Delving into Identity and Access Management
In this chapter we will look at different types of authentication and how to dispose of data, we will first look at identify and access management concepts.
We will cover the following exam objectives in this chapter:
Compare and contrast identify and access management concepts: Identification, authentication, authorization and accounting (AAA). Multifactor authentication—something you are—something you have—something you know—Somewhere you are—something you do. ; Federation—single sign-on—transitive trust
Given a scenario, install and configure identity and access services: LDAP—Kerberos—TACACS+—CHAP—PAP—MSCHAP—RADIUS—SAML—OpenID Connect—OAUTH —Shibboleth—Secure token—NTLM
Given a scenario, implement identity and access management controls: Biometric factors—fingerprint scanner—retinal scanner—Iris scanner—voice recognition—facial recognition—false acceptance rate—false rejection rate—crossover error rate. Tokens—hardware—software—HOTP/TOTP. Certificate-based authentication—PIV/CAC/smart card—IEEE 802.1x
Given a scenario, differentiate common account management practices: Account types—user account—shared and generic accounts/credentials—guest accounts—service accounts—privileged accounts—permission auditing and review—usage auditing and review—time-of-day restrictions—re-certification—standard naming convention—account maintenance—group-based access control—location-based policies. Account policy enforcement—credential management—group policy—password complexity—expiration—recovery—disablement—lockout—password history—password reuse—password length
One of the first areas in IT security is giving someone access to the company's network to use resources for their job. Each person needs some form of identification so that they can prove who they are; it could be anything ranging from a username to a smart card. It needs to be unique so that the person using that identity is accountable for its use. The second part after proving your identity is to provide authorization for that identity; this can be done in many ways for example inserting a password or if you have a smart card it would be a PIN.
Passwords are one of the most common ways of authenticating a user; they are also the authentication factor that is most likely to be inserted incorrectly, maybe because they use higher and lower-case characteristics, numbers, and special characters not seen in programming. Some people may have the caps lock reversed without knowing it. When the password is inserted, it is shown as a row of dots therefore users cannot see their input, however, in the password box in Windows 10 you can press the eye to see the password that you have inserted. This reduces the risk of people being locked out.
An administrator should have two accounts, one for day-to-day work and the other for administrative tasks. If your company is using a device such as a wireless router, the default administrative username and password should be changed as they are normally posted on the internet and could be used for hacking your device/network.
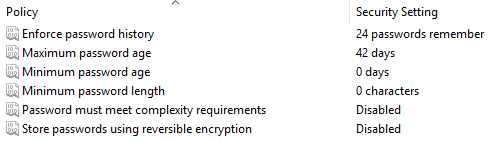
A group policy allows security administrators to create settings once and then push them out to all machines in their domain. This could cover maybe 5-10,000 machines. It reduces configuration errors and reduces the labor required to carry out the task. One portion of a group policy deals with passwords; please look at the screenshot:

Figure 1: Password policies
Let us look at each of these going from the top to the bottom.
Enforce password history: Enforce password history prevents someone from just reusing the same password. The maximum number that can be remembered is 24 passwords as set above. This would then mean when I set my first password it would then need another 24 passwords before I could use it again.
Password reuse: Password reuse is a term used in the exam that means the same as password history. They both prevent someone from reusing the same password. Password History would be used for a windows operating system and password reuse for any other products. An example of this could be a smartphone or an email application.
Maximum password age: It is the maximum amount of days that a password can be used for before you are required to change it. The default is 42 days but in a more secure environment it could be lowered to maybe 21 days; this is really the maximum time that the password can be used. If it was set at 21 days you could reset at any time before 21 days passed.
Minimum password age: The minimum password age is to prevent someone from changing a password 25 times on the same day to enable them to come back to the original password. If you set the minimum password age to 2 days then you could only change your password every two days. This is also known as the password expiry date. For example, if I set the password maximum age to 21 days, the password history to 24, and then the minimum password age to 1 day, this would prevent someone from reusing the same password. Each day you could set your password but you could only use 21 passwords in the password cycle.
Password must meet complexity requirements: Complex passwords (sometimes known as strong passwords) are formatted by choosing three groups from the following:
Lowercase: a b c
Uppercase: A B C
Numbers: 1 2 3
Special characters not used in programming: $ @
If I choose the password P@$$w0rd, then it contains characters from all four groups but it would be cracked very quickly as most password crackers replace the letter o with a zero and replace an a with the @ sign.
Store passwords using reversible encryption: This is when a user needs to use his credentials to access a legacy (old) application, because it is storing them in reversible encryption they could be stored in clear text—this is not good. Companies tend to have this option disabled at all times as it poses a security risk.
Account lockout threshold: Account Lockout Threshold determines the number of times that a user can try a password before the system locks you out; companies normally set this value to 3 or 5 attempts. .
When purchasing devices, you should always change the default password that the manufacturer has set up to prevent someone hacking into your device.
Once you are locked out your account is disabled:
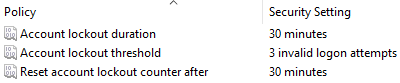
Figure 2: Account lockout
Know the password options and types of password attacks thoroughly.
Account lockout duration: Both Account lockout duration and Reset account lockout counter after should not be enabled. If these are disabled the person locked will have to contact the security administrator to have their password reset; this way the administrator knows who keeps for getting their password and knows to keep monitoring them.
People can be locked out from time to time by forgetting their password. They can reset their passwords by going to a portal and selecting forgotten my password, then filling in personal details and having the password reset option send a code to their phone via SMS, or by email.
Some desktop operating systems allow you to create a password reset disk so that you can save to a SD card or a USB drive; this is not normally used in a corporate environment.
There are different authentication factors that range from something you know, for example a password, to something you are using, for example an iris scanner. The following are the different authentication factors:
Multifactor authentication: These factors are grouped into different types and the number of factors is the number of different groups being used. For example, if you have a smart card, this is something you have and the PIN is something you know; this means it is dual factor, but the smart card and PIN is also known as multifactor. Multifactor could also be more than two different factors—it just means multiple factors.
Something you know: This would be a username, password, PIN, or your birth date; these are all something that you know:

Figure 3: Hardware token and key fob used with proximity card
Something you have: A secure token, key fob, or a card. The hardware token is tamper proof and sends a different PIN every 60 seconds. The key fob is similar to some cards that are placed close to a proximity card; once you hear a beep then the door opens. A smart card that could be used with a PIN could also be something you have.
Something you are: The is called biometric authentication; it is the trait of a person for example, iris or retina scanner, palm or fingerprint reader or your voice.
Something you do: This would be swiping a card, inserting your signature, or maybe the way you walk (this is called your gait). It could also be the dwell time, for example the speed that you type and how far in you press the keys.
Somewhere you are: This would be a location that you are in. Are you in London or Disneyland, Florida? This is a location-based policy.
Let us look at combining the different factors to determine single factor, dual factor, or multifactor. Here are different factor examples:
Single factor: If I have a username, password, and PIN then it is only single factor as they come from the same group.
The number of factors is determined by the different numbers of factor groups being mentioned.
Two factor: If you have a smart card and a PIN, this is two factor, also known as dual factor.
Multifactor: This is where more than one factor can be used, for example if you combine a hardware token with a PIN.
Transitive trust is where you have a parent domain and maybe one or more child domains; these would be called trees. Refer to the diagram:
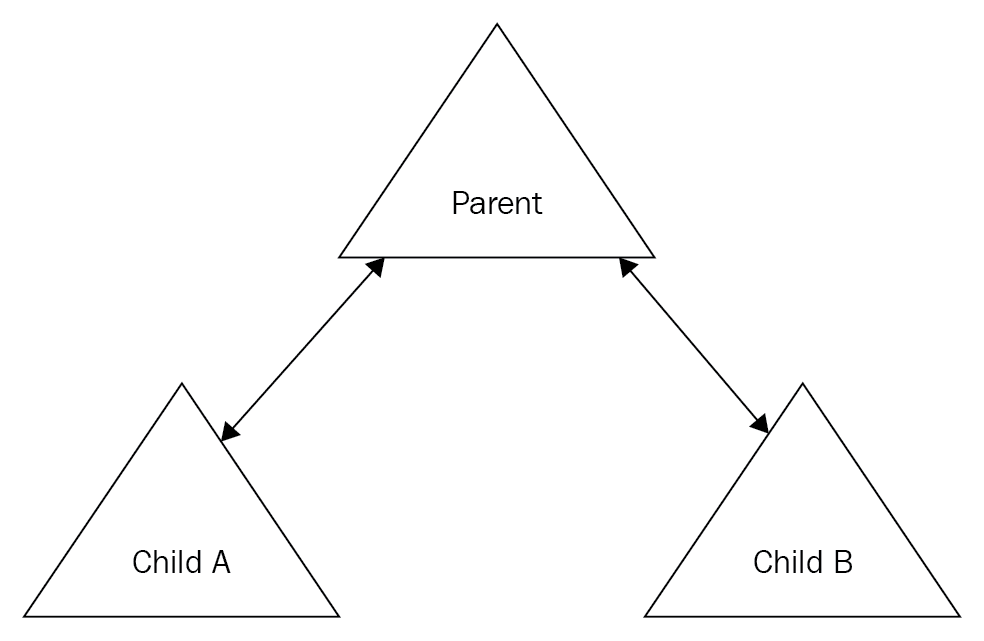
Figure 4: Transitive trust
Between the parent domain and each child domain is two-way transitive trust, where resources can be shared two ways. Because the parent domain trusts both child domains A and B, it can be said that Child A transitively trusts Child B as long as the administrator in Child B wishes to give someone from Child A access to resources and vice versa. Think of a domain as being people from the same company.
When the exam mentions third-party to third-party authentication, then that can only be federation services.
Federation services are used when two different companies want to authenticate between each other when they participate in a joint venture. Think of two car manufacturers wanting to produce the best car engine in the world. Both companies have experts on engines but they want to work together to produce a super engine.
The companies don't want to merge with each other; they want to retain their own identify and have their own management in place. These are known, to each other, as third parties.
Each of these companies will have their own directory database, for example an active directory that will only have users from their domain. Therefore, normal domain authentication will not work. Let us now look at the two different domains and their directory databases:
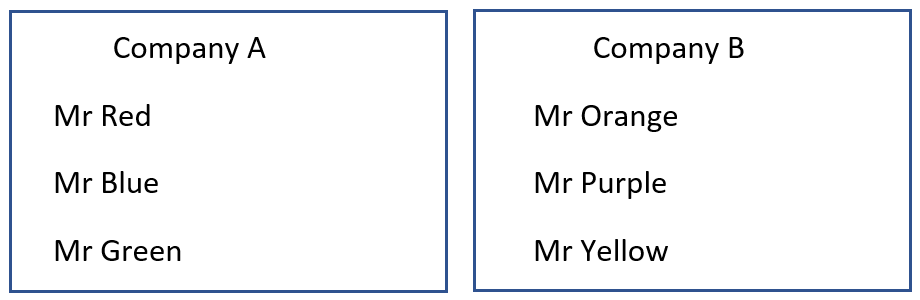
Figure 5: Directory databases
Company A has three users in his active directory: Mr Red, Mr Blue, and Mr Green. Company B also has three users: Mr Orange, Mr Purple, and Mr Yellow. This means that they can only change passwords for the people in their own domain.
If Mr. Orange was to try and access the Company A domain he would need an account. Since he does not have an account the security administrator from Company A has no way of providing authentication. He then needs to make an agreement with Company B to set up a federation trust where the people from the other domain would need to use alternative credentials instead of a username and password or a smart card and PIN. They use extended attributes:
User-extended attributes are extended attributes used by their directory services; they are, in addition to the basic attributes:
Employee ID
Email address
They both have decided that the extended attributes that they will use will be the user's email address. Because an email address is easy to find or guess they will also need to use their domain password. This is known as a claim. When the exam talks about authentication using the phrase third party or extended attributes, think of federation services.
The two companies need to exchange the extended attribute information and need a special protocol to do that, so they use Security Assertion Mark-up Language (SAML) as it is XML based authentication:
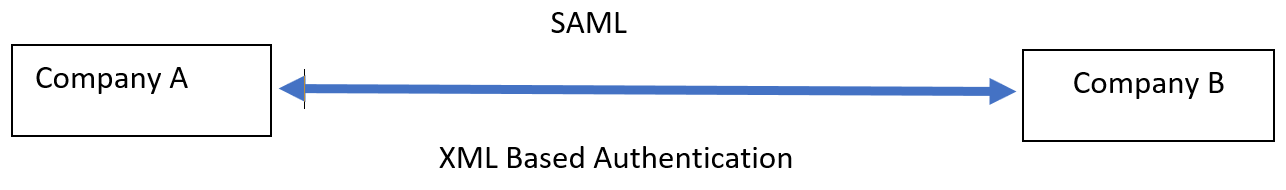
Figure 6: SAML
Federation Services—Authentication: In this scenario Mr. Yellow is going to authenticate himself with Company A so that he can access limited resources. He contacts Company A through a web browser and it asks him for his email address and password:
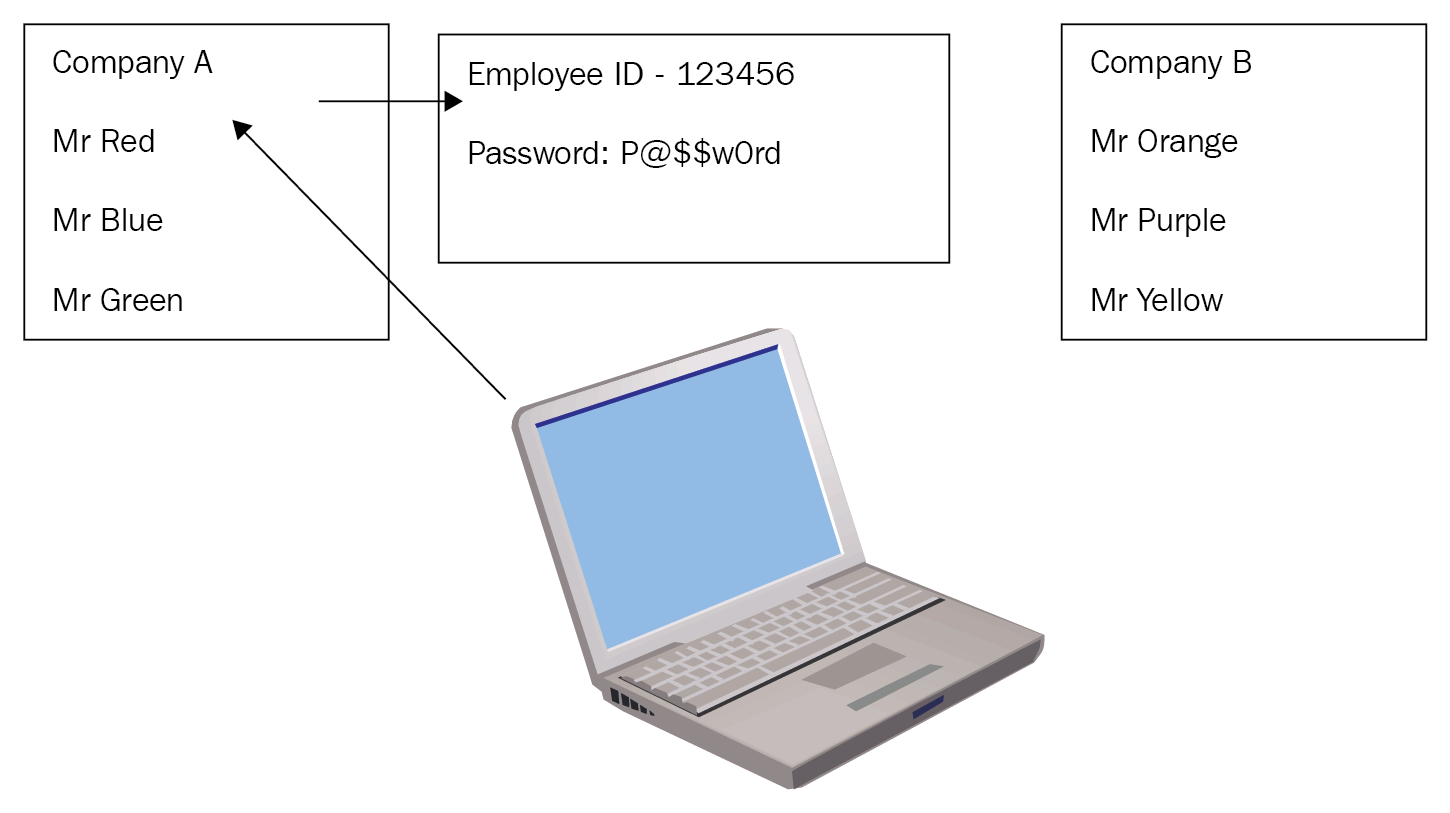
Figure 7
Federation Services—Exchange of Extended Attributes: Company A now uses SAML to send the authentication details of Mr Yellow to Company B. Mr Yellow's domain controller confirms that they are correct:
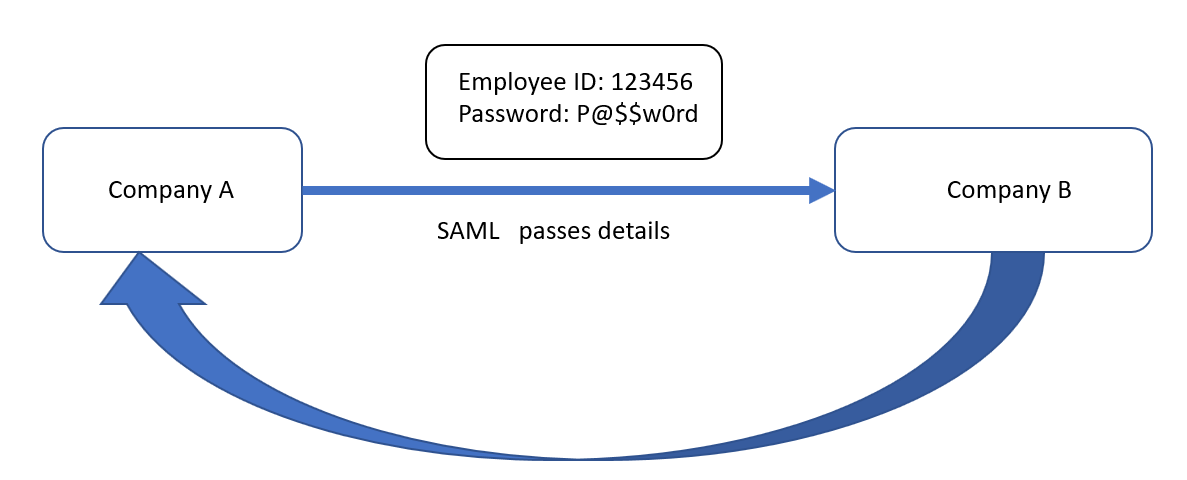
Figure 8: Extended attributes sent to Company A using SAML
Once Company B confirms that Mr Yellow's extended attributes are valid the Company A domain controller sends a certificate to Mr Yellow's laptop; this certificate is used next time for authentication.
When the exam mentions authentication using extended attributes, they can only be federation services.
Shibboleth is an open source federation service product that uses SAML authentication. It would be used in a small federation service environment.
Single sign-on is used in a domain environment; this is where someone logs in to the domain and then can access several resources such as the file or email server without needing to input their credentials again. Think of it as an all-inclusive holiday where you book into your hotel and the receptionist gives you a wristband that you produce when you want to consume food and drink. federation services and Kerberos (Microsoft authentication protocol) are both good examples of single sign-on. You log in once and access all of your resources without needing to insert your credentials again.
Identify management in a corporate environment will use a directory database we are going to look at Microsoft's Active Directory, where a protocol called Lightweight Directory Access Protocol manages the users are groups. Let us look at how it works.
Most companies have identity and access services through a directory services that stores objects such as users and computer as X500 objects; these were developed by the International Telecommunication Union (ITU). These object form what is called a distinguished name and are organized and stored by the Lightweight Directory Access Protocol (LDAP).
There are only three values in X500 objects; these are DC (domain), Organization Unit (OU), and CN (anything else).
In this example, we have a domain called Domain A and an organizational unit called Sales; this is where all of the sales department users and computers would reside. We can see inside the Sales OU a computer called Computer 1:
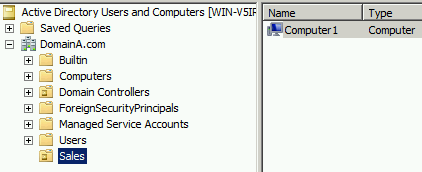
Figure 9: Active Directory
When creating the X500 object we start off with the object itself, Computer 1, and then continue up through the structure. As Computer 1 is neither an OU or domain, we give it a value of CN, then we move up the structure to Sales. As it is an OU, we give it that value. Computer 1 is a CN, sales is a OU and the domain is into two portions, each having the value of DC. The distinguished name is here:
CN=Computer1, OU=Sales, DC=DomainA, DC=com
The way it is stored in the active directory can be viewed using a tool called ADSI Edit:
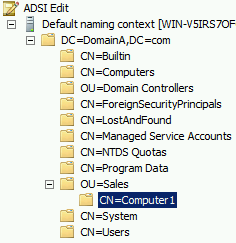
Figure 10: ADSI Edit
LDAP is the active directory storeman responsible for storing the X500 objects; when the Active Directory is searched, then LDAP provides the information required. LDAPS is the secure version of LDAP.
Examples:
If I want to know how many people are in the IT OU, I can search the Active Directory. LDAP provides the search and returns a reply saying that the IT department has 10 members.
I am searching the Active Directory for a user called Fred. Once again LDAP finds the user. If you have 10,000 people in your domain you will have them in different OUs to make it easier to find and manage them. However, if you need to find someone it will still be difficult; that is why we need LDAP to perform the search. It saves time.
Kerberos is the Microsoft authentication protocol that was introduced with the release of Windows Server 2000. It is the only authentication protocol that uses tickets, updated sequence numbers (USN), and is time stamped. The process of obtaining your service ticket is called a ticket granting ticket (TGT) session. It is important that the time on all servers and computers are within five minutes of each other; time can be synchronized by using a time source such as the Atomic Time clock. The Security+ exam looks at Stratum time servers.
Stratum Time Servers: There are three types of Stratum time servers, Stratum 1, 2, and 3. Stratum 1 is internal and Stratum 0 is external and the reference time source. The way to remember this is that you can draw a clock face inside a zero making it the time source. The Stratum 1 time server is linked directly to Stratum 0, the time source. The Stratum 2 time server is linked to the Stratum 1 through a network connection:
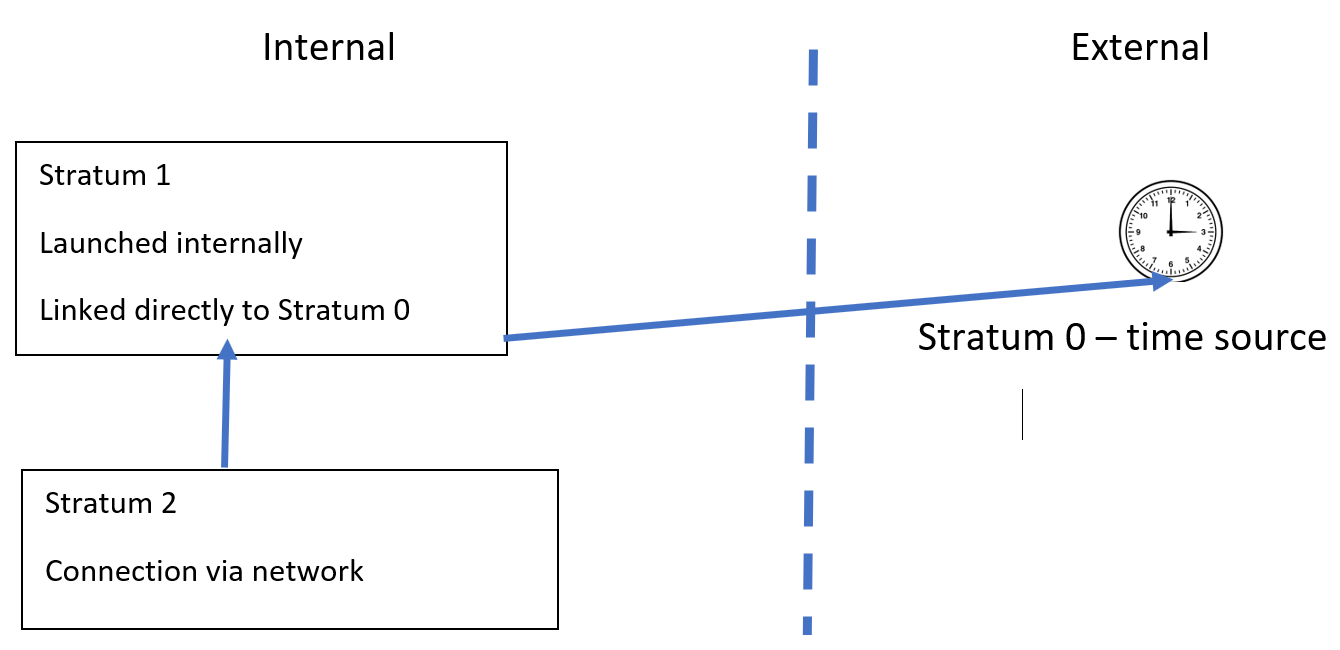
Figure 11: Stratum time servers
A TGT session is where a user sends their credentials (username and password, or it could be smart card and PIN) to a domain controller that starts the authentication process and when it has been confirmed it will send back a service ticket that has a 10-hour lifespan. This service ticket is encrypted and cannot be altered:

Figure 12: TGT session
Single sign-on/mutual authentication: Kerberos provides single sign-on as the user needs to login in only once then uses his service ticket to prove who he is; this is exchanged for a Session Ticket with the server that they want to access resources on. In the example here, the user will use his or her service ticket for mutual authentication with an email server:
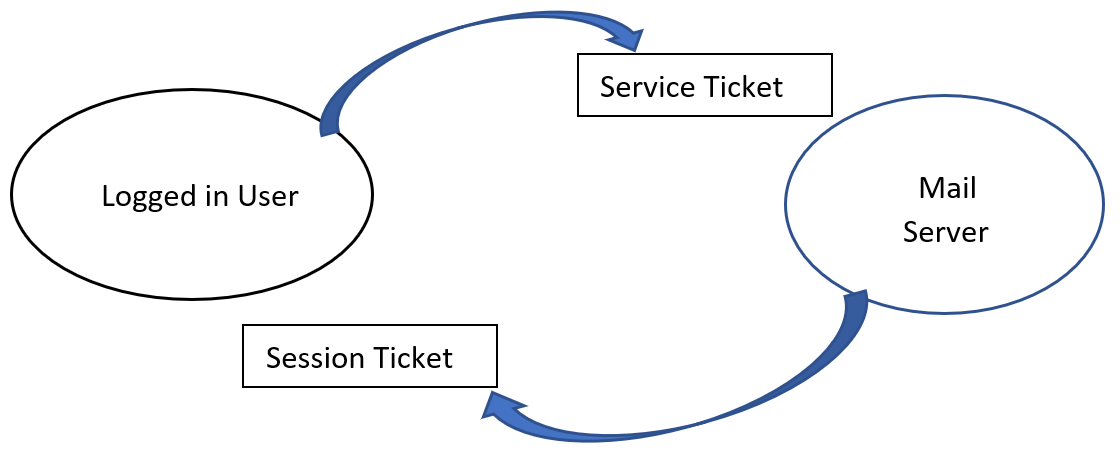
Figure 13: Mutual authentication
The preceding diagram shows the logged-in user exchanging his encrypted Service Ticket with the mail server which in return provides mutual authentication by returning a session ticket. The logged-in user checks the session ticket's timestamp is within 5 minutes of the domain controllers. This means that Kerberos can complete mutual authentication.
You need to remember that Kerberos is the only authentication protocol that uses tickets. It will also prevent replay attacks as it uses USN numbers and timestamps.
NT Lan Manager (NTLM): NTLM is a legacy authentication protocol that stores the passwords using the MD4 hash that is very easy to crack. It was susceptible to the Pass the Hash attack; it was last used in a production environment in the 1990s.
More and more people are accessing web-based applications and need an account to log in, however applications hosting companies do not want to be responsible for the creating and management of the account accessing the application. They use OAuth to help them facilitate this:
OAuth 2.0: OAuth 2.0 provides authorization to enable third-party applications to obtain limited access to a web service. OAuth allows secure authorization in a simple and standard format for web, mobile, and desktop applications.
Open ID Connect: Open ID Connect uses OAuth to allow users to log in to a web application without needing to manage the user's account. It allows users to authenticate by using their Google, Facebook, or Twitter account. For example, the Airbnb website that finds users accommodation allows you to sign up using your Google or Facebook account.
The main two AAA servers are Microsoft's Remote Authentication Dial-In User Service (RADIUS) and CISCO's Terminal Access Controller Access-Control System Plus (TACACS+). Both of these servers provide authentication, authorizing, and accounting:
RADIUS server: The RADIUS server is UDP based and it authenticates servers such as virtual private network (VPN) servers, remote access services (RAS) servers, and the 802.1x authenticating switch. Each of these are known as RADIUS clients even though they are servers themselves. If I had a small company I could outsource my remote access server but put in a RADIUS server which would check any remote-access policies and verify that authentication was allowed by contacting a domain controller.
RADIUS clients: RADIUS clients are VPN servers, RAS server, and the 802.1x authentication switch. Every RADIUS client need the secret key that is sometimes called the session key to join the RADIUS environment. RADIUS communicates over UDP port 1812. It is also known as non-proprietary.
Diameter: Diameter is the more modern version of RADIUS that works on TCP. For the exam, remember, Diameter is the AAA server that uses the EAP.
TACACS+: This is a CISCO AAA server that used TCP so it is more secure that RADIUS, it was TCP port 49.
A Virtual Private Network (VPN) allows someone working remotely either from a hotel room or home to connect securely through the internet to the corporate network. More information on how the VPN operates will be in Chapter 5, Understanding Network Components, at this book; we are going to look at VPN authentication methods in this chapter:
Figure 14: VPN
Remote Access Services (RAS): RAS is a legacy protocol that pre-dated the VPN; the RAS client used modems and a dial-up network using telephone lines. It was very restricted in speed.
Authenticated for VPN/RAS: There are numerous methods of authentication used by VPN or RAS. We will look at these here:
Password Authentication Protocol (PAP): The Password Authentication Protocol (PAP) should be avoided at all costs as the passwords are transmitted as clear text and can be easily captured.
ChallengeHandshake Authentication Protocol (CHAP): Challenge Handshake and Response (CHAP) was used to connect to a RAS server with a four-stage process:
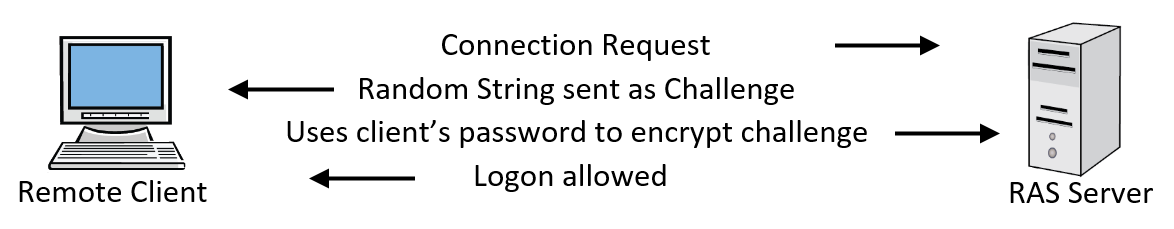
Figure 15: Challenge-Handshake Authentication Protocol
The client makes a connection request to the remote access server.
The RAS server replies with a challenge that is a random string.
The client uses his password as an encryption key to encrypt the challenge.
The RAS server encrypts the original challenge with the password stored for the user. If the both values match, then the client is logged on.
MS CHAP/MSCHAP version 2: MS CHAP/MSCHAP version 2 are Microsoft's version of MS CHAP. MS CHAP has been superseded by MS CHAP v 2 and can be used by both VPN and RAS.
In this section, we are going to look at identity and management controls, starting with biometrics and moving on to security tokens and certificates. Let us first look at biometric controls followed by identity management using certificates.
Biometrics is a method of authentication using an individual's characteristics, for example, using a fingerprint as everyone's fingerprints are very different. In 1892, Inspector Eduardo Alvarez from Argentina made the first fingerprint identification in the case against Francisca Rojas who had murdered her two sons and cut her own throat in an attempt to place blame on another, but the inspector proved that she was guilty. We will now look at the types of biometrics:
Fingerprint scanner: Fingerprint scanners are now very common; for example, f you are going to the USA on holiday, when you go through customs you are required to place all of your fingerprints in the scanner. Another use of a fingerprint scanner is when you are setting up your iPhone; you can set it up so that you press the home button to log in instead of using a password. Refer to the screenshot:
Figure 16: iPhone fingerprint scanner
Retina and iris scanners both look at an individual's eye and the scanners themselves are physical devices.
Retina scanner: The retina is the light-sensitive layer of tissue that lines the inside of the eye and sends visual messages through the optic nerve to the brain. The blood vessels of the retina absorb light more readily than the surrounding tissue and are easily identified with appropriate lighting.
Iris scanner: The iris is the round, colored part of the eye. Iris recognition uses mathematical pattern-recognition techniques on video images of one or both of the irises of an individual's eyes—these patterns are very complex and unique. Most countries have issued biometric passports where the person inserts their passport into the reader and a camera about 1.5 meters away confirms the identity of the user.
Voice recognition: Voice biometrics works by digitizing a profile of a person's speech to produce a stored model voice print; these prints are stored in databases similar to the storing of fingerprints or other biometric data.
Facial recognition: Facial recognition looks at the shape of the face and the characteristics such as mouth, jaw, cheekbone, and the nose. Light can be a factor when you use this software. There are much better versions of facial recognition, such as those that use infrared. You need to ensure that you are looking straight at the camera each time.
Microsoft has released a facial recognition program called Windows Hello that was released with Windows 10; this uses a special USB infrared camera. It being infrared it is much better than other facial recognition programs that can have problems with light.
False acceptance rate (FAR): FAR is what it says on the tin: it accepts unauthorized users and allows them to gain access. It is known as a Type II error.
False rejection rate (FRR): FRR is where legitimate users who should gain access are rejected and cannot get in. It is known as a Type I error.
Crossover error rate: Crossover Error Rate is where both the FAR and FRR are equal:
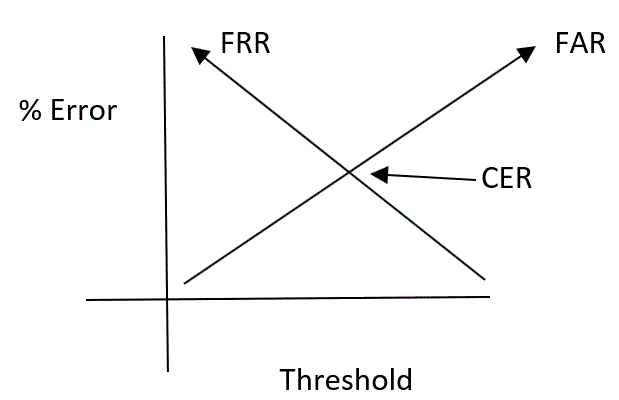
Figure 17: Crossover error rate
If the CER point is lower down the graph, then there are fewer errors, but if it is at the top of the graph it indicates many errors and could prove more difficult to support; if this was the case, you would change your biometric system.
There are different types of tokens that have different time limits; let us look at the difference between the Time-Based One-Time Password and HMAC-based one-time password:
Time-Based One-Time Password (TOTP): A TOTP requires time synchronization, because the password needs to be used in a very short period of time, normally between 30 and 60 seconds. Here, we can see the TOTP that has come to a phone—it can also come to a device similar to the RSA Secure ID shown earlier in this chapter. TOTP could be used when you want to access secure cloud storage:
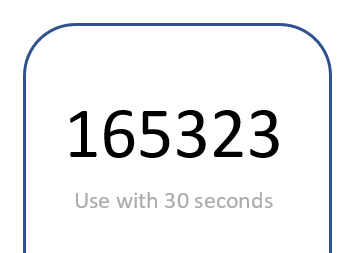
Figure 18: TOTP
HMAC-based One-Time Password (HOTP): A HOTP is similar to TOTP in that a one-time password is issued; the main important factor is that there is no restriction on time but you can only use this password once.
Certificate-based authentication is very popular as it provides two-factor authentication that makes it more secure than single-factor authentication such as a username and password. We will now look at various types:
Smart card: As previously mentioned in this book, a smart card looks like a credit card with a chip on it. The certificate is located on the chip itself and does not leave any trace (footprint) on the computer or laptop being used.
Common Access Card (CAC): CAC are used by governmental and military personnel as they provide both authentication and identification as it has a picture of the user on it. They are similar to a smart cards. On the front side of a CAC is a picture of the users with their service—army, navy, or air force—and on the reverse side show their blood group and their Geneva Convention Category. To view a CAC card please go to: http://www.cac.mil/Common-Access-Card/.
Personal Identity Verification (PIV): This is very similar to the CAC but is used by federal agencies rather than the military.
1EEE 802.1x is a port-based authentication protocol that is used when a device is connected to a switch or when a user authenticates to a wireless access point.
Authentication with a password with a short lifespan will be a Time-Based One-Time Password (TOTP).
Account management ranged from account creation on start up to its disablement when someone leaves the company. Fully understanding these concepts is crucial to obtaining the Security+ certification.
Each user in a system needs an account to access the network in a Microsoft Active Directory environment; the user account has a Security Identifier (SID) linked to the account. When I create a user called Ian they may have an SID of SID 1-5-1-2345678-345678. When the account is deleted the SID is gone and a new SID is created.
For example, a member of the IT team has deleted a user account called Ian—it may have a SID of SID 1-5-1-2345678-345678, so he quickly creates another account called Ian but this account cannot access resources as it has a new SID of SID 1-5-1-2345678-3499999. The first portion from left to right, identifies the domain and then the remainder is a serial number that is never reused.
There are various different types of user accounts and these are heavily tested in the Security+ exam; you must know when you would need each account:
User account: A user account, also known as a standard user account, has no real access. They cannot install software—they just give users limited access to the computer systems. There are two types of user accounts: those that are local to the machine and those that access a domain. A domain is another name for a large group of users.
Guest account: A guest account is a legacy account that was designed to give limited access to a single computer without the need to create a user account. It is normally disabled as it is no longer useful and some administrators see it as a security risk.
Sponsored guest account: A sponsored guest account is used for external speakers who may need access to the internet via a wireless router to show internet content whilst delivering their presentation to maybe a group of university students or company employees. For example, John Smith has been asked by Company A to deliver a presentation to company employees about a new pension plan. While he is delivering the presentation, he wants to show the latest share prices for the stock market. The finance department have asked the IT department to let John Smith access the company network to use the internet. The IT Director decided the best course of access was to create a sponsored guest account that would allow John to have access to the company guest WiFi.
A guest speaker should be allocated a sponsored guest account.
Privilege account: User accounts do not have rights but privilege accounts have much higher access to the system and tend to be used by members of the IT team. Administrators are an example of privilege accounts.
Administrative account: An administrative account can install software and manage the configuration of a server or a computer. They also have the privileges to create, delete, and manage user accounts. An administrator should have two accounts: a user account for routine tasks and then an administrator account to carry out their administrative duties.
Service account: When software is installed on a computer or server it needs higher levels of privilege to run the software, but at the same time we need a lower level administrative account and the service account fits the bill. An example of this is an account to run an anti-virus application.
A service account is a type of administrator account used to run an application.
Shared account: When a group of people perform the same duties, such as members of customer services, they can use a shared account. The people monitoring this account can send a reply coming from the shared account. If you need to set up monitoring or auditing to individual employees you must eliminate the practice of using shared account. For example, a multinational corporation that has 100,000 employees has five members of the Human Resources (HR) team that receive and process email applications from potential employees. They all use a shared account called jobs@corporations.com and between them they open and action the CVs they receive. Mr Grumpy was one of the people who applied for a job within the company and has complained to the Chief Executive Officer (CEO) because he was not happy with how his application was handled. The CEO wanted to know which of the HR employees was responsible but could not identify the person responsible as all five members of the HR team denied dealing with the application.
When you need to monitor or audit to an employee level, you must eliminate the use of shared accounts.
Generic accounts: Generic accounts are default administrative accounts created by manufacturers for devices ranging from baby alarms, smart ovens, and smart TVS; they all have a default usernames and passwords. If you surf the web for the device that you have purchased it very easy to find the credentials to hack that device. As cybercrime is increasing each day we should rename the default account name and its associated password. At the time of writing this book, Security Week has published an article on hacking a home oven; it can be viewed at https://www.securityweek.com/security-flaw-could-have-let-hackers-turn-smart-ovens. Here's another example. Baby monitors are getting more sophisticated and come with the ability to see and hear your baby from somewhere else in your home via a web browser. When the police have investigated such instances, they have found out that the baby monitors can be used to film children when they are asleep using the default user account and password; most parents are unaware that this is possible.
If you do not change the default username and password for household devices it is possible for a cybercriminal to hack into your home. This includes baby monitors, TVs, ovens, and refrigerators.
Multinational corporations will make hundreds of accounts annually and need to have a standardized format; this is called a standard naming convention. Account templates are copied and modified with the details of new employees. Some examples of standard naming conventions are:
First name, last name: John.Smith
Last name, first name: Smith.John
First initial, last name: J.Smith
If you have John Smith and Jack Smith you would have two J Smiths, therefore you may also use a middle initial—J A Smith—or a number at the end—J Smith1—to make them unique.
All user accounts need to be unique so that each person is responsible for their own account. If you leave your computer logged on to the network whilst you go for a coffee and someone deletes data using your account then you are held responsible. A good practice would be to lock your screen while you are not at your desk to prevent this.
Without a standard naming convention, accounts would be created differently and cause chaos when you tried to find users in your directory service.
When employees move between departments, IT teams normally modify their account for the next department they move to; they don't generally get a new account. In the Security+ exam, when people move department, they are given new accounts and the old account is active until it has been disabled.
There are a few times when the IT team will disable accounts as good practice; let us look at the reasons for this:
Employee leaving: A good practice when someone leaves the company is that human resources provide the employee with an exit interview to find out the reasons that they are leaving. The final step is that the IT team should disable their accounts and reset their passwords. These steps keep their email and certificate settings so that encrypted data can still be accessed and they can no longer access the network. If you delete the account, then you lose all of this.
Extended absence period: When an employee is away from a company for a month or more then it may be prudent to disable the account so that it cannot be accessed. It could well be that the employee is on maternity/paternity leave, seconded to another company, on a long course, or taking a gap year to fulfill one of their dreams. It then means that, while they are away, the account cannot be hacked and can be reactivated once they return.
Guest account: Guest account are designed for temporary users but are seldom used; they are disabled to prevent them being hacked.
When an employee leaves a company the first stage is that the account is disabled and not deleted. You will also reset the password so that the old account holder cannot use the account.
Account recertification is a process where an auditor will review all of the user accounts. The auditor will have a matrix showing all of the active accounts and what privileges and access that they should have. If the auditor finds anything wrong then he will report it to the management, who will then either write a new account policy or make changes to the management of accounts using change management. For the purpose of the exam the auditor should be looked at as a snitch—he will never take any action but he will report his findings to the management.
Account maintenance is ensuring that accounts are created in accordance with the standard naming convention, disabled when the employee initially leaves, then deleted maybe 30 days later.
If you wish to find out when a user account has been granted a new set of privileges then this can only be done via active monitoring of the accounts. This could be automated by using a security information and event management (SIEM) system that will create and alert you about changes to the system. You will not be alerted by user account review as there could be 6-12 months between the review—you may need to know immediately.
If you want to know immediately when there is a change to a user account such as it being given higher privileges then you need active account monitoring.