A security information and event-management (SIEM) system automates the collection of log files from multiple hosts, servers, and network devices, such as firewalls, in real time to identify potential risks to the network. The types of functionality from a SIEM system are:
Aggregation: The SIEM system can move log files and data from multiple sources to a common repository.
Event correlation: A SIEM system uses a correlation engine to correlate events from multiple systems. For example, if someone tried to log in to three separate devices, the SIEM server will notify the security administrator of a potential attack. When the same event is duplicated and is logged by different devices, the SIEM system will use event de-duplication to ensure that the event is logged only once.
WORM drive backup: The logs from a SIEM system can be vital to the security team, therefore they can be backed up onto a WORM drive, write-once, read-many. This allows log files to be backed up onto the WORM drive, but prevents the alteration or deletion of events.
Automated alerting and triggers: A SIEM system could install agents on several devices so that the SIEM system is alerted when several events occur.
Time synchronization: A SIEM server relies on time synchronization from a Stratum Zero or the Atomic Clock time source so that time can be synchronized and events can be put into chronological order.
A Mail Gateway is a device that sits in a DMZ to scan incoming and outgoing email for viruses. It can also act as a spam filter, preventing spam emails from reaching the internal mail server.
Due to email being a critical function for businesses, more and more companies are moving away from in-house, server-based solutions, and are using Microsoft Office 365 or Google G Suite. The benefits of cloud-based email are that the cloud provider is responsible for scanning the incoming email as well as providing the hardware to run the mail servers.
A Media Gateway is a translation device or service that converts media streams between disparate telecommunications technologies. An example of this is Karaka, which is an XMPP Gateway that allows communication between Jabber and Skype.
A Hardware Security Module (HSM) is a physical device that stores the X509 certificates used on a network. These modules traditionally come in the form of a plug-in card or an external device that attaches directly to a computer or network server.
Traditional networks route packets via a hardware router and are decentralized; however, in today's networks more and more people are using virtualization, including cloud providers. A software-defined network (SDN) is where packets are routed through a controller rather than traditional routers, which improves performance.
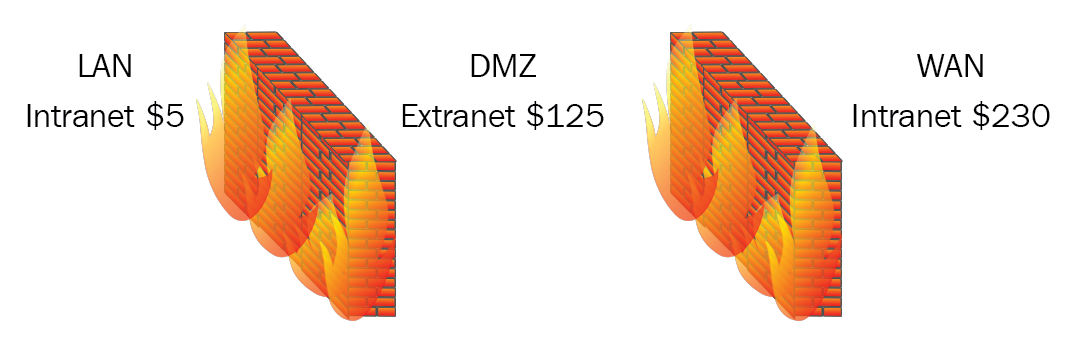
Securing networks and protecting them is vital to protect a company's assets. We use different zones and topologies, network separation and segmentation, and install firewalls to prevent unauthorized access to the network. First of all, let's look at different zones and topologies. There are three main zones—LAN, WAN and DMZ:
Local area network (LAN): A secure network with very fast links and a web server, called the intranet, that holds internal-only information, such as classified data, manufacturing price lists, or the internal forms library.
Demilitarized zone (DMZ): A boundary layer between the LAN and the WAN that holds information that companies may want people from the internet to access. You may put your email server in the DMZ but never a domain controller. The web server inside the DMZ is called the extranet, which needs a username and password to access the site. It could be used for an area, which a distributor would gain information from.
Wide Area Network (WAN): Open to the public and not a safe place, as it is freely accessible, the web server inside the WAN is the internet. The internet is an example of a WAN, and any data traversing the internet needs to be encrypted. It covers a very large geographic area and the links tend to be slower than the LAN and DMZ.
Example:
An upscale store sells designer sneakers at $230, however, the shop's owner purchases them from the manufacturer by placing orders on the extranet server. Access to the extranet web server is via a unique username and password, and the price the shop purchases the sneakers at is $125, allowing for a profit of $105. On the intranet, web server is the manufacturing price of the sneakers, which are made in China, for a mere $5 a pair:

Figure 15: Zones
From this information, you should ask yourself three simple questions:
What would happen if the customer knew that the shop owner was making a profit of $105? They would definitely want a discount.
What would happen if the shop owner discovered the manufacturing price was $5? They would also like a discount.
What would happen if the customer found out that their designer sneakers were made for $5? They may decide not to purchase them as they are really cheap sneakers in disguise and, through social media, the manufacturer would lose market share.
You can see why data in a LAN needs to be secure and not freely available to the general public.
Network Address Translation is where a request from a private internal IP address is translated to an external public IP address, hiding the internal network from external attack. See Figure 16:
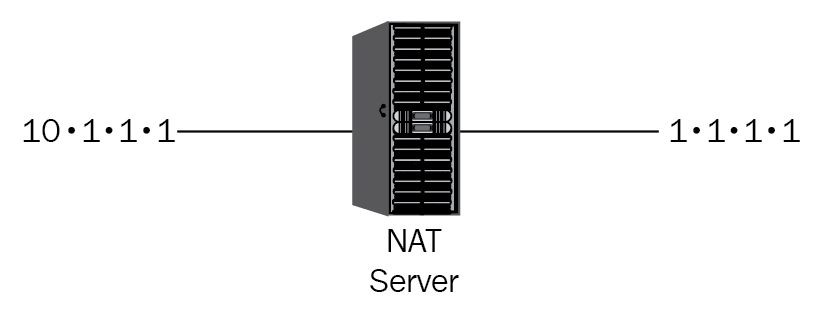
Figure 16: NAT
A NAT could be set up to hide a R&D network where new products are designed. Remember, a competitor may try to steal your new ideas and get them to market before you. A NAT could be set up on a firewall or a NAT server.
Port address translation (PAT) is where multiple internal requests are translated to an external IP address, see Figure 17:
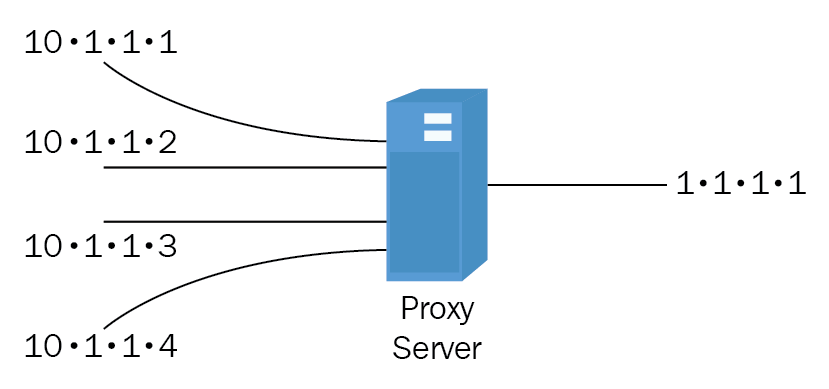
Figure 17: PAT
A proxy server could be used for PAT as it gets many internal requests that are translated to one external IP address.
If you have a Windows desktop or laptop and you go away on holiday for 2-3 weeks, when you come back your device may need multiple updates. After a remote client has authenticated NAC, it then checks that the device being used is fully patched. See Figure 18:
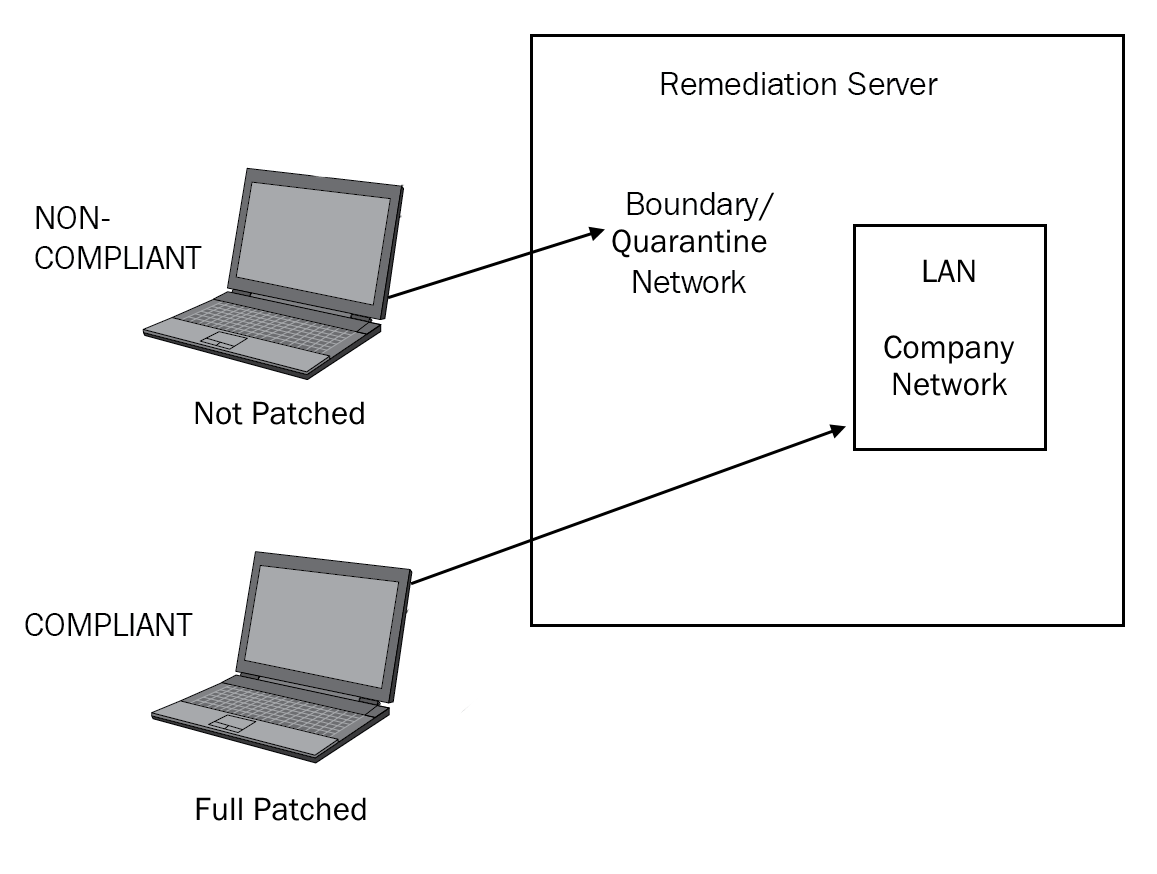
Figure 18: NAC
When the user is authenticated, the health authority (HAuth) checks against the registry of the client device to ensure that it is fully patched. A fully patched machine is deemed compliant and allowed access to the LAN. In the preceding diagram, Laptop 2 is compliant. If the device is not fully patched, it is deemed noncompliant and is redirected to a boundary network, which could also be known as a quarantine network. The components of NAC are:
Host health checks: The HAuth checks the health of the incoming device to ensure that it is fully patched.
Compliant/noncompliant device: A device that is fully patched is a compliant device, but a device that has missing patches is deemed noncompliant.
Agents: Each device has an agent installed so that the Health Authority can carry out health checks. The two types of agents are:
Permanent: The agent is installed on the host
Dissolvable: A dissolvable agent is known as temporary and agentless and is installed for a single use
Remediation server: Sits on the boundary or quarantine network. When the noncompliant machine is connected to the boundary network, it can obtain the missing updates from the remediation server. Once the device is fully patched, it is then allowed to access the LAN.
When security teams are trying to find out the attack methods that hackers are using, they set up a website similar to the legitimate website with lower security, known as a honeypot. When the attack commences, the security team monitors the attack methods so that they can prevent future attacks. Another reason a honeypot is set up is as a decoy so that the real web server is not attacked. A group of honeypots is called a honeynet.
Exam tip:
A honeypot can be used to examine the attack method that hackers use.
Secure Socket Layer (SSL) is used to encrypt data so that when it is in transit it cannot be stolen or altered. SSL encryption is a processor-intensive operation and most servers, such as database servers, are working very hard as it is. SSL acceleration refers to offloading the processor-intensive SSL encryption and decryption from a server to a device, such as a reverse proxy, to relieve the pressure from the server.
When traffic comes into your network from the internet and it is encrypted, the firewall, NIPS, NIDS, DLP, or any network device cannot examine the data. Therefore, after the traffic has passed through the external firewall, the SSL/TLS decryptor will decrypt the data before it passes through an inline NIPS. This then means that the NIPS can examine and prevent malicious traffic accessing the local area network.
A sensor/collector can be a device, tap, or firewall log whose purpose is to alert the NIDS of any changes in traffic patterns within the network. If you place your first sensor on the internet side of your network, it will scan all of the traffic from the internet.
A tap or a port mirror is set up on a port of a switch so that when the data arrives at that port, a copy is stored on another device for later investigation or it is sent to a sensor who will investigate the traffic and, if needs be, inform the NIDS of changes in traffic patterns.
A Distributed Denial of Service (DDoS) attack is where a very large amount of traffic is sent to a switch or a server so that it is overwhelmed and cannot function. A DDoS mitigator is a device, such as a stateful firewall on the external interface of your DMZ or a flood guard on an internal switch, that can identify the DDoS attack at an early stage and prevent it from being successful.
Exam tip:
Capturing the data flowing through a port on a switch can be done by port mirroring, also known as a tap.
Cyber crime is rife and is the largest growing criminal industry. In today's word, most businesses are interconnected and use the internet. Maintaining the security and integrity of data, including research and development, is paramount. We need to be able to isolate, segment, and segregate our network, both physically and virtually. Let's look at the options we may have:
Physical segmentation/separation: If we have data, such as email or a web server, that we want people to be able to access from the internet, whether it be a customer or one of our salespeople, we will physically separate it from our LAN by placing it in the DMZ, which is a boundary layer, so that users accessing this data do not need to come into our secure LAN. You would never place a domain controller or a database server in the DMZ.
Air gaps: Another physical method is to create air gaps between some systems that we use internally to separate confidential systems from normal systems.
Example 1: The US department of defense has two distinct networks: the Secret Internet Protocol Router Network (SIPRNet), where classified data such as top secret or secret documentation are accessed, and the Non-classified Internet Protocol (IP) Router Network (NIPRNet) where unclassified data is held. These two private networks have air gaps between them so that a desktop from the NIPRNet cannot access the SIPRNet, or vice versa.
Example 2: In a finance department, there is one computer that would be used to make electronic payments, such as BACS or CHAPS transfers, and this machine would be not be accessible by everyone in that finance department, therefore it would be isolated from the other departmental machines—this is also an example of an air gap.
Logical separation—VLAN: There is sometimes a need to create a separate logical network within the LAN to segment a department from the rest of the internal network. The device that connects all of the internal computers is called a switch, but within a switch we have the ability to create a Virtual Local Area Network (VLAN). If you look at Figure 19, you can see a switch with two separate VLANs:
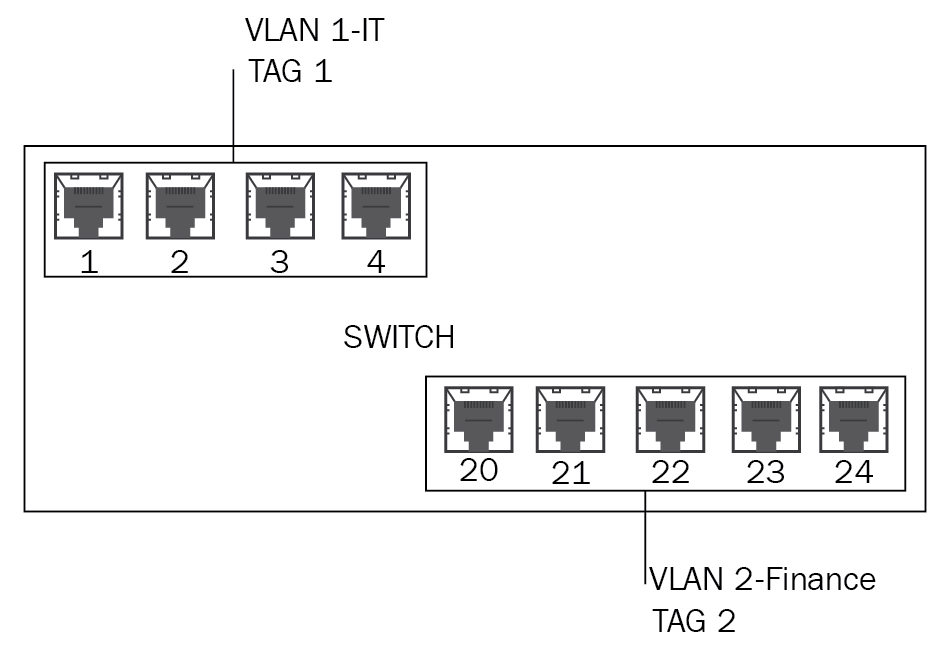
Figure 19: Two VLANS in a switch
A VLAN is created by using the software on the switch where you can bond a number of ports to work together as a separate logical network. If you look at Figure 19, you can see that port numbers 1-4 have been used to create a VLAN for the IT department, and then ports 20-24 have been used to create another VLAN for the finance department. Although both of these departments are on an internal device, creating the VLANs isolates them from other VLANs and the company's network. An important factor is that a VLAN tag is set up so that when traffic arrives at the switch, it knows where to send it.
Virtualization: If we create a virtual network, we can isolate the users on that network from other users on the same virtual network using VLANs. On a virtual host, I can create many different isolated virtual networks. Virtualization is covered in Chapter 6, Understanding Cloud Models and Virtualization.
It is important for a security or network administrator to understand the functionality that each device provides and where best to place them to ensure that your network is safe. Figure 20 shows the placement of each device:
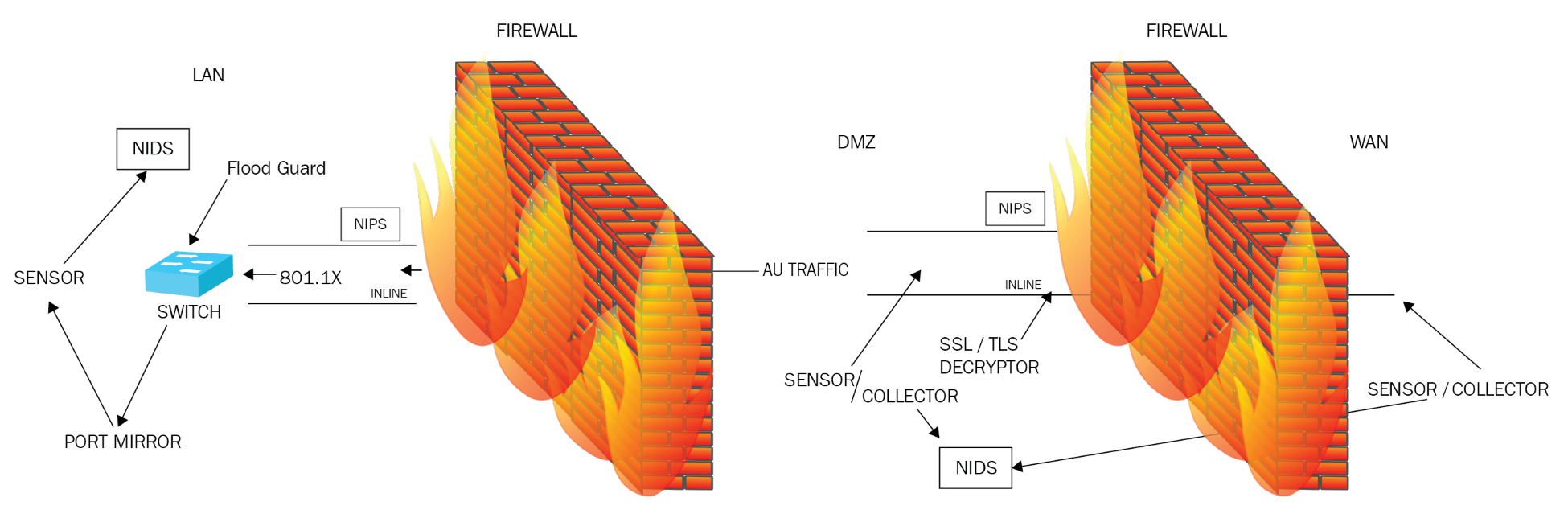
Figure 20: Security device placement
If we look at Figure 20, the first thing you will notice is that the three network zones that have been established are the LAN, DMZ, and WAN. These networks are divided by two firewalls that are in a back-to-back configuration so that if traffic manages to get through the first firewall, we hope that the next firewall stops it. As resources, such as our website, are in the DMZ, the external firewall may have one or two ports open that the internal firewall between the DMZ and LAN does not.
Between the WAN and DMZ there is a network firewall. The purpose of this firewall is to prevent unauthorized access to the network. Directly behind the external firewall is an SSL/TLS decryptor that decrypts the traffic coming in so that other security devices can examine it.
The next stage is that the decrypted traffic is placed through an inline NIPS. As it is inline, all traffic must pass through it. The purpose of the NIPS is as an additional layer of security and should be placed close to the external firewall.
Behind the NIPS is the NIDS in passive mode, where traffic does not travel through it but it is scanning the network for changes in traffic patterns. The NIPS in the DMZ scans the network and also has sensors/collection places in the DMZ to alert it to changes in traffic patterns.
The firewall dividing the DMZ and the LAN will be a stateful firewall that will prevent DDoS attacks and knows of the acceptable commands used by each application. Directly behind the firewall will be another inline NIPS examining the traffic as it comes into the LAN. Another NIDS and a set of sensors/collectors are placed in the LAN.
The internal switch connects all of the internal devices, and it will be a managed switch using 802.1x so that it authenticates all devices connecting to the network and stops unauthorized devices and rogue WAP from connecting the to the network. The switch will have a flood guard installed to prevent DDoS and MAC flooding attacks. The switch may have a port mirror installed on one of the ports so that a copy of the traffic, stored on backup device for later investigation, is sent to a sensor. Should the sensor identify anything abnormal, it will notify the NIDS in the LAN. A port mirror is also known as a tap.
Depending on the number of users that reside in your LAN, you may need several switches to be operating, and these switches need to move traffic between each other. Therefore, rather than having a daisy chain, which would take more time to move the traffic around, we install an aggregation switch. The aggregation switch connects multiple switches in a mode called link aggregation:
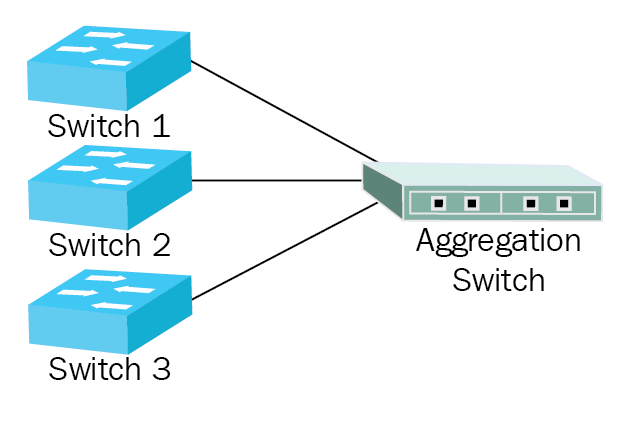
Figure 21: Aggregation switch
Link aggregation is a way of joining Ethernet links together so they act like a single, logical link. If you connect all of the switches together, you can balance the traffic among these links to improve performance. An important reason for using link aggregation is to provide fast and transparent recovery in case one of the individual links fails.
A protocol is the rules required by different applications for the exchange of data where the application can perform actions such as running commands on remote systems, sending and receiving email, or maybe downloading files from the internet. Each application has a special port number it uses for communication. If you think of ports as being TV channels, if we want to watch sport we go to the sports channels, if we want to watch news we go to the news channel. Applications are the same; if we want to send an email, we use a mail application, and they all have a distinct port number for communication.
There are two types of ports: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). The main difference between the two is that the TCP is connection-orientated as it uses a three-way handshake, and UDP is faster but less reliable as it is connectionless. See Figure 22 for the three-way handshake:
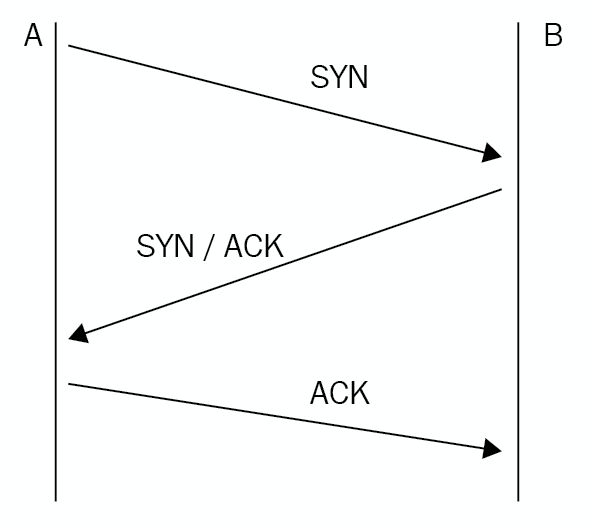
Figure 22: Three-way handshake
In a three-way handshake, the first packet that is sent is called a SYN packet, where the sending host informs the receiving host of the number of its next packet. The receiving host sends a SYN-ACK packet where it says what its next packet is. The Ack packet acknowledges both, and then the data is sent. The data is sent in chunks, and where it is received, an acknowledgement is sent that tells the sending host to send more packets. Once all of the data is sent, a three-way handshake confirms all of the data is intact and the session closes.
In a UDP session, the application is responsible for ensuring that everything is received, and because a three-way handshake is not used, the connection is faster but less reliable. You would use UDP for streaming video, where speed is paramount.
For the purpose of the Security+ examination, you will need to know when to choose the correct protocol and which port it uses. A list of common protocols is listed here with their uses afterwards.
As most protocols use TCP ports, I will only mention the UDP ports and therefore you can assume if it is not labelled UDP, it is TCP.
Exam tip: Knowing why we use each protocol is more important than knowing the port numbers. There will be a review at the end of the book testing port numbers.
|
Protocol |
UDP |
Port |
Use |
|
File Transfer Protocol (FTP) |
|
21 |
File transfer—passive FTP |
|
Secure Shell (SSH) |
|
22 |
Run remote command—securely |
|
Secure Copy Protocol (SCP) |
|
22 |
Secure copy to UNIX/LINUX |
|
Secure FTP (SFTP) |
|
22 |
Secure FTP download |
|
|
|
23 |
Run remote command—unsecure |
|
Simple Mail Transport Protocol (SMTP) |
|
25 |
Transport mail between Mail Servers |
|
Domain Name System (DNS) |
UDP |
53 53 53 |
Host name resolution Zone transfer Name queries |
|
Dynamic Host Configuration Protocol (DHCP) |
UDP |
67/68 |
Automatic IP address allocation |
|
Trivial File Transfer Protocol (TFTP) |
UDP |
69 |
File transfer using UDP |
|
Hypertext Transport Protocol (HTTP) |
|
80 |
Web browser |
|
Kerberos |
|
88 |
Microsoft authentication using tickets |
|
Post Office Protocol 3 |
|
110 |
Pull mail from mail server, no copy left on mail server |
|
NETBIOS |
UDP |
137-139 |
NETBIOS to IP address resolution |
|
Internet Message Access Protocol (IMAP 4) |
|
143 |
Pull mail from mail server |
|
Simple Network Management Protocol (SNMP) |
UDP |
161 |
Notifies the status and creates reports on network devices |
|
Simple Network Management Protocol Version 3 (SNMP v3) |
UDP |
162 |
Secure version of SNMP |
|
Lightweight Directory Access Protocol (LDAP) |
|
389 |
Stores X500 objects, searches for active directory information |
|
Lightweight Directory Access Protocol Secure (LDAPS) |
|
636 |
Secure LDAP where the session is encrypted |
|
Secure Internet Message Access Protocol (IMAP 4) |
|
993 |
Secure IMAP4 |
|
Secure Post Office Protocol 3 |
|
995 |
Secure POP3 |
|
File Transfer Protocol Secure (FTPS) |
|
989/990 |
Download of large files securely |
|
Remote Desktop Protocol (RDP) |
|
3389 |
Microsoft remote access |
|
Session Initiated Protocol (SIP) |
|
5060/5061 |
Connects internet based calls |
|
Secure Real Time Protocol (SRTP) |
|
5061 |
Secure voice traffic |
A Use Case is where everyone in a company tries to achieve a goal. An example would be if you called a company, their customer services take your order, their finance department processes the payment, production would make the product, and then dispatch would mail it to you. Another way of looking at use cases is that they are an example of how something is used. In the following examples, we will see use cases for different protocols.
Transferring files is a common function. When we purchase an e-book, it is immediately available to download onto our Kindle. There are four different protocols that we can use for file transfers:
File Transfer Protocol (FTP): If I wish to upload files to a web server, I would use FTP on port 20, but the more common use is to download files using port 21, which is known as Passive FTP. The downside of using FTP is that the transfer is in clear text, so a packet sniffer could view the information.
Secure FTP (SFTP): Allows me to download files securely so that they cannot be tampered with. It is secure as it is packages with SSH.
Trivial File Transfer Protocol (TFTP): The UDP version of a file transfer; it is faster than FTP as it does not use a three-way handshake, but it is not secure as the files are transferred in clear text. It is used when user authentication is not required.
File Transfer Protocol Secure (FTPS): FTPS is much faster than SFTP as it uses two ports, 989 and 990, and is used for downloading very large files securely.
Exam Tip:
SSH is a secure method of running a command on a router.
There are various ways of obtaining remote access, we are going to look at each in turn, and decide when we would choose to use them:
Telnet: A protocol that was first used in 1973 to run remote commands on devices, such as routers. Unfortunately the session is in clear text and therefore not secure. If you want to know whether port 25 is opening on a mail server called Mail1, you could run telnet Mail1 25. It is no longer used as it is unsecure but may be tested.
Secure Shell (SSH): Invented in 1991 to replace Telnet so that it could run commands securely, it is commonly used when you want to perform remote access onto routers.
Remote Desktop Protocol (RDP): A Microsoft product that allows you to run a secure remote access session on a Windows desktop or server. When you set up a remote access using RDP, the service obtaining the session needs to allow access for incoming remote sessions and then also place the users into the remote desktop users group. If these two actions are not taken, it will not work. As most routers are CISCO products, RDP cannot be used to remote into a router.
Remote Access Server (RAS): A legacy server that allows remote access via a modem and telephone line and therefore is very rarely used.
Virtual Private Network (VPN): Used to create a secure tunnel from home or a remote location into your work. The most common protocol is L2TP/IPSec, which is used in tunnel mode across the internet. If you have a legacy system pre-2000, you would use an SSL VPN that requires an SSL certificate.
There are different types of email, some are web-based and some use the MAPI client on the desktop, Let's look at each of them and understand when we would use them:
Simple Mail Transport Protocol (SMTP): Used to transfer files between different mail servers and is used for outbound emails.
Simple Mail Transfer Protocol Secure (SMTPS): Encrypts the mail being transferred between mail servers, making it very secure.
Post Office Protocol 3 (POP3): An email client that pulls email from the mail server, but when the email is downloaded it does not retain a copy on the mail server itself. It is not commonly used, but is tested in the Security+ exam. There is also a secure version of POP3.
Internet Message Access Protocol version 4 (IMAP4): A mail client that also pulls emails from the mail server, but he has more functionality than POP3 as a copy of the message is retained on the mail server. It can also provide tasks, calendars, and journaling. There is also a version of secure IMAP.
An easy way to remember the port number for IMAP4 is to pretend the first letter of IMAP is number 1. Then take the last figure, which is 4, for the second digit, and then take 1 from 4 to get for to get 3 for your third digit, giving you 143 the actual port number.
Web Mail (HTTPS): Web mail, such as Microsoft's Outlook Anywhere, is accessed via a secure web browser and uses the HTTPS protocol.
Secure/Multipurpose Internet Mail Extensions(S/MIME): Uses Public Key Infrastructure (PKI) to either encrypt the email or digitally sign the email to prove the integrity of the message. It is very cumbersome as it requires each user to exchange their public key with each other and does not scale very well.
There are two types of name resolution: hostname resolution, which is the most common, and NETBIOS, which is a legacy name resolution that is very rarely used.
The most common form of name resolution is that hostname resolution that comprises of a database of hostnames to IP addresses called DNS that uses a flat file called the hosts file:
Domain Name System (DNS): A hierarchical naming system that takes a hostname and resolves it to an IP address. Just think what it would be like if you wanted to go to a website and you had to remember an IP address—you would have a list on your computer of the names and IP address, as we don't remember number as easily as we remember names. If I want to go to the Microsoft website, I know that I need to enter www.microsoft.com in my web browser and it will take me there. If I have a user called Ian in a domain called ianneil501.com, the hostname portion would be Ian and the Fully-Qualified Domain Name (FQDN) would be ian.ianneil501.com. Entries in the DNS database are:
A: IPV 4 host
AAAA: IPV6 host
CNAME: Alias
MX: Mail server
SRV records: Finds services such as a domain controller
Example: A user would like to visit the website of http://ianneil501.com; to get there, they would enter www.ianneil501.com in their web browser as per Figure 23. The hostname resolution follows a strict process:
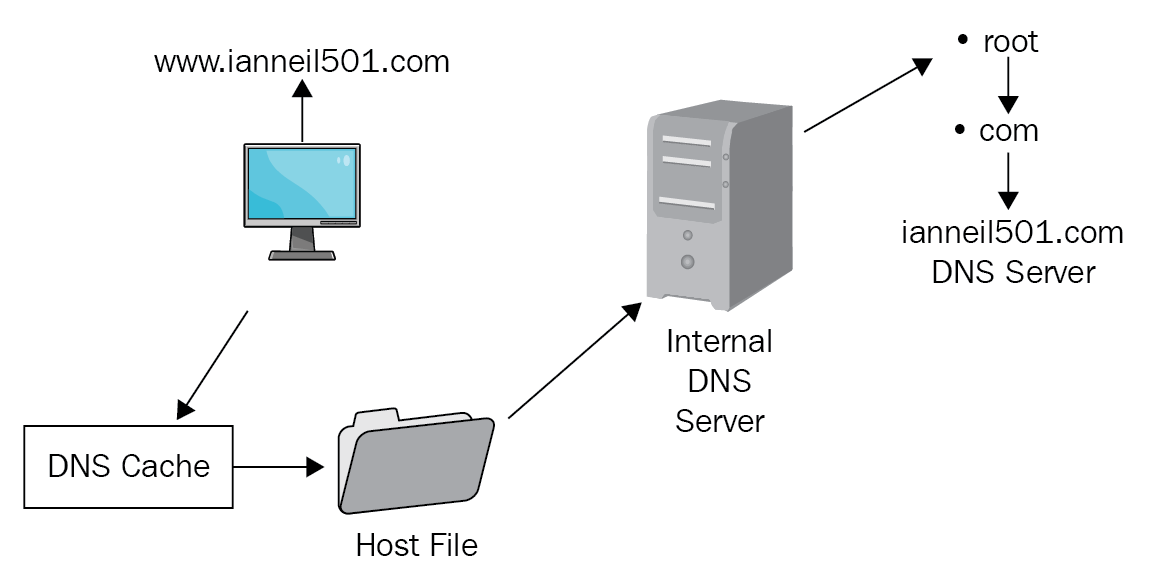
Figure 23: Hostname resolution
In Figure 23, the hostname resolution adopts a strict process and takes the first entry for that hostname no matter whether it is right or wrong, this is a pitfall of the process. Let's look at this process starting with the DNS Cache:
DNS cache: Stores recently resolved names; if the cache is empty, it goes to a flat file called the hosts file. Attackers will attempt to poison the DNS cache by putting in wrong entries to divert you to a server where they can attack you or poison the DNS cache so that you cannot get to a legitimate server.
In the preceding example, the DNS cache is empty so it would move onto the hosts file located on the local computer. If you need to view the DNS cache, you would run the ipconfig /displaydns command, and if you wanted to clear the DNS cache, you would run the ipconfig /flushdns command.
Hosts file: A flat file where entries are manually inserted and read from the top to the bottom. It takes the first entry, whether right or wrong. The purpose of a host file is that if one user needs to go to a server called Sneaky Beaky, I would put an entry for that server in his local hosts file that would allow them to go there. If I put the entry in the DNS server, that would allow anyone to find that server. In the preceding example, the hosts file is empty so name resolution would move to the DNS server, whose IP address is in the local computer's network card.
DNS server: Normally maintains only the hostnames for your domain and would then need to complete a referral process through the root server of the internet, which is represented by a dot.
Root/.com server: Refers the request to the .com server, who in turn refers the request to the authoritative DNS server for the ianneil501.com domain, which would then reply with the IP address of the website.
Cache the reply: A copy of the name resolution is placed in the DNS cache for future use.
To prevent someone poisoning DNS records, DNSSEC was introduced to protect the DNS traffic. Each DNS Record is digitally signed, creating an RRSIG record to protect against attacks assuring you that they are valid and their integrity has been maintained.
Exam tip:
DNSSEC produces a RRSIG record for each host.
NETBIOS is a Microsoft legacy naming convention that has a flat namespace of a maximum of 15 characters with a service identifier. Each computer name has three separate entries in its database, called WINS and it uses a flat file, called the LMHosts file.
The entry for PC1 as a WINS database would be:
PC1 <00>: The <00> represents the workstation service
PC2 <03>: The <03> represents the messenger service
PC3 <20>: The <20> represents the server service
The majority of people use the internet to make purchases and research information, so it is important that we know what the protocols used when accessing websites are:
Hypertext Transfer Protocol (HTTP): Used to access websites, no matter whether you are using Internet Explorer, Chrome, Firefox, or Microsoft Edge.
Hypertext Transfer Protocol Secure (HTTPS): When you are using HTTP and adding items to your shopping cart, you will then be diverted to a secure server that uses HTTPS so that your session is secure and you can then enter your credit or debit card details.
Transport Layer Security (TLS): An upgraded version of SSL that is used to encrypt communications on the internet and transfer data securely, such as email or internet faxing. HTTPS is a common instance of it.
In the past, when companies wanted meetings, such as a sales meeting, a date was set and the salespeople kept their schedule open, travelling to the location of the meeting the night before and booked themselves into a hotel. This was very costly and time-consuming; nowadays we use videoconferencing where everyone connects to the meeting, does not have to travel, and can free their schedule, making them more productive. In the Security+ exam, we need to be able to understand which protocols are used. There are three main protocols and these are:
Session Initiated Protocol (SIP): Allows people from all over the internet, and those with VoIP, to communicate using their computers, tablets, and smartphones. An example would be of a secretary who could receive a Skype call for the boss: SIP allows them to put the caller on hold, speak to their boss, and, if needs be, put the person through.
Real Time Protocol (RTP): Once SIP has established the session, RTP transfers the videoconferencing traffic.
Secure Real Time Protocol (SRTP): Used to secure the videoconferencing traffic, it normally uses TCP port 5061.
VLAN: Voice traffic being placed in a VLAN segments it from the rest of the network.
Media gateway: Allows different methods of video and voice to communicate with each other: for example, if you use an XMPP gateway, you can connect Jabber clients to a Skype session.
Exam tip:
Voice traffic should be placed in its own VLAN to ensure reliability.