Introduction to Django Permissions
Django itself has different features for the user; permission is one of the features provided by Django. Django has additional permissions such as add, delete and update permission to all the specified models. So users can perform the associated operations as per their requirements with the help of the admin portal. As well as, Django provides the facility to add permissions for our specified models and assign them to the selected users. While assigning permission, we need to consider authentication and authorization to assign at the user level as per our requirements.

Overview of Django Permissions
Django authentication is a client validation framework. It handles authentication, gatherings, authorizations, and treat-based client meetings. This documentation segment explains how the default execution figures out of the crate and how to stretch out and alter it to suit your venture’s necessities.
The Django verification framework handles both validation and approval. Momentarily, validation confirms that a client is who they guarantee to be, and authorization determines what a verified client is permitted to do. Here the term verification is utilized to allude to the two assignments.
The auth framework has the following points:
- Clients
- Permission: Binary (yes/no) here; Django uses the flag to determine whether the user has performed any action or not.
- Group: A conventional approach to applying permissions and consents to more than one client.
- A configurable secret key hashing framework.
- Structures and view devices for signing in clients or confining substance.
- A pluggable backend framework.
- Django’s confirmation framework is extremely nonexclusive and doesn’t give a few highlights regularly tracked down in web verification frameworks. Answers for a portion of these normal issues have been carried out in outsider bundles:
- Secret key strength checking.
- Choking of login endeavors.
- Validation against outsiders (OAuth, for instance).
- Object-level authorizations.
The validation framework is adaptable. You can develop your URLs, structures, perspectives, and layouts without any preparation, assuming you like, simply calling the given API to sign in to the client. In any case, in this article, we will utilize Django’s “stock.” Verification perspectives and structures for our login and logout pages. Well, in any case, you have to make a few layouts, yet at the same time, that is quite simple.
How to Use Django Permissions?
We know that Django provides authentication and authorization for security purposes, but usually, it is not sufficient to provide access rights. Authorization checks are constantly run at the beginning of the view before some other code is permitted to continue. Authorization checks will regularly utilize the verification data in the request.user and request.auth properties to decide whether the approaching solicitation ought to be allowed.
Authorizations are utilized to concede or prevent access for various classes from getting clients to multiple pieces of the API. The least complicated authorization style is to permit admittance to any verified client and deny admittance to an unauthenticated client. This compares to the IsAuthenticated class in the REST structure.
A somewhat less severe consent style permits full admittance to confirmed clients; however, it allows read-just admittance to unauthenticated clients. This compares to the IsAuthenticatedOrReadOnly class in the REST system.
Django Permissions Level
Let’s see different levels of permission in Django as follows:
1. User Level Permissions
At the user level, we can set different permissions or say that Django itself creates add, update, view, and delete permission to the developed models. Django provides permission in the below sequence as follows.
Code:
{Specified application name}.{Required permission access}_{Specified Model Name}Explanation:
- The first block is used in the above syntax to specify application names related to the model.
- Required permission access means which action we need to perform, and finally, we need to provide the model name.
2. Group Level Permission
Django provides the group-level permission functionality to the user, so first, we need to create a group of users, and we can assign permission to each group as per our requirements.
We require a group model with the following roles created a group model.
- Author: Using this role, we can view and add posts per our requirements.
- Editor: Using this role, we can view, edit and add posts per our requirements.
- Publisher: Using this role, we can view, edit, delete and add posts per our requirements.
3. Model Level Permission
Django provides the model-level permission functionality to the user through the model Meta options. In addition, Django allows flexibility to the user meaning whether the user requires permission.
4. Object Level Permission
If we are using the Django REST framework, then it provides object-level permission. It has different classes such as BasePermission, has_permission, and has_object_permission.
Django Permissions Setting
Now let’s see how we can set permission in Django as follows:
Django itself has the default permission that we can set globally as follows.
Code:
FRAMEWORK = {
'DEFAULT_PERMISSION_CLASSES': [
'rest_framework.permissions.IsAuthenticated',
]
}If not specified, we need to; then we can set it like below.
'DEFAULT_PERMISSION_CLASSES': [
'rest_framework.permissions.AllowAny',
]In the above point, we already see the different permission levels, and as per our requirement, we can set any level.
Example of Django Permissions
First, we need to create a virtual environment with the help of the below commands as follows.
Code:
mkdir sample_auth
cd sample_auth
python –m venv env
source env/bin/activate
pip install djangoWe can see the created application list in the setting file.
Code:
INSTALLED_APPS = [
'django.contrib.admin',
'django.contrib.auth',
'django.contrib.contenttypes',
'django.contrib.sessions',
'django.contrib.messages',
'django.contrib.staticfiles',
'sampleproject',
]If we want to set model-level permission, we must add the following code.
Code:
from django.db import models
class Student(models.Model):
studname = models.CharField(max_length=100)
city = models. CharField(max_length=100)
studname = models.Boolean(default=False)Now we can set custom permission as follows.
Code:
from django.db import models
class Student(models.Model):
studname = models.CharField(max_length=100)
city = models. CharField(max_length=100)
studname = models.Boolean(default=False)
class Meta:
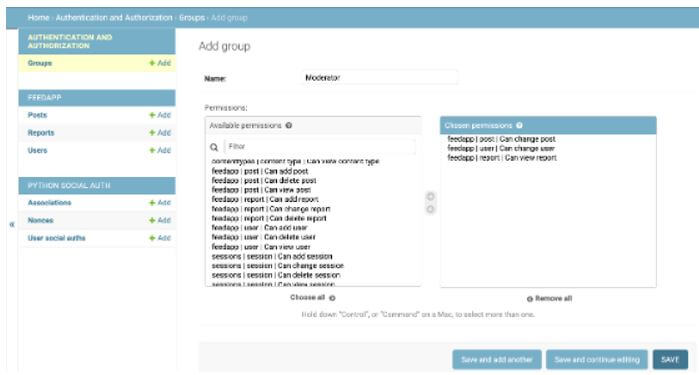
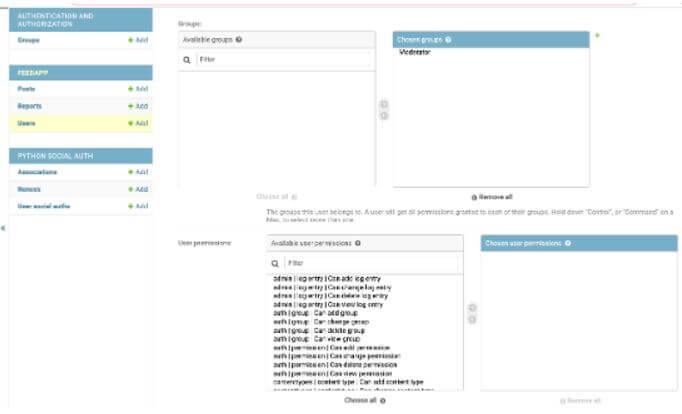
permission =[( "set_display_flag", "Check name is display or not",)]So in this way, we can set different permissions at the admin level. So first, we need to log in with the admin, as shown in the screenshot below.
Output:

The admin dashboard is shown in the below screenshot as follows.
Conclusion
With the help of the above article, we saw Django’s permission. From this article, we saw basic things about Django permission and the features and installation of Django permission, and how we use it in Django permission.

