How To Conduct A Security
Risk Assessment
Learn how PurpleSec’s experts can help assess your organization’s cyber security risk.

Learn how PurpleSec’s experts can help assess your organization’s cyber security risk.
Author: Josh Allen / Last Updated: 5/21/22
Reviewed by: Michael Swanagan, CISSP, CISA, CISM, Seth Kimmel, OSCP & Rich Selvidge, CISSP
View our: Editorial Process
There are 8 steps to conducting a security risk assessment including mapping your assets, identifying security threats and vulnerabilities, determining and prioritizing risks, analyzing and developing security controls, documenting results, creating a remediation plan, implementing recommendations, and evaluating effectiveness.
What You’ll Learn
The pandemic gave threat actors many new opportunities to try and infiltrate company networks and cloud systems.
As more employees moved to remote working arrangements, businesses had to quickly bring new systems online to support their remote employees.
The size of attack surfaces increased rapidly, and, given the substantial talent gap for cyber security professionals, companies struggled to keep up.
The resulting increase in the number of cyber attacks was staggering.
Phishing schemes proliferated, with threat actors preying on people looking for vaccine information and updates on government support payments.
Ransomware attacks exploded, with several high-profile attacks, including Colonial Pipeline, the Kaseya data breach, JBS Meats, SolarWinds, and Accellion to name a few.
With threat actors becoming ever more sophisticated and ever more tireless in their efforts, companies need to take the time and review the security of their current systems.
An important step all businesses must take is conducting a security risk assessment.
A security risk assessment identifies, evaluates, and prioritizes potential vulnerabilities to various information assets (i.e., systems, hardware, applications, and data) and then prioritizes the various risks that could affect those vulnerabilities.
The primary purpose of a risk assessment is to inform decision-makers about vulnerabilities in corporate systems, allowing them to take preemptive defensive actions and prepare effective risk responses.
The assessment also provides an executive summary to help executives make informed decisions about ongoing security efforts.
Security risk assessments also indicate to management areas where employees need training to help minimize attack surfaces.
While it may seem that these concepts are self-explanatory, it is important for executives and management to understand their differences.
A risk assessment is primarily proactive.
It involves testing your current infrastructure and identifying weaknesses and vulnerabilities.
Risk assessment is an important prerequisite for effective risk management.
Risk management can be proactive or reactive.
The primary goal of risk management is to reduce risk by continuously applying best practices.
Risk management includes a wide range of activities from managing and updating infrastructure to applying identity management policies to training employees on proper password hygiene.
Unfortunately, even with strong risk assessment and proactive risk management, some attacks are likely to succeed.
Reactive risk management focuses on minimizing the damage of these successful exploits and facilitating rapid recovery.
Think about a healthcare organization working to distribute COVID vaccines.
As part of their work, they are collecting massive amounts of patient information that is subject to the HIPAA Security and Privacy Rules.
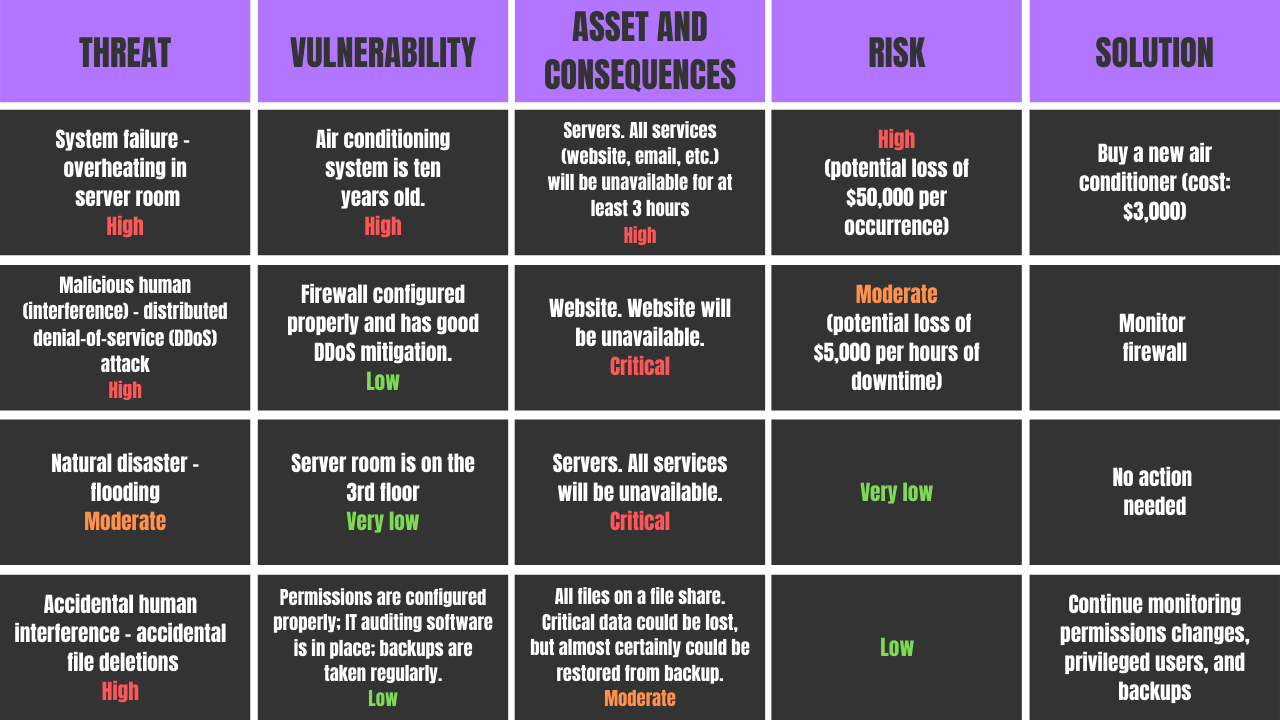
How can this organization ensure their security efforts are HIPAA-compliant? A HIPAA security risk assessment will identify areas of vulnerability and set the stage for implementing controls and remediation procedures.
The chart below is an example of issues identified in a HIPAA risk assessment, from physical vulnerabilities to firewall configuration issues.
A more basic and comprehensive security risk assessment any organization can consider, regardless of its industry, is compliance with the Center for Internet Security Critical Security Controls for Effective Cyber Defense (CIS Top 18).
The Top 18 are CSCs (Critical Security Controls) that companies should utilize to block or mitigate known attacks.
Another compliance standard that can serve as the basis for a security risk assessment is ISO/IEC 27001, an international standard on information security management.
ISO/IEC 27001 details processes for assessing, controlling and mitigating security risks.
There are many other standards that companies should know and address, many of which are specific to particular industries.
For example, government contracts must comply with NIST 800-171, while e-commerce businesses should have PCI-DSS-compliant payment systems.
How PurpleSec Helps To Secure Your Organization
Our vulnerability management services and penetration testing services provide a holistic approach to securing what’s most important to you.
The answer is simple. Successful attacks can cause substantial financial and reputational damage.
23% of small businesses suffered at least one cyber attack in 2020, with an average annual financial cost of over $25,000.
And this estimate is lower than many others.
But the initial financial costs of dealing with breaches are just one aspect of the damage.
Companies also can suffer lost clients, loss of reputation, loss of intellectual property, and increased insurance premiums, among other effects.
The costs of proactive risk assessments are minimal when compared to the damage of a successful attack. And the associated benefits more than offset those upfront costs.
Many companies are simply uninformed on even the basics of cybersecurity. More simply put, they don’t know what they don’t know.
Risk assessments help identify security gaps at all levels, from physical security to high-level malware detection and removal.
They also prevent spending unnecessary money by focusing on the top security controls and prioritizing security risks.
This goes far beyond comparing the cost of the assessment to the cost of a later breach. Risk assessments also show companies how to prioritize their security spend to minimize long-term costs.
Just take a look at the HIPAA risk analysis chart again.
Many company executives would not think that A/C maintenance is a cyber security risk.
But a $3,000 investment in updating the air conditioner could save the company $10s of thousands down the road.
And the faster companies take action, the more cost-effective their efforts can be.
Indeed, the White House recently urged corporate executives to take immediate action to assess their systems and take all steps necessary to prevent cybercrime, ransomware attacks in particular.
To be effective, risk assessment reports must be actionable.
That is, they must contain specific recommendations for remediation activities.
Assessment reports must tell companies how to harden their systems by filling security gaps.
It is equally important that reports identify issues that appear problematic at first glance, but which are so unlikely that they require no action.
Security risk assessments set the baseline for a company’s ongoing cybersecurity efforts.
By prioritizing identified gaps, they help companies create detailed plans for corrective actions.
And with detailed plans in place, companies can then set realistic budgets for their IT and cyber security teams.
They can also take rapid steps to address staffing shortages, which can take time given the current cyber security talent gap.
Poor security practices among employees create significant vulnerabilities for businesses.
Building a corporate culture focused on cybersecurity is essential.
Risk assessments help identify areas where companies should provide employees training to mitigate future risk.
Unless employees know what they are doing wrong and why it is important to correct their actions, they will remain easy attack targets.
Comprehensive risk assessments cover a broad range of potential issues, from location security to infrastructure security to data security to the risks of employees misappropriating or damaging data or systems.
How easy it for people to get physical access to your systems?
Do you have security at the entrances to the building?
Do you log visitors?
Are there security cameras in sensitive locations?
Do you have biometric locks on your server room?
Physical security assessments, including physical penetration testing, evaluate the ease with which a malicious actor can gain physical access to your critical systems.
What is the state of your IT infrastructure? What network level security protocols do you have in place? How are you ensuring compliance with shared security responsibilities in cloud services?
IT security assessments investigate the overall health over your IT infrastructure and communications pathways.
They identify broad system vulnerabilities that are not specific to particular applications or data storage facilities, as well as misconfiguration issues that frequently leave companies open to attack.
Is company data subject to least privilege and/or zero trust access controls?
Do you use network segmentation to limit data access?
Do you have strong identity management processes?
Data security assessments consider the ease and breadth of access to corporate data.
They identify areas where companies should apply new controls to restrict access to data on an as needed basis.
Read More: 9 Data Security Strategies & Best Practices For 2022
Do company applications conform to security-by-design and privacy-by-design principles?
Have you performed white and black box testing of your applications?
Is application access subject to least privilege control?
Application security assessments consider application vulnerabilities at every level from the code itself to who has access to the applications.
They allow companies to strengthen their applications and limit access to that needed for employees to perform their jobs.
Many, if not most, attacks arise from insider threats. However, many companies do not realize that insider threats go beyond employees that are intentionally trying to steal information or damage systems.
First of all, insider threats are not limited to people. They can include unapproved hardware that is not subject to a BYOD policy. They can also include outdated hardware.
Insider threats also need be neither intentional nor malicious. Negligence and unintentional threats can cause just as much harm as intentional ones.
A perfect example is using “password” as your password.
An increasingly common insider threat that many companies do not recognize is the advanced persistent threat (APT).
APTs, which are often used by state-sponsored cybercriminals or corporate espionage professionals, are long-term, targeted network insertions.
Often, careless or uninformed employees are the attack vector for an APT, with phishing emails being one of the most common ways attackers get access to company networks.
Essentially, the APT remains undetected in company systems for so long that it becomes an insider.
There are various types of penetration testing to assist in each security assessment.
To answer this question, you must first determine your goals for the security assessment.
If you want to conduct a broad, general assessment of your organization’s security posture, then you should look to one of the more generic frameworks such as the CIS top 18.
CIS top 18 assessments are also useful for small and medium businesses and companies with limited security budgets.
More mature or well-funded companies may consider using ISO 27001 or NIST 800-171 as the basis for their security assessment efforts.
If the goal is compliance, then you are more likely to consider industry-specific requirements, such as the HIPAA assessment described above.
And how you move forward with the assessment may depend on where you fall within the groups that HIPAA applies to.
For instance, data processors may have different security considerations than healthcare clearing houses.
E-commerce businesses and other companies that accept online payments may want to conduct assessments focused on their compliance with the Payment Card Industry Data Security Standard (PCI-DSS).
The ability to offer secure payment systems is essential to online business.
But once again, your needs will vary depending on whether you are a data holder, a data processor or both.
Defense contractor or government supplier?
Then you need to have Cybersecurity Maturity Model Certification (CMMC).
CMMC requirements are similar to NIST 800-171, although there is third-party auditing and certification rather than self-certification.
Even if your industry has no specific cyber security requirements, you should consider becoming compliant with some of the standards set out above.
How PurpleSec Helps To Secure Your Organization
Our vulnerability management services and penetration testing services provide a holistic approach to securing what’s most important to you.
Security risk assessments involve a detailed and iterative process.
Your security assessment plan begins with understanding exactly what resources your organization has.
Once you have built a thorough and complete inventory, you can begin to identify each resource’s vulnerabilities and implement appropriate security measures to rectify the vulnerabilities or protect them against exploits.
 Without a thorough understanding of your organization’s assets, security efforts will always be lacking.
Without a thorough understanding of your organization’s assets, security efforts will always be lacking.
Therefore, the first step in any effective security risk assessment is to generate a complete map of potentially vulnerable assets.
Asset maps require more than identifying hardware in use.
You must also include all applications, all users (whether human or processes) and all data storage containers because each of these contributes to your overall attack surface.
You should log and track each asset in a centralized database that you can quickly and easily update.
For users, you need to have a centralized system for assigning and managing all users and their respective permissions, for instance, an Active Directory system.
After completing your asset inventory, you should assign each asset a value and map data flows among your various resources.
Building data flow diagrams allows you to understand better where weak points and vulnerabilities exist in your network.
As part of assigning value to your assets, you should categorize your data by access levels.
Example categories include:
Data flow analyses should include what data is stored where and which users have access to what data.
User is a generic term that can include any person, program or process with access to corporate data storage.
In addition to identifying all internal assets, you must also identify and track connections to and data sharing with third-party providers, whether infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS), software-as-a-service (SaaS), or other type of service provider.
Third-party data flow assessments are particularly important for compliance with worldwide data privacy laws and regulations.
Building data flow maps, whether internal or with third-party providers, requires that you know:
 Having built your asset inventory, you can now begin to identify vulnerabilities and threats for each asset.
Having built your asset inventory, you can now begin to identify vulnerabilities and threats for each asset.
There are many tests and risk assessment software tools available to help you in this process.
For example, vulnerability scanning investigates your network and applications to identify susceptibility to known threats.
Having scan results categorized by severity allows your security team to prioritize remediation efforts.
Security gap analyses compare your current state of security readiness to established standards, such as CIS Top 18, CMMC or PCI/DSS. These analyses help you identify administration and configuration risks.
Penetration testing takes vulnerability and threat assessment to the next level.
By replicating actual attacks on your systems, pen testing can both validate the results of your vulnerability scans and security gap analyses and pinpoint previously unidentified vulnerabilities.
Pen testing also tells you more than whether a vulnerability exists and can be exploited.
It lets you assess how difficult it is to access your systems, as well as the scope of access and potential damage from a successful attack.
You will calculate a risk rating for each vulnerability that indicates the likelihood and impact of an exploit.
For known vulnerabilities, public information will give you a good sense of how easy it is to exploit the vulnerability, including whether there are already public tools designed to exploit the vulnerability.
For other vulnerabilities, pen testing can help you determine the likelihood of an exploit.
You also want to assess the potential impacts for each vulnerability:
Coupled with your categorization of data and asset valuations, vulnerability testing allows you to assess the likelihood that attacks will compromise high-value targets, as well as your potential liability if they are.
 Vulnerability and security threat assessments will invariably identify more risks than you can address at once.
Vulnerability and security threat assessments will invariably identify more risks than you can address at once.
Therefore, when following your risk assessment procedures, your next step is to prioritize risks by giving each vulnerability a risk rating so that you can prepare your remediation plans.
Prioritizing your remediation responses involves assessing your overall remediation budget against the risks and impacts of each threat or vulnerability.
For example, you may decide to prioritize vulnerabilities that affect medium-value assets if the likelihood of exploit and damage potential is much more significant than for higher-value assets.
Costing remediation efforts should include the costs of employees allocated to security efforts.
For example, you can expect to pay a back-end developer with IT security training roughly $80 an hour in the United States.
If you divert them from their everyday tasks to address risk remediation, this involves an additional cost for the company.
You should continuously update your risk prioritization and calculate the associated remediation costs on an annual basis.
 For any given vulnerability, there are several types of security controls you may consider.
For any given vulnerability, there are several types of security controls you may consider.
The primary security controls are:
Each of these controls can be further divided by function, that is, by whether they detect, prevent/deter, correct or compensate for threats and vulnerabilities.
Once you determine the appropriate controls for each vulnerability, you can then develop specific remediation plans.
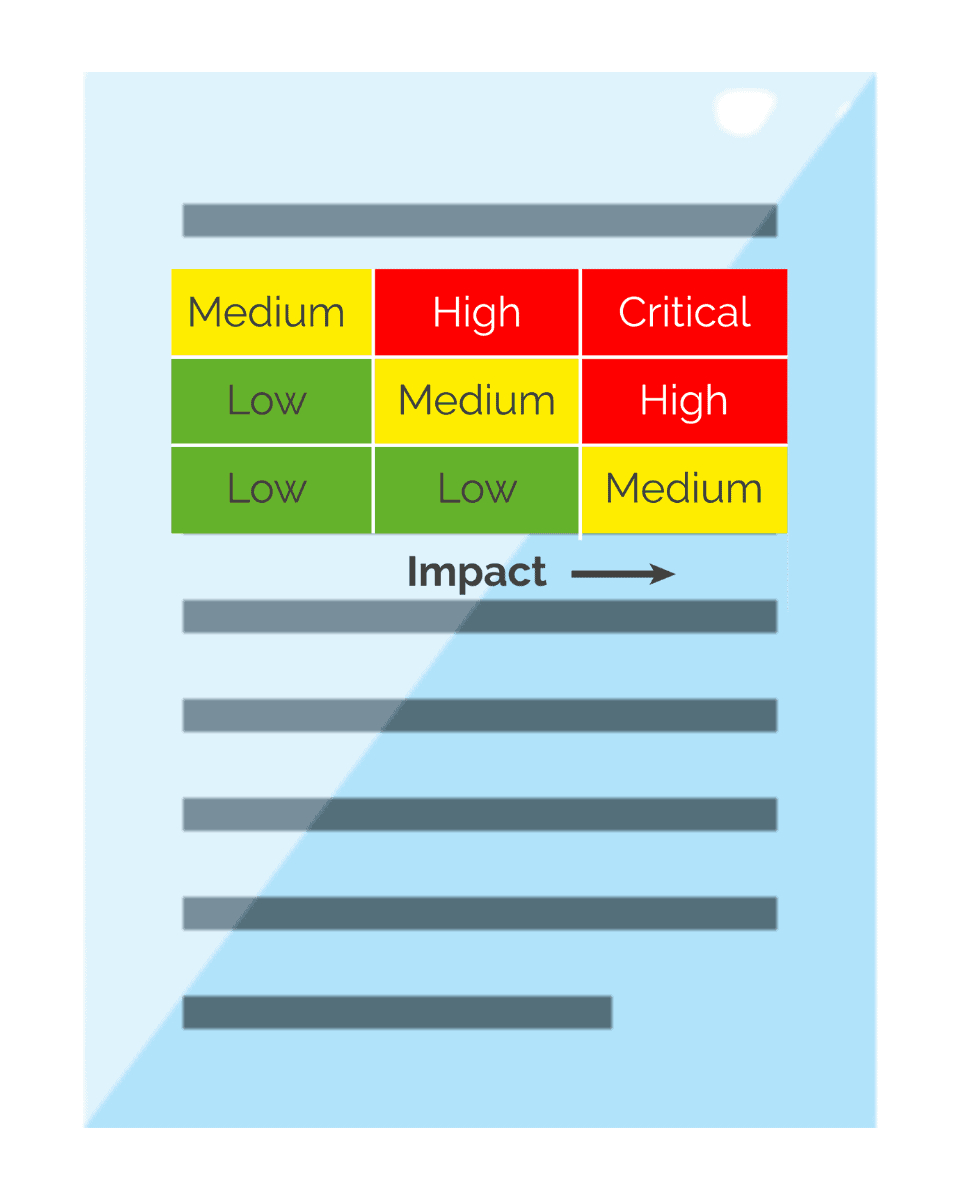 Effective risk assessment reports will condense the results of the various threat and vulnerability assessments in a concise threat ranking that show you a visual prioritization of your remediation plan.
Effective risk assessment reports will condense the results of the various threat and vulnerability assessments in a concise threat ranking that show you a visual prioritization of your remediation plan.
One effective way to represent your risk prioritization is using risk analysis templates, for example, a risk matrix.
The risk matrix compares various levels of likelihood of exploitation against the severity of the damage from a successful attack.
As the likelihood of exploitation and value of attack increase, vulnerabilities increase in priority and move higher in the remediation plan.
Now that you have determined risk ratings and the order in which you will address vulnerabilities, you can begin creating your detailed vulnerability remediation plan.
This should include the basic, high-level steps for each remediation process and the associated costs.
If you still have several options for a given vulnerability, you should perform a cost/benefit analysis.
Comparing the cost of remediation against the potential cost of a successful attack can assist you in narrowing down to your preferred control.
Costs are not limited to monetary expenditures; they can also include the time it takes to implement a solution and the disruption to the business.
For example, applying software patches may have little overall cost for an organization, but it can be disruptive if done during business hours.
 It’s finally time for action.
It’s finally time for action.
Your security team should now assign each item in the remediation plan to the appropriate team.
Assignments should include realistic time frames for completion.
In addition, you should indicate steps that teams should take to monitor the effectiveness of their remediation efforts, as well as any necessary reporting workflows.
As part of your remediation efforts, you should consider proactive risk responses such as Managed Detection and Response (MDR) solutions or Security Information and Event Management (SIEM) solutions.
Your choice among proactive risk response solutions may depend on whether you want to keep your efforts internal (SIEM) or whether you want to rely on external providers (MDR).
Experienced external providers can also help you build your SIEM processes, even if you control them internally.

Risk assessments are never static processes.
They require ongoing monitoring and optimization. As the old saying goes, rinse and repeat.
Internal audits are one way to evaluate whether remediation efforts are working.
You can also repeat your risk evaluations and gap analyses to verify that your actions have improved your security posture.
Another very effective test of remediation efforts is the so-called “Blue Team” exercise.
Blue Team is your internal defensive group responsible for performing security threat assessment, creating and implementing remediation plans and managing incident response.
In contrast, Red Team represents attack vectors, for example, by conducting penetration testing.
Blue Team exercises are widely varied and can include anything from performing domain name server audits to tracking individual user activity to identify anomalous actions to putting firewalls and anti-virus programs in place.
Blue Teams should also police compliance with company security policies.
As with all business processes, once you identify a flaw or fault, you must correct it and restart the process.
Constantly updating your risk analyses and improving your remediation plan is the best way to make sure you are well-protected against threats.
To get the most out of your security risk assessments, you should be aware of the most common errors organizations make when conducting them.
If you understand the process and its structure, you will easily avoid these problems.
Every second you lose in placing proper controls and remediation plans in effect exposes you to attacks, breaches, and potential liability and costs.
Frequently, organizations think security risk assessments focus only on electronic assets and resources.
Do not neglect to consider issues such as physical threats and human risks.
The reasons you are conducting a risk assessment help you properly allocate manpower and financial resources to the assessment.
Keeping within scope is also more cost-effective than doing broad-brush assessments with no specified end goal.
Do not assume you already know the risks and immediately start planning remediation.
Beginning with proper inventories and data flows is key to having effective remediation efforts.
While you will need to use tools to complete your assessments and implement remediation plans, you should not neglect the human factor.
Instead, rely on both your internal security experts and external providers to help you fully understand the results the tools generate.
And rely on your C-suite to build the necessary culture of cybersecurity, including training employees in basic cybersecurity practices that serve as the best foundation for ongoing security efforts.
Your efforts will not be successful if you run a risk assessment once, implement a remediation plan and then stop.
Threat actors are constantly evolving, and you need to update your assessments continually to keep pace with them.