
In this chapter we will look at different frameworks and guides and how to best dispose of data, we will start off look at frameworks and reference architecture and guides.
We will cover the following exam objectives in this chapter:
Explain use cases and purpose for frameworks, beast practice sand secure configuration guides: Industry-standard frameworks and reference architectures—regulatory—non-regulatory—national versus international—industry-specific frameworks. Benchmarks/secure configuration guides—platform/vendor-specific guides—web server—operating system—application server—network infrastructure devices. General purpose guides—vendor diversity—control diversity—administrative—technical—user training
Given a scenario, carry out data security and privacy Practices: Data destruction and media sanitization—burning—shredding—pulping—pulverizing—degaussing—purging – wiping. Data sensitivity labelling and handling—confidential—private—public—proprietary—PII—PHI. Data roles—owner—steward/custodian—privacy officer. Data retention—legal and compliance
Industry standard frameworks are a set of criteria within an industry relating to carrying out operations known as best practices; this is the best way that the operations should be set up and carried out. Best practice produces better results than a standard way of setting up the operations.
These industry standard frameworks are carried out by all members of that industry. In networking, the International Standard Organization (ISO) is responsible for the industry framework within communications and the IT industry. The ISO is a body comprised of international standards bodies that mainly look at communication.
Reference architecture is a document or a set of documents to which a project manager or other interested party can refer to for best practices; this will include documents relating to hardware, software, processes, specifications, and configurations, as well as logical components and interrelationships.
ISO/IEC 17789:2014 specifies the cloud computing reference architecture (CCRA). The reference architecture includes the cloud computing roles, cloud computing activities, and the cloud computing functional components and their relationships.
ISO developed the Open Systems Interconnection model (OSI model). It is a conceptual model that standardizes the communication functions of a telecommunications or computing system, without regard to its internal structure and technology.
The purpose of the OSI reference model is to provide guidance to vendors and developers so that products they develop can communicate with one another.
The OSI reference model is a seven-layer model, and each layer provides specific services. The CompTIA Security + exam focuses mainly on layers 2, 3, and 7:
|
Layer |
Description |
Purpose |
Packet structure |
Devices |
|
7 |
Application |
The applications are windows sockets, such as HTTP for web browsers or SMTP for email. |
|
|
|
6 |
Presentation |
Formats data into a character format that can be understood. It can also encrypt data. |
|
|
|
5 |
Session |
Responsible for logging in and out. |
|
|
|
4 |
Transport |
TCP—connection orientated; UDP—connectionless |
Datagrams |
|
|
3 |
Network |
Responsible for Internet Protocol (IP) addressing and packet delivery |
Packets |
Layer 3 switch router |
|
2 |
Data link |
Works with Media Access Control (MAC) addresses. Checks for transmission errors from incoming data and regulates the flow of data |
Frames |
Switch VLAN IPSec ARP |
|
1 |
Physical |
Transmits data in raw format bits over a physical medium (cables) |
Bits |
Hub repeater |
Exam tip:
Although Security+ is not a networking exam, you must ensure that you are familiar with devices that operate at layers 2, 3, and 7. These will be covered fully in Chapter 5, Understanding Network Components, of this book.
The TCP/IP Protocol is the protocol or language used in modern communications; it is the only protocol used by the internet. The TCP/IP model is derived from the OSI reference model, and it is a four-layer model:
|
Layers |
TCP/IP model layers |
Corresponding OSI layers |
|
4 |
Application |
Application, presentation, and session |
|
3 |
Transport |
Transport |
|
2 |
Internet |
Network |
|
1 |
Network |
Data link and physical |
There are different types of frameworks covered in the Security + exam, and these are listed here:
Regulatory: Regulatory frameworks are based on statute law and governmental regulations that companies must abide by them at all times. Failure to do so will result in a regulatory fine.
Example 1: The General Data Protection Regulation (GDPR) (EU) 2016/679 is a regulation in EU law on data protection and privacy for all individuals within the European Union. It addresses the export of personal data outside the EU. Companies within the European Union can be fined 4% of their annual turnover, up to €20 million.
Example 2: The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is United States' legislation that provides data privacy and security regulations for safeguarding medical information. Regulatory fines ranging from $100 – $1.5 million can be awarded for each violation.
Non-regulatory: This is not enforceable by law and is optional, but provides a framework that organizations can follow as a best practice.
Example 3: The Information Technology Infrastructure Library (ITIL) is a set of detailed practices for IT service management through a service's life cycle.
The ITIL has five distinct life cycle stages:
Service strategy
Service design
Service transition
Service operation
Continual service improvement
Example 4: COBIT 5 is similar to ITIL in that it seeks to provide management with an IT governance model that helps deliver value from IT and manages the risks associated with IT.
The five COBIT principles are as follows:
Meeting stakeholder needs
Covering the enterprise end to end
Applying a single integrated framework
Enabling a holistic approach
Separating governance from management
National versus international: National frameworks could be the Data Protection Act 2018, which is a United Kingdom regulation on data protection and how it can be used; it was given Royal Assent from the Queen of England on May 23, 2018. An international frameworks example is the IS0/IEC 27002, which provides a framework for IT security and is used by the international community.
Industry-specific frameworks—finance: The International Financial Reporting Standards Foundation (IFRS) is a non-profit accounting organization. The purpose of the IFRS is to standardize financial reporting internally. It only deals with the finance industry.
Every company faces the challenge of protecting its servers and computers from an ever-increasing cyber security threat. There are many different types of servers: web servers, email servers, and database servers, and each of these has different configurations and services, so the baselines are different for each type of server. Vendors and manufacturers will provide platform/vendor guides so that their product can be configured as per their own best practices so that they perform as best they can.
Exam tip: Policies are written so that the security administrator knows what to configure, and end users know what part they play in keeping the company secure.
The management team will create policies that need to be adhered to by all employees, and these policies are created to help reduce the risk to the business and are mandatory; failure to carry out these policies is called policy violation and may lead to disciplinary action:
Policies: IT is immense, so if the management team says to the security administrators to go and set up IT security, the administrators would not know what to do, or where to start. Do they wish firewall rules to be set up, or permissions set on files?
If a policy was created so that Data Loss Prevention (DLP) templates were created to prevent Personally Identified Information (PII) or sensitive data being emailed out of the company, hen the Security Administrators would know exactly what to so.
The purpose of policies is to ensure that the security administrator knows what tasks they need to perform and also that end users know what their responsibilities are within each policy. Policies are an administrative control to help reduce risk.
Least privilege policy: This policy states that access to data should be restricted and that employees should be given the minimum access required so that they can perform their job. In the military, it is known as the need to know principle, where if you don't need to know it, then you have no access.
On-boarding policy: Companies allow employees to bring their own devices—Bring Your Own Device (BYOD)—to work, and part of the process is carrying out onboarding and offboarding. The on-boarding policy states that the device must be checked for viruses, and any application that could cause damage to the company's network should be removed before the device can be used to access the network. If someone brings their own device to work and fails to carry out the on-boarding properly, then the company could be infected by a virus.
Off-boarding policy: When someone leaves your company, then the business data used on BYOD devices needs to be removed before departure. If off-boarding is not carried out properly, an ex-employee could leave with company data on their device.
Acceptable Use Policy (AUP): The purpose of the AUP is to let the company employee or contractor know what they can do with company computers and BYOD devices. It lays out the practices on how you can access the company network and the internet. It will also state practices that are forbidden, such as participating in blogs and social media sites such as Facebook or Twitter while at work.
Remote access policy: A remote access policy may state that when a remote user is connecting to the company's network, they must use a secure VPN such as L2TP/IPSec. Policy violation would be trying to connect by another method and lead to data being compromised.
Auditing: The company employs an internal auditor to ensure that the employees carry out the policies and procedures written by the management team. The auditor does not have the authority to stop any processes, but they will report back to management. The outcome following an audit will result in change management or a policy being re-written.
Exam tip:
The auditor is the snitch: they won't ever stop a process, but they always inform the management of non-compliance to company policies. The outcome following an audit will result in either change management or a new policy being written.
Data-retention policy: For legal and compliance reasons, you may need to keep certain data for different periods of time; for example, some financial data needs to be retained for six years, whereas medical data may need to be kept for 20–30 years, depending on the type. A data-retention policy ensures that legal and compliance issues are addressed.
Change management: Policies, procedures, and processes are in place so that the company is running efficiently and the risk is being managed properly; however, when newer technology is introduced, some of the procedures and processes may change. It could be that an auditor has identified a process that needs to change, so they report that to the manager, who will then adopt change management.
Change management requests are sent to a Change Management Board (CMB). The board looks at the change request, what the financial implications are, and how changing one process affects other processes. If the change is really major, then a new policy could be written rather than just change management.
Example: New laptops are being purchased and configured for use within the company. The auditor is reviewing the process and finds that there is no anti-virus software being installed on these laptops; therefore, they report this back to management. Management then looks at the processes that are laid down for configuring new laptops and then uses change management to change the processes so that in future anti-virus software is installed before rolling them out to the rest of the company.
There are two main web servers used by commercial companies. Microsoft has a web server called the Internet Information Server, and its rival is Apache. Web servers provide web pages for the public to view, and, because they are in the public domain, they are a prime targets for hackers. To help reduce the risk, both Microsoft and Apache provide security guides to help security teams reduce their footprint, making them more secure:
Microsoft has created a user guide called basic security practices for web applications. This helps the security administrator protect web applications running on a web server, and this can be seen at the following URL:
https://msdn.microsoft.com/en-gb/library/zdh19h94.aspx
Apache has created and article called security tips that can be seen at https://httpd.apache.org/docs/2.4/misc/security_tips.html.
Web server security guides rely upon the latest updates being in place, services that are not required being turned off, and the operating systems to be hardened, to make them as secure as possible and reduce the risk of attack.
CISCO produce the best high-end network devices, and, because the networking world is ever evolving, CISCO has produced an infrastructure upgrade guide so that companies can use it as a best practice when upgrading their network device. It can be seen at https://www.cisco.com/c/m/en_us/solutions/enterprise-networks/infrastructure-upgrade-guide.html.
Security is critical for providing a safe working environment, and we now need to look at guidelines for vendor diversity, control diversity, technical controls, administrative controls, and the benefits of user training:
Vendor diversity: Companies need to be running 24/7, and therefore need to put in place vendor diversity. This may mean that they will get internet access from two different companies so that when one fails, the other can keep the company up and running. Vendor diversity provides both reliability and resiliency.
Examples: Firewalls are a mission critical network device that prevent unauthorized access to your network. In the Security+ exam, they tend to be used in a back-to-back configuration.
If we purchase the two firewalls from Vendor A, we may also have two firewalls from Vendor B with the same configuration kept in a secure area within your company. Should there be a failure with one of the firewalls or a vulnerability with the Vendor A firewall, then we can then quickly swap those with the firewalls from Vendor B. This ensures that the network remains secure at all times.
Control diversity: Control diversity goes back to the Depth in Defense Model, where many different controls are in place so that if one control fails, then the other control stops the attack.
Example: A firewall that protects our network against attacks and has been very successful in preventing attacks, but if a hacker manages to get through the firewall, then the control diversity installs a network Intrusion Detection System (IDS) that will alert the networks and security administrators about attacks inside the network.
Administrative controls: Administrative controls provide security to the company. An example of this would be to have an outside agency carry out a penetration test or a vulnerability scan. Rules for the penetration test would have to be established before the test, as you may want the penetration tester to exploit the vulnerability totally and see how far an attacker would have got, or maybe just inform you of the vulnerability. Another administrator control would be to carry out an internal audit.
User training: Most cyber security attacks happen because of mistakes being made by people, so an important step in keeping your company safe is to provide user training so that they are not vulnerable to malicious telephone calls and phishing emails, and annual training reminds them of their responsibilities.
One of the most critical areas in data security is the storing, accessing, and destroying of data when it is no longer required. In this section, we will look at the types, control, and destruction of data.
Data is controlled, handled, and stored based on its classification and privacy markings. Once this data has outlived its use, it needs to be destroyed so that it cannot be read by a third party. Data can be stored electronically on a computer's hard drive or kept as a hard copy by being printed. Most companies employ a third-party organization that specializes in data destruction and can provide a destruction certificate. Let's look at the different methods of destruction:
Burning: A company will have many burn bags that are normally paper-based and contain classified or sensitive information. These burns bags will be picked up periodically by a third party, who will place the data in the incinerator, where it will be burned. Burning is seen as more secure than shredding.
Shredding: There are three main paper shredders. The first is a strip-cuts shredder, where it shreds the data into strips, and they are pretty useless. The second type of shredder is a cross-cut one, where the paper is cut into small pieces. However, the best shredder is the micro-cut, which turns the data into confetti, and this is difficult to put back together. After paper has been shredded, it is not secure, as scanners can put it back together, so the next step is to pulp the shredding:

Destruction of hard drives can also be done by shredders that destroy the hard drive into smaller chunks. Take a look at the preceding photo, which shows the results of hard-drive shredding. Some hard-drive shredders can shred hard drives into much smaller chunks.
Pulping: After paper has been shredded into small pieces, the next step is to ensure that it cannot be re-constructed by pulping the data. You put the paper shreds into a container, and then pour water or sulfuric acid on them, to turn it into a sludge of cellulose fibers, making it impossible to reconstruct them.
Pulverizing: Pulverizing can be used for hard drives or optical media such as CD/DVD ROMs, where they are either hit by using a lump or sledge hammer, turning them into smaller pieces.
Degaussing: Degaussing is where a magnetic field is applied to a hard drive or tape drive in order to remove the data.
Purging data: Purging is the process of removing unwanted data from a database server such as a SQL server. Do not confuse it with deletion, which removes all of your data.
Wiping data: Wiping data is the process of removing data from a mobile device such as a smartphone. Most Mobile Device Management (MDM) systems can remote wipe the data when it is stolen to prevent access.
Cluster Tip Wiping: If you use an NTFS file system, data is stored in storage areas called clusters, and the default size of a cluster is 4 KB. If I have a file that is 11 KB in size, and the first two clusters are fully loaded with 8 KB of data, but the last cluster (which is called the cluster tip) has 3 KB of data and an area of 1 KB that has no data. Cluster tip wiping ensures that no data remnants are left behind in the 1 KB space.
Securing and handling data is a critical part of security, as companies spend so much money completing the Research and Development (R&D) of a product because they don't want their competitors to know about their new product until it goes on the market. It is very important that the data is labeled according to its classification. Military data in the UK army is classified as unclassified, restricted, confidential, secret, and top secret, whereas a civilian company may classify data as confidential, private, public, and proprietary.
The first stage of risk management is classification of the asset, which determines how we handle, access, store, and destroy the data:
Confidential data: Normally, R&D and legal data will be classified as confidential data; disclosure would cause damage to the company.
Private data: This data could be a list of products and the minimum sales price; we would not want customers to know this. It could also be sensitive data such as PII or Protected Health Information (PHI) data.
Public data: This is data that is available to anyone, such as yesterday's news, leaflets, or brochures that have been distributed everywhere. Anyone has access to this data.
Proprietary data: This is data generated by a company such as its trade secrets or the R&D department.
Personally Identifiable Information (PII): This is information that can identify a person, such as their date of birth, biometric information, or their social security number.
Protected Health Information (PHI): This is information stored in a person's medical records.
Privacy: Privacy law or data protection laws prohibit the disclosure or misuse of information about private individuals. In the United Kingdom, there is the Data Protection Act (1998) that protects the privacy of data.
Data is retained either for legal reasons or to be compliant with statute law, which could be either the length of time the data should be retained or the national boundaries that data must be stored within. Multinational companies cannot just simply move data between national boundaries, as compliance forbids it:
Legal hold: Legal hold is where either a litigation case is ongoing or the police are investigating an individual. Legal hold is normally done with mailboxes where the person has their mailbox placed on legal hold so that they can receive emails, reply back, but cannot delete any emails. This is to ensure that evidence is not destroyed.
Data compliance: There are different national laws about the retention, movement, storage, and disclosure of data to protect the individual. In the United Kingdom, most financial accounts data must be retained for at least six years; medical data can range from 20-30 years, depending on the type of data; and pension data must be retained indefinitely. Companies that are not data compliant within the country in which they operate could face a regulatory fine that goes into millions of pounds or dollars.
Everyone within a company will access data every day, but the company needs to control access to the data, and this is done by using data roles; we are now going to look at these roles:
Owner: Someone within a company needs to have overall control of the data, and this is normally the Chief Executive Officer (CEO) or the Chairman. The owner can be known as the information owner or steward and is responsible for making decisions on its protection.
Custodian: The data custodian is responsible for securing the data, backing it up, checking the data's integrity, and ensuring that the server holding the data has anti-virus software installed. They are responsible for ensuring that the data is made available, but they do not make critical decisions on the protection of the data, as that is made by the data owner.
Security administrator: The function of the security administrator is fulfilled by the IT team, and the team is responsible for ensuring that the least privilege policy is adhered to, as the team only gives access to the data to those who require it for their jobs.
Privacy officer: The data privacy officer is responsible for ensuring that access to the data is fulfilled according to the Legal and Compliance regulations.
In this practical, we will download the Microsoft Baseline Security Analyzer (MBSA) tool, and then we will run the tool to see what missing patches and vulnerabilities it may have. The Windows 10 desktop that this demo will be run on has only recently had the latest update (two days ago):
Go to Google and insert the latest MBSA download (the current link is https://www.microsoft.com/en-gb/download/details.aspx?id=75580; at the time of writing, this is MBSA 2.3):
Select the language that you require, and then press Download:
All Windows 10 and Windows 8 desktops use 64 bit; I have selected 64 bit with English as the language. Press Next. Allow popups, and then select Run:
Press Next:
Select I accept the license agreement, and press Next:
In the wizard, you can select the destination folder; select Next in the screen that follows, and select Install. During the installation, the UAC prompt will appear. Select Allow, and then the installation will be complete:
After the installation appears, there will be a shortcut on the desktop, as shown here:

Double-click the desktop icon; select Allow when the UAC prompt appears, and then the MBSA interface will appear:
From here, you can either scan a single computer or multiple computers; please select Scan a computer, and then press Start scan. At this stage, it downloads security update information from Microsoft, and this may take some time:
This then performs a scan, checking security update information from Microsoft.
The outcome of the scan will be similar to this:
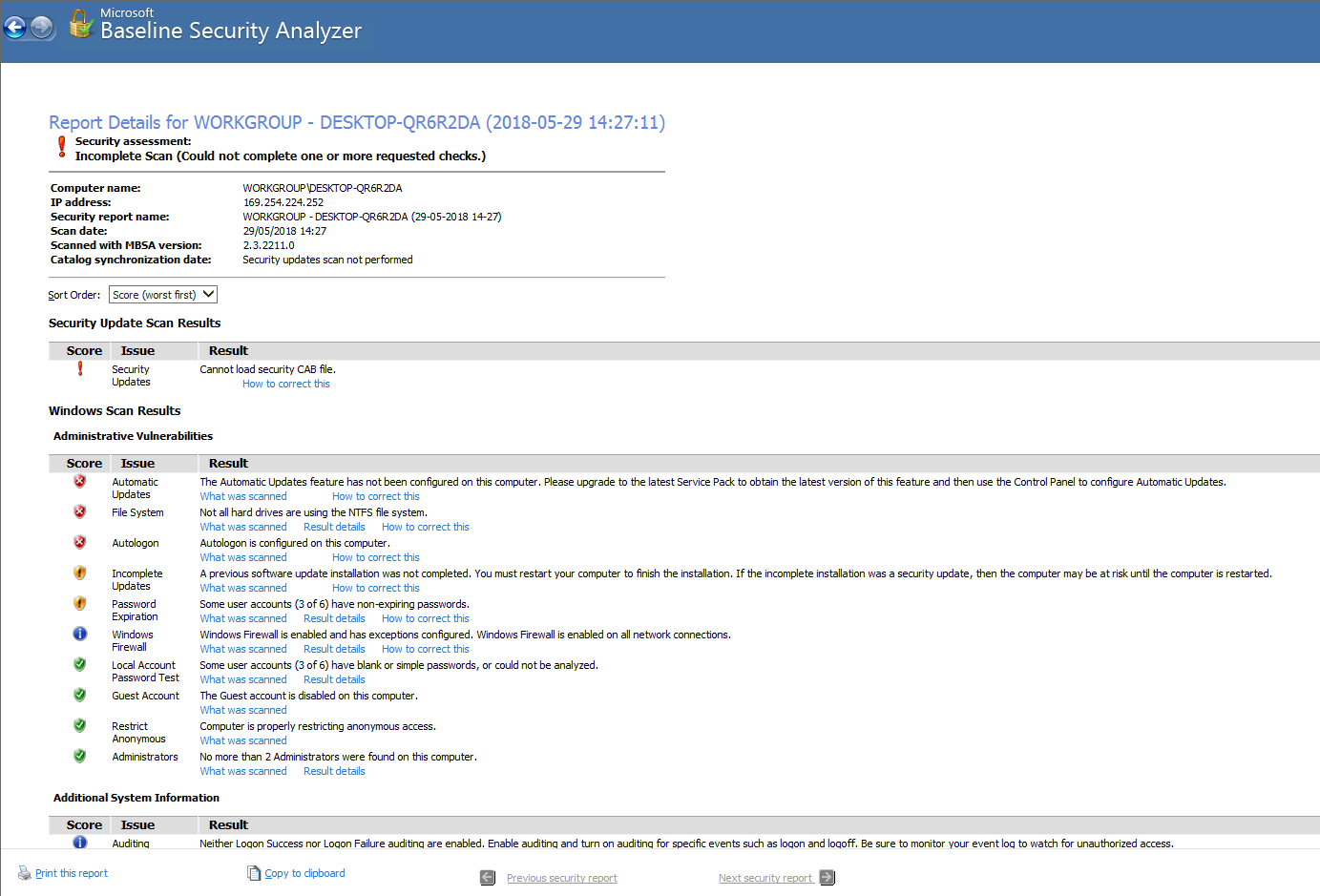
The default scan result shows the vulnerabilities in red; blue is informational, and green is for the items that are compliant. Where there are vulnerabilities in red, the MBSA has hyperlinks so that these items can be resolved and so the desktop can be made as secure as possible.
What is an industry standard framework?
What is the OSI reference model, and how many layers does it have?
What is the TCP/IP protocol, and where is it used?
Which layer of the OSI reference model does a switch operate?
Which layer of the OSI reference model does a router operate?
What is a regulatory framework, and is it legally enforceable?
What type of frameworks are ITIL and Cobol 5, and are they legally enforceable?
What three policies are used in a BYOD environment, and what purpose does each of them serve?
What would happen if I were in an internet café at an airport and did not connect to the company network using a VPN and the data was intercepted?
The FBI were investigating John Smith; therefore, the IT team placed his account on Legal Hold. John Smith decided to leave the company on February 12, and the IT team decided to delete his account on April 12, as nobody from the FBI had requested any evidence. On April 13, the FBI contacted the company asking for evidence. What policy could have ensured that the evidence was available for the FBI?
What is the purpose of auditing, what power does the auditor have, and what is the likely outcome after the audit?
What is the purpose of change management?
Why do vendors produce security guides?
What is the purpose of vendor diversity?
What is the purpose of control diversity?
What type of control are penetration test or vulnerability scans?
How do companies normally dispose of classified printed material?
What is best way of disposing of a hard drive?
What is the purpose of pulping, and when would it normally be carried out?
What is the purpose of degaussing, and when will it be carried out?
What is cluster tip wiping?
If the company held information marked Public and Private, why would we then introduce classifications such as confidential and proprietary?
Who is responsible for the securing and backing up of data?
Who is responsible for allowing access to the data?
What is the purpose of a privacy officer?
Industry standard frameworks are a set of criteria within an industry, relating to carrying out operations known as best practices. This is the best way that the operations should be set up and carried.
The Open Systems Interconnection model (OSI model) is a conceptual model that standardizes the communication functions of a telecommunications or computing system without regard to its internal structure and technology. It has seven layers—application, presentation, session, transport, network, data link, and physical; these are layers seven, down to layer one.
The TCP/IP protocol is the only protocol used in the internet, and most networks use it; each computer has an IP address to identify it.
A switch operates at layer 2: the data link layer. There is a multilayer switch that works at layer 3, but the exam focuses on a switch and VLAN operating at layer 2. A switch is an internal device.
A router whose function is to join networks together works at layer 3: the network layer. A router operates as an external device.
A regulatory framework is based on statute law and governmental regulations; is it legally enforceable?
ITIL and Cobol 5 are Non-Regulatory. These are not enforceable by law and are optional, but they provide a framework for companies to follow as a best practice for IT service management.
The three types of policies needed for a BYOD environment are on-boarding, off-boarding, and Acceptable User Policy (AUP). The on-boarding policy states what needs to be done before a device can be allowed access to the network, the AUP states how the device should be used and restricts access to games and social media. When the exam mentions a BYOD environment, think of on-boarding and AUPs. The off-boarding policies state how to decommission a device from your network.
Not using a VPN to connect to your network would be a policy violation against the remote access policy and would lead to disciplinary action being taken against the perpetrator.
A data retention policy stating that data should be kept for six months following a person leaving the company, or the data retention policy could state never delete data that has been placed on Legal Hold. Both of these would ensure that the FBI got its data.
The role of the auditor is to ensure that the company's policies and processes are being carried out, following an audit—either change management or the creation of a new policy are the likely outcomes.
Change management regulates changes within a company so that they are controlled and risk is managed effectively. This stop employees doing their own thing.
Vendors produce security guides so that their products can be set up by their best practices, making them as secure as possible.
Vendor diversity provides reliability and resiliency by having more than one solution in place; should one solution fail, then the company is still up and running. Business continuity is covered later in this book.
Should one control fail, then another is in place; an example of this is if an attacker gets over the perimeter fence, then a guard with a guard dog would stop them going any further.
Penetration test or vulnerability scans are administrative controls; the vulnerability scan is less intrusive.
Classified printed document are normally put in burn bags that are collected by a third-party agency, who then incinerates them and provides the company with a destruction certificate.
The best way to destroy a hard drive would be to shred it. Pulverizing is an alternative, but it is not as effective.
Pulping can turn shredded paper into a sludge by using water or sulfuric acid. Try and read it now!
Degaussing is where a magnetic field is applied to a hard drive, or a tape drive, to remove the data.
Cluster tip wiping is removing the last remnants of data stored in the last data cluster.
By having four classifications rather than two classifications, it can lead to better classifications of the data.
The custodian is responsible for securing and backing up data.
The security administrator is responsible for granting access to the data. Remember: this is not the owner.
The privacy officer is concerned with who is accessing the data and how is it shared; for example: are only doctors able to see a patient's medical history?