
How much did you save? Was it cost-effective?
Now, search for another cloud provider and use their calculator to see who is more cost-effective.
In a cloud environment, what is elasticity?
In which cloud environment would I install the software and then have to update the patches?
Which cloud model is Office 365?
What is the major benefit of using a public cloud?
What is a cloud single-tenant model?
What is a cloud multitenant model?
Describe how a community cloud operates.
What are the limitations imposed on a CSP regarding data storage?
Who is responsible for the disaster recovery of hardware in a cloud environment?
What is a cloud access security broker (CASB)?
What model is it if you own the premises and all of the IT infrastructure resides there?
What is a hybrid cloud model?
What is distributive allocation?
What type of model deals with identity management?
What RAID model has a minimum of three disks? How many disks can it afford to lose?
What are the two RAID models that have a minimum of four disks?
What is the difference between RAID 5 and RAID 6?
Where will a diskless virtual host access its storage?
If you have a virtual switch that resides on a SAN, what connector will you use for a VLAN?
What type of disks does a SAN use?
Name a Type 1 hypervisor.
What type of hypervisor can be installed on bare-metal machines?
What is the machine that holds a number of virtual machines called?
What is a guest and what is it called if you isolate it?
In a virtual environment, what is sandboxing and how does it relate to chroot jail?
Which is faster for data recovery: a snapshot or a backup tape?
Why does HVAC produce availability for a datacenter?
Which cloud model is it if you decide to use Salesforce?
What do you call the cloud model where people from the same industry share resources and the cost of the cloud model?
What is an example of cloud storage for a personal user?
Elasticity allows you to increase and decrease cloud resources as you need them.
Infrastructure as a service (IaaS) requires you to install the operating systems and patch the machines. The CSP provides bare-metal computers.
Office 365 is a software as a service (SaaS) that provides email, Skype, and Office applications.
The major benefit of a public cloud is that there is no capital expenditure.
A private cloud is a single-tenant setup where you own the hardware.
Public cloud is multitenant.
A community cloud is where people from the same industry, such as a group of lawyers, design and share the cost of a bespoke application and its hosting, making it cost-effective.
A CSP must store the data within regions. It cannot even more backup data to another region for resiliency.
The CSP is responsible for the hardware fails.
The CASB ensures that the policies between the on-premises and the cloud are enforced.
On-premises is where you own the building and work solely from there.
A hybrid cloud is where a company is using a mixture of on-premises and cloud.
Distributive allocation is where the load is spread evenly across a number of resources, ensuring no one resource is overutilized. An example of this is using a load balancer.
Security as a service (SECaaS) provides secure identity management.
RAID 5 has a minimum of three disks and you can afford to lose one disk without losing data.
RAID 6 and RAID 10 both have a minimum of four disks.
RAID 5 has single parity and can lose one disk, where RAID 6 has double parity and can lose two disks.
A diskless virtual host will get its disk space from a SAN.
A VLAN on a SAN will use an iSCSI connector.
A SAN will use fast disks, such as SSDs.
Hyper V, VMware, and Zen are all Type 1 hypervisors.
Type 1 hypervisors can be installed on bare-metal machines.
A host holds a number of virtual machines—it needs fast disks, memory, and CPU cores.
A guest is a virtual machine, for example a Windows 10 virtual machine, and if it is isolated it is called containers.
Sandboxing is where you isolate an application for patching, testing, or because it is dangerous. A chroot jail is for sandboxing in a Linux environment.
A snapshot is faster at recovering than any other backup solution.
HVAC keeps the servers cool by importing cold air and exporting hot air. If a server's CPU overheats, it will cause the server to crash.
Salesforce is an online sales package, this is software as a service (SaaS).
A community cloud is where people from the same industry share resources.
Cloud storage for personal users could be iCloud, Google Drive, Microsoft Onedrive, or Dropbox.